Many companies were forced to accelerate their digital transformation by rolling out new apps and services to help them adapt to the disruption caused by COVID-19. Kubernetes played a vital role to address this challenge as organizations around the globe focused on containerizing their applications in production. Although 84% of global security decision makers report that they have security policies in place for the use of containers, only 45% report that they have the right tooling in place to support those policies. While there are signs of progress, there is more we can and should do.1
Anthos Config Management (ACM) aims at solving this problem by providing administrators creating and enforcing consistent configurations and security policies across an organization’s fleet of clusters.
From our partners:
The focus of this article is Policy Controller, a feature of ACM based on the Open Policy Agent Gatekeeper project, that comes with a full library of pre-built policies for common security and compliance controls.
CIS Benchmark for Kubernetes
To help customers enhance the security posture of their workloads, the CIS organization has developed a guideline based on security objectives and community consensus which is called the Kubernetes CIS benchmark. Although the scope of the benchmark is fairly broad, this article focuses on the CIS policy bundle that is provided with the sample repository when configuring ACM.
The CIS policy bundle addresses and enforces policies in the following areas:
- RBAC and Service Accounts – restricting the use of cluster-admin role except for the
system:mastersgroup. Additionally, restricting the use of wildcard in Roles and ClusterRoles - Pod Security Policies – restricting the use of privileged containers, restricting admission containers wishing to share the host process ID, host IPC or host network namespace , restricting containers asking for
allowPrivilegeEscalation, restricting containers from running as root users and finally requiring containers to drop theNET_RAWcapability that can allow containers to exchange raw packets over ICMP. - Network Policies and CNI – requiring all namespaces to have a network policy defined.
- Secrets Management – prohibiting the use of secrets as environment variables and instead encouraging the use of mounted secret files in data volumes.
- General Policies – restricting deployment of resources in default namespace, requiring all pods to have
securityContextdefined and seccomp profile set todocker/default.
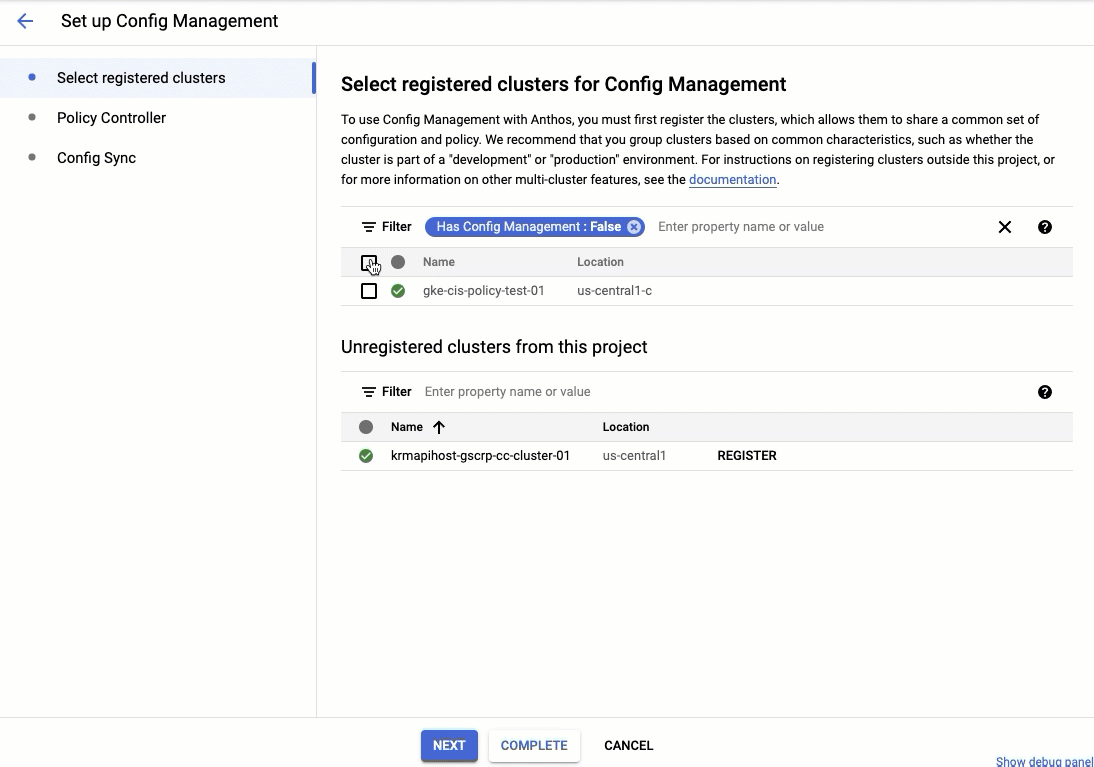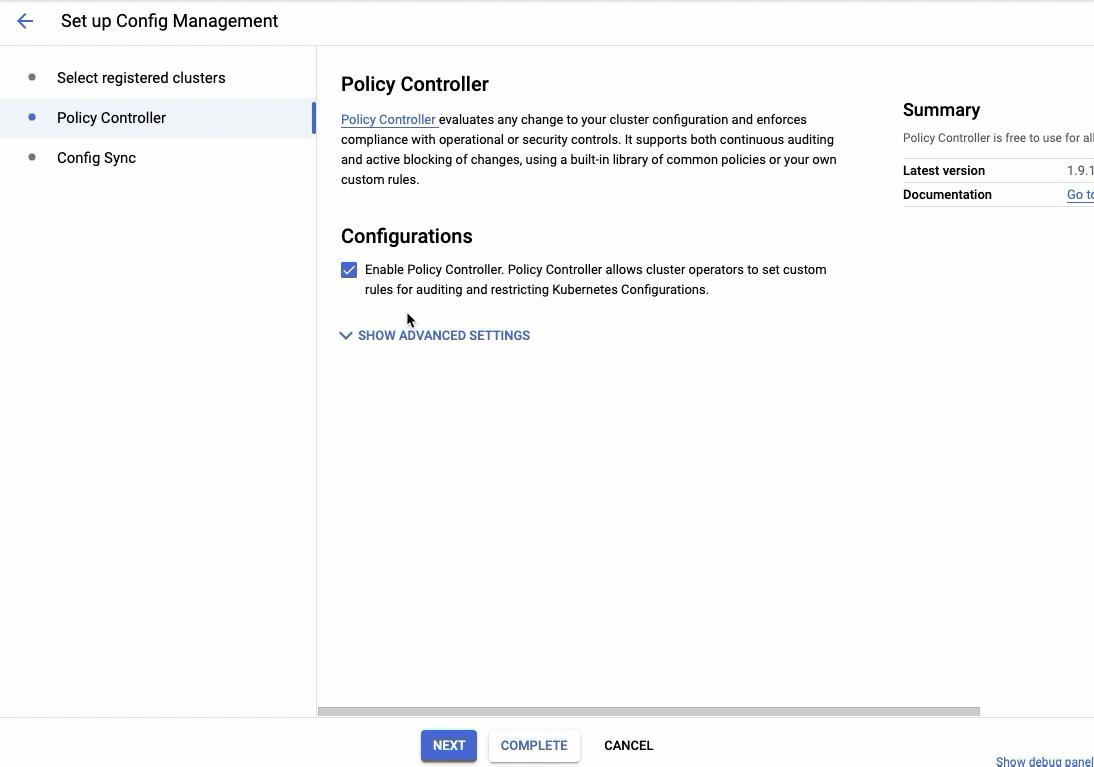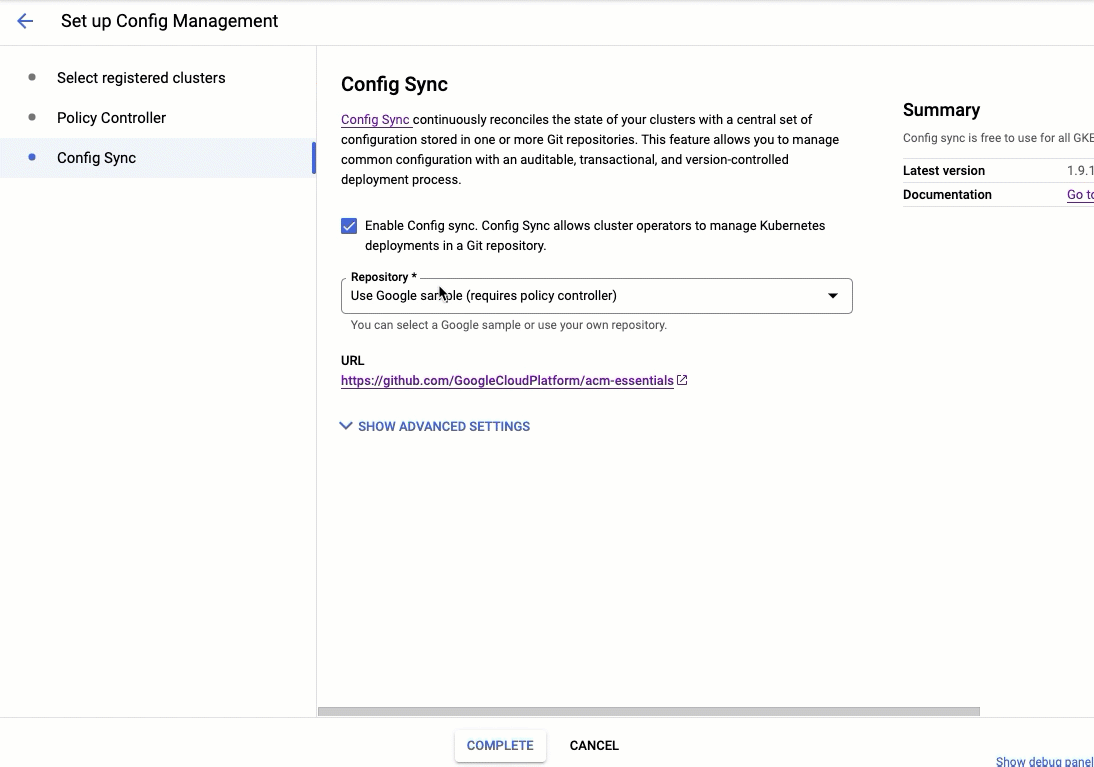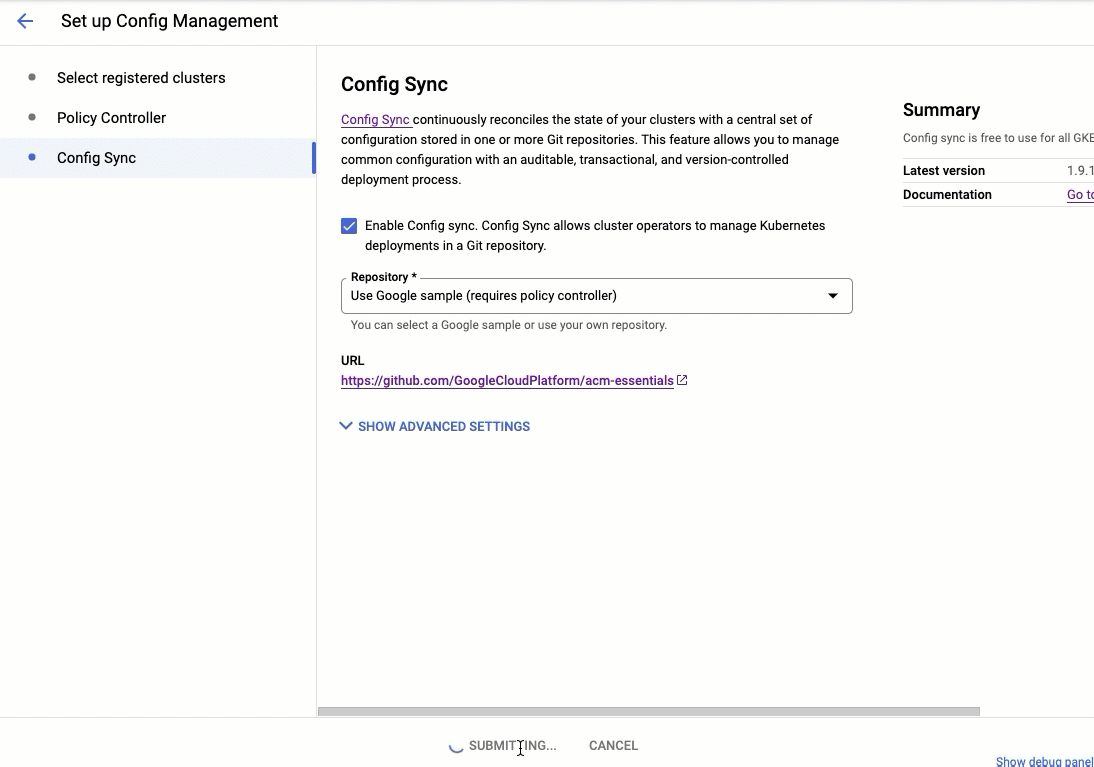
Conusuming the CIS Bundle via ACM UI
In addition to launching the CIS bundle, we have built a new UI for ACM which allows you to get started with minimal configurations. In particular, setting up ACM will now include installing Policy Controller by default and setting up Config Sync to pull from an essential baseline repository.
This essentials repository is in unstructured mode, which gives you the freedom to fork it and organize resources as you see fit. Out of the box, it applies the CIS benchmark to all clusters and namespaces.
Monitoring your cluster(s) for violations
The CIS policy bundle by default has its enforcement action set to dryrun which is the configuration for Policy Controller to show you violations without blocking or aborting any resources. This gives you the ability to audit your clusters, share any violations with workload owners and collaborate on fixing critical security issues.
All policy violations are automatically recorded in Cloud Logging and can be found by applying these filters in the Logs Explorer:
resource.type="k8s_container"resource.labels.location=CLUSTER_LOCATIONresource.labels.namespace_name="gatekeeper-system"resource.labels.pod_name:"gatekeeper-audit-"jsonPayload.process: "audit"jsonPayload.event_type: "violation_audited"jsonPayload.constraint_name:*jsonPayload.constraint_namespace:*
You can also use Cloud Monitoring to set up alerts for whenever policy violations occur.
Once you’ve had the chance to review all violations and are ready to turn on the enforcement of policies by blocking any non-compliant resources, you should change the enforcement action on each constraint to deny. This can be done in bulk by using the set-enforcement-action kpt function.
Conclusion
The need for monitoring and neutralizing security threats is growing and will continue to grow as we innovate with modern and distributed application development platforms such as Kubernetes. Without proper governance and tools in place, this growth can easily become an overhead for IT organizations. Anthos Config Management can help bring structure to this by providing central control over policies and traceability using Git. Explore Anthos Config Management best practices, quickstarts, and tutorials here. We also encourage you to try out the CIS policy bundle that is provided with the sample repository when you are configuring using Anthos Config Management.
1. Best Practices For Container Security, Forrester, July 2020
By: Awais Malik (Solutions Architect, Anthos)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!