Cyberspace does not exist in a vacuum. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers, communications networks and other critical infrastructure. These chips are becoming faster, cheaper and more powerful, and this has enabled the rise of artificial intelligence, the internet of things (IoT), and autonomous systems as key technologies of the future.
As the world becomes increasingly reliant on advanced technologies for economic growth and national security, implicit trust in hardware becomes an untenable option. Ultimately, hardware is the foundation for digital trust. A compromised physical component can undermine all additional layers of a system’s cybersecurity to devastating effect. Hardware security, therefore, focuses on protecting systems against the vulnerabilities at the physical layer of devices.
From our partners:
Hardware vulnerability
Hardware attacks take advantage of vulnerabilities in hardware-manufacturing supply chains. Modern chips are incredibly complex devices consisting of billions of transistor components that can be compromised during the processes of design, fabrication, and assembly and testing.
The complexity of integrated circuits and microelectronics makes hardware vulnerabilities difficult to detect. Physical modifications to a single integrated circuit can be well hidden among the sheer number of valid components and can function undetected for a long time. A well-designed hardware vulnerability could therefore go undetected until well after the malicious hardware has been widely incorporated into critical infrastructure.
What are the drivers changing global hardware security?
Recent global developments in industry, technology and geopolitics call for a greater focus on hardware security to ensure the continued health of our increasingly interconnected world.
Industrial trends
Globalization has transformed the semiconductor industry over the past few decades. Original equipment manufacturers have relocated their assembly plants and foundries to inexpensive geographic regions and have tapped into economies of scale by outsourcing manufacturing to dedicated suppliers.
The semiconductor industry has experienced a 90% contraction in the number of companies with leading-edge fabrication capabilities, with only three remaining companies (TSMC, Samsung and Intel) maintaining state-of-the-art foundries.
Technology trends
The growing expense of advanced semiconductor fabrication reflects the fact that technological growth in semiconductors has largely been driven by process innovation and advanced hardware architecture design. The primary semiconductor technology has not fundamentally changed since its invention in the 1960s. Rather, advanced manufacturing and innovative designs allow smaller semiconductor structures to be packed with increasing density to boost computational power.
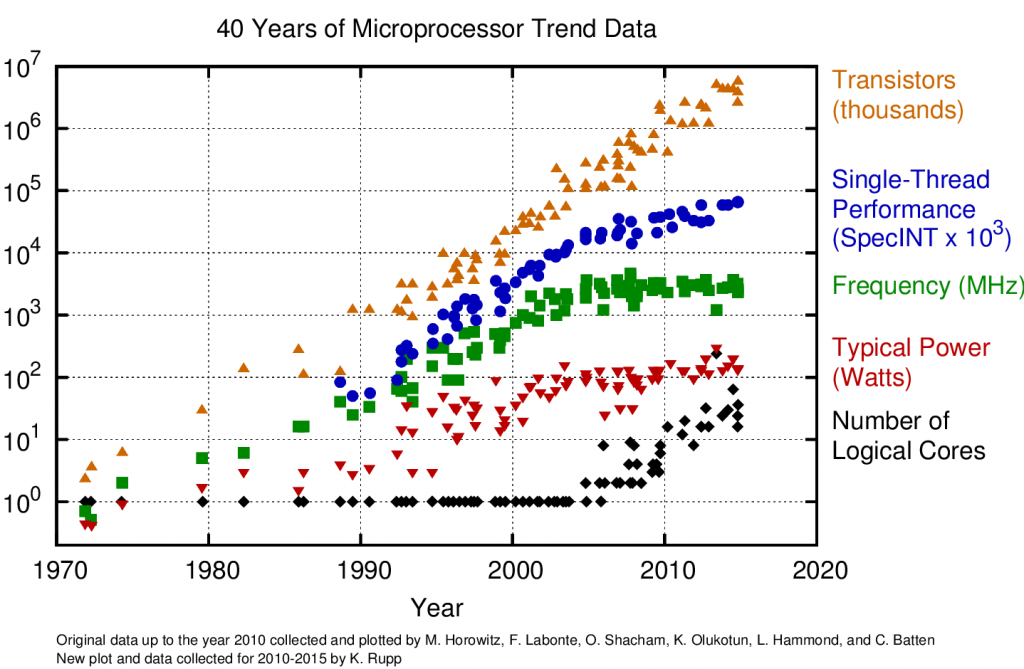
Reducing feature size has been so successful that the semiconductor industry is now facing a barrier in the underlying physics; further attempts at decreasing size will increasingly result in unwanted quantum mechanical effects.
Geopolitical trends
All nations and their economies are increasingly dependent on advanced semiconductor-based technologies for high-tech sectors and economic growth. This is reflected by the technological investments of well-resourced nations that seek to bolster their semiconductor manufacturing and innovation base by concentrating on developing critical technical expertise and production capabilities.
Component-manufacturing capabilities and the technical workforce have consequently been concentrated in a few countries around the world. This has lead to the current paradigm of haves and have-nots in semiconductor innovation and fabrication. Growing competition among the resourced nations to take the lead in semiconductor-manufacturing technology and innovation is ongoing, and impacts hardware security through changes in oversight and control of the supply chain. Nations without a semiconductor industry are exposed to geopolitical risks akin to those faced by commodity markets such as oil-dependence in the energy sector, and will have little influence over the security standards for hardware.
Achieving trusted hardware
Semiconductor technologies are essential to today’s economy and tomorrow’s prosperity. Consumers of microelectronics, from governments to corporations to individuals, purchase hardware with implicit trust, thereby exchanging security for capability. Ultimately, global cybersecurity requires diversified manufacturing sources of critical cyber infrastructure and future advances in hardware. Hardware manufacturers may also seek to ensure security and standards in their supply chain, and may be compelled to do so by governmental regulations.
Hardware security should be approached cooperatively by the private and public sectors. Both sectors have an important role to play in ensuring the safety and security of our digital infrastructure. This partnership should emulate well-established mechanisms in other engineering disciplines, such as civil or aeronautical engineering. The public sector sets standards and controls while the private sector designs, manufactures, builds and sustains. in the past, the global community has learned how to secure our physical infrastructure to safeguard our safety; now it is time to learn from that past and apply the same principles to secure our hardware.
The potential magnitude of impact of a successful hardware attack makes designing a comprehensive mitigation strategy imperative. Such an approach should seek not only to prevent a hardware vulnerability from occurring during the manufacturing stages, but also to enable systems to identify and respond to attacks as they take place. Prevention requires shoring up all stages of the manufacturing supply chain and developing thorough means of testing. Identification and response require designing integrated circuits with security features to detect, quarantine and shut down attacks as they occur. Success in achieving hardware security is possible only if the attacks are considered inevitable, not plausible, and are therefore pre-empted.
Written by
Edlyn V. Levine, PhD Research Associate, Department of Physics, Harvard University
Algirde Pipikaite, Project Lead, Governance and Policy, World Economic Forum
This article is republished from World Economic Forum.
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!