As organizations move to the cloud, VM-based architectures continue to make up a significant portion of compute-centric workloads. To help ensure strong protection for these deployments, we are thrilled to announce a public preview of our newest layer of threat detection in Security Command Center (SCC): Virtual Machine Threat Detection (VMTD). VMTD is a first-to-market detection capability from a major cloud provider that provides agentless memory scanning to help detect threats like cryptomining malware inside your virtual machines running in Google Cloud.
The economy of scale enabled by the cloud can help fundamentally change the way security is executed for any business operating in today’s threat landscape. As more companies adopt cloud technologies, security solutions built into cloud platforms help address emerging threats for more and more organizations. For example, in the latest Google Cybersecurity Action Team Threat Horizons Report, we saw 86% of compromised cloud instances were used to perform cryptocurrency mining. VMTD is one of the ways we protect our Google Cloud Platform customers against growing attacks like coin mining, data exfiltration, and ransomware.
From our partners:
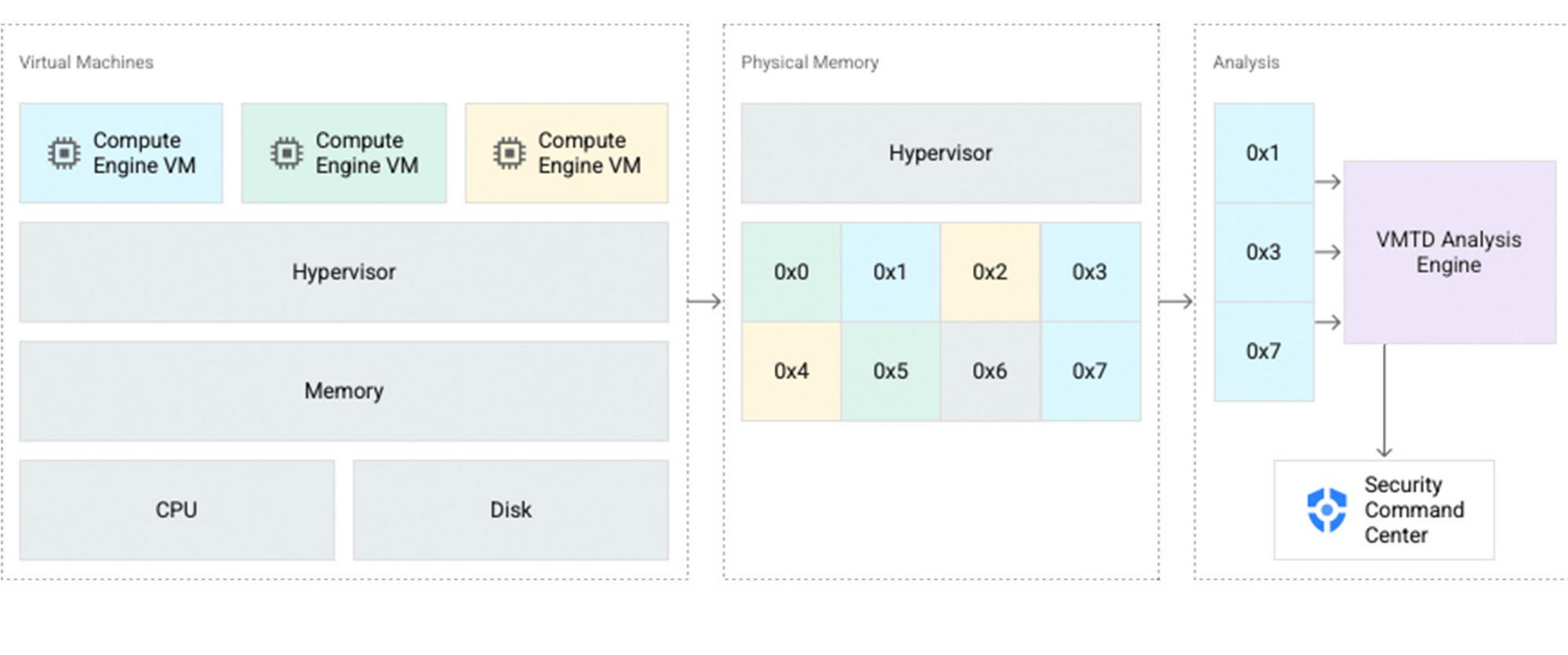
Our unique approach with agentless VM threat detection
Traditional endpoint security relies on deploying software agents inside a guest virtual machine to gather signals and telemetry to inform runtime threat detection. But as is the case in many other areas of infrastructure security, cloud technology offers the ability to rethink existing models. For Compute Engine, we wanted to see if we could collect signals to aid in threat detection without requiring our customers to run additional software. Not running an agent inside of their instance means less performance impact, lowered operational burden for agent deployment and management, and exposing less attack surface to potential adversaries.
What we learned is that we could instrument the hypervisor — the software that runs underneath and orchestrates our customers’ virtual machines — to include nearly universal and hard-to-tamper-with threat detection.
Getting Started with Virtual Machine Threat Detection (VMTD)
We’re excited about the kinds of detection that are possible with VMTD. During our public preview, VMTD detects cryptomining attacks. Over the next months as we move VMTD towards general availability, you can expect to see a steady release of new detective capabilities and integrations with other parts of Google Cloud.
To get started with VMTD, open the Settings page in Security Command Center. Click on “MANAGE SETTINGS” under Virtual Machine Threat Detection. You can then select a scope for VMTD. To confirm that VMTD is working for your environment, you can download and execute this test binary that simulates cryptomining activity.
Safeguarding customer trust
We know safeguarding users’ trust in Google Cloud is as important as securing their workloads. We are taking several steps to ensure the ways in which VMTD inspects workloads for potential threats preserves trust:
- First, we are introducing VMTD’s public preview as an opt-in service for our Security Command Center Premium customers.
- Additionally, not only does Confidential Computing provide encryption for memory as it moves out of a CPU to RAM, we never process memory in VMTD from Confidential nodes.
Comprehensive threat detection with SCC Premium
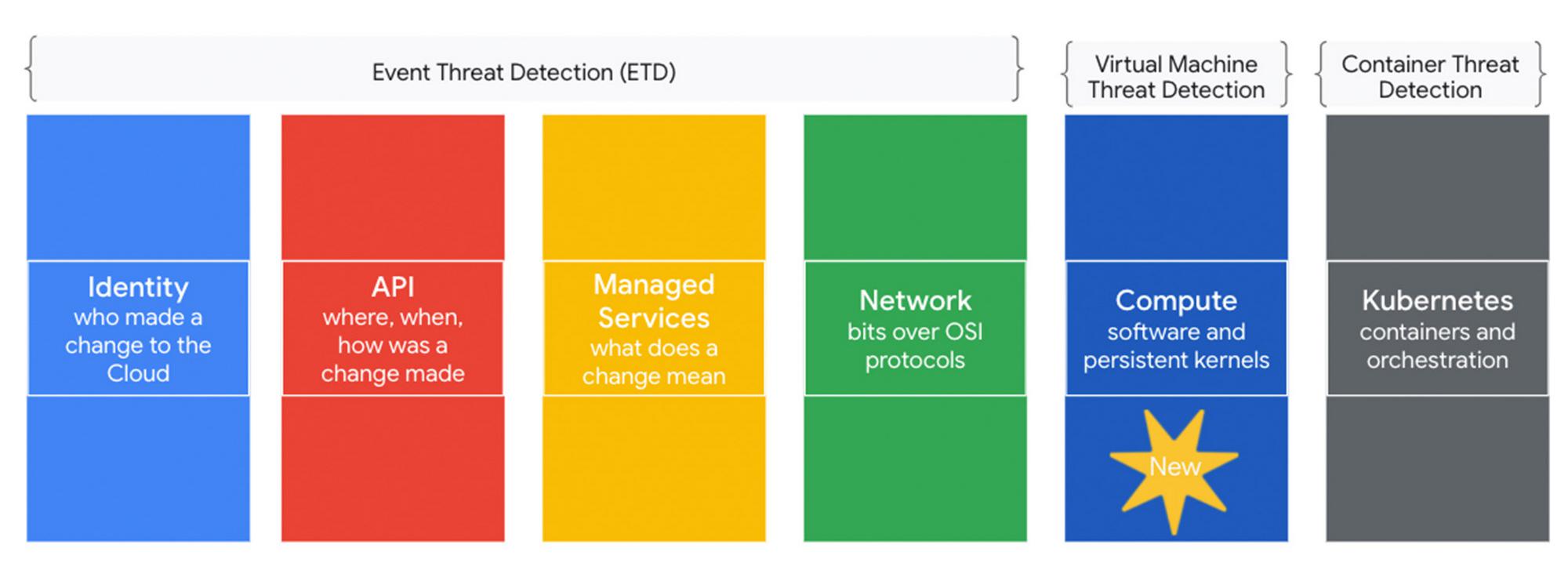
Virtual Machine Threat Detection is fully integrated and available through Security Command Center Premium. VMTD complements the existing threat detection capabilities enabled by the Event Threat Detection and Container Threat Detection built-in services in SCC Premium. Together, these three layers of advanced defense provide holistic protection for workloads running in Google Cloud:
In addition to threat detection, the premium version of Security Command Center is a comprehensive security and risk management platform for Google Cloud. It provides built-in services that enable you to gain visibility into your cloud assets, discover misconfigurations and vulnerabilities in your resources, and help maintain compliance based on industry standards and benchmarks.
To enable a Security Command Center Premium subscription, contact your Google Cloud Platform sales team. You can learn more about all these new capabilities in SCC in our product documentation.
By: Timothy Peacock (Product Manager)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!