With today’s rapidly escalating threat landscape, it is important that our customers have access to relevant context across their entire IT stack, whether it’s in the cloud, on-premise, or a combination of both, while responding to malicious threats. An alert in isolation does not provide sufficient information – associated metadata, context, and asset information is fundamental to an effective threat response strategy. Additionally, with prevalent alert fatigue, security teams lack the ability to prioritize which critical threats to address first.
In order to alleviate these challenges, we are thrilled to announce the public preview of context-aware detections in Google Chronicle. With this release, we are creating efficiencies in every step of a customer’s detection and response journey, starting by making alerts more functionally enabled.
From our partners:
Why context matters
To see why context is so important, consider the following example scenario: When a security analyst receives a detection alert for a suspicious Excel macro, the normal analyst path to respond would be to: 1) do a host lookup; 2) see which user owns that host; 3) do an LDAP lookup to identify the organization and responsibilities; 4) identify that the user belongs to accounting and payroll; and 5) identify they are likely to be using a macro in their financial spreadsheet. These steps allow the analyst to de-risk it contextually. However, if the same behavior was observed from the CEO’s machine with an unknown user logged in, it requires an immediate alert-escalation.
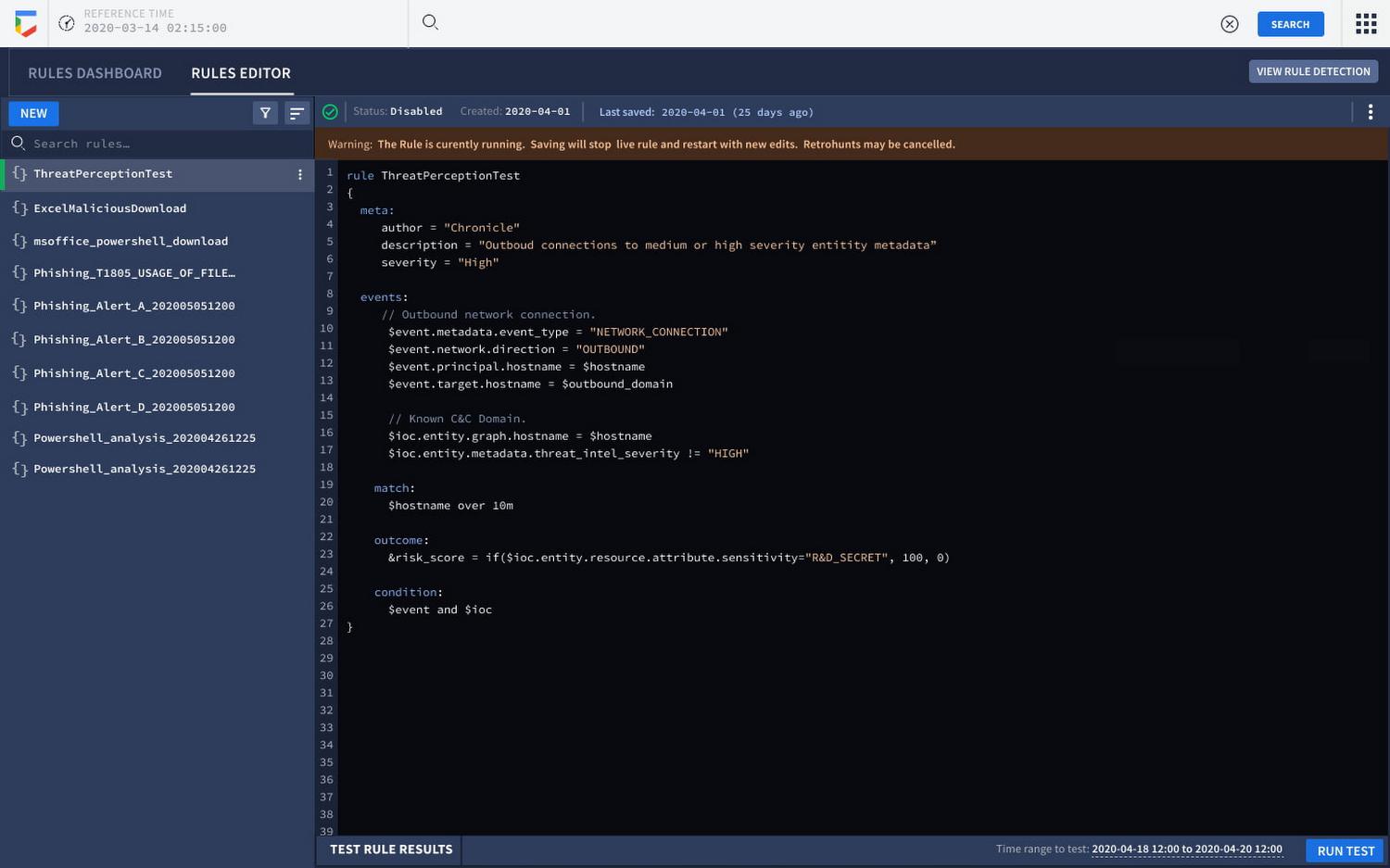
With context-aware detections in Google Chronicle, all the supporting information from authoritative sources (e.g. CMDB, IAM, and DLP) including telemetry, context, relationships, and vulnerabilities are available out of the box as a “single” detection event. Customers can use this contextualization to write better detections, prioritize existing alerts, and drive investigation faster. With this launch, Google Chronicle customers can now incorporate advanced enrichment capabilities earlier in the detection authoring and execution workflow, enabling them to:
- Prioritize threats with risk scoring: Making relevant context available for heuristic-driven contextual risk scoring of detections at detection execution time rather than at the human triage stage.
- Respond to alerts faster: Reducing time spent on triage and manually stitching together information from disparate IT security systems (e.g. EDR consoles, firewall/proxy logs, CMDB and IAM context, and vulnerability scan results).
- Enhance fidelity of alerting: Enabling analysts and detection engineers to filter out entire clusters of threats that may be expected or represent little-to-no danger to the enterprise (e.g. malware testing in a sandbox environment, vulnerabilities and anomalous activity in a development network with no sensitive data or access, and more).
To put this in perspective, here is an example of our integration with Google Cloud DLP: Customers can use DLP for BigQuery integration and enable scans of their BQ tables to find where sensitive data resides, and provide a risk score for each table – a particularly valuable feature since many customers don’t accurately know where their most sensitive data resides. This new DLP integration into Chronicle allows us to bring in this score (among other things) allowing analysts to gain immediate insight into if the BQ data targeted by an attacker is of high value.
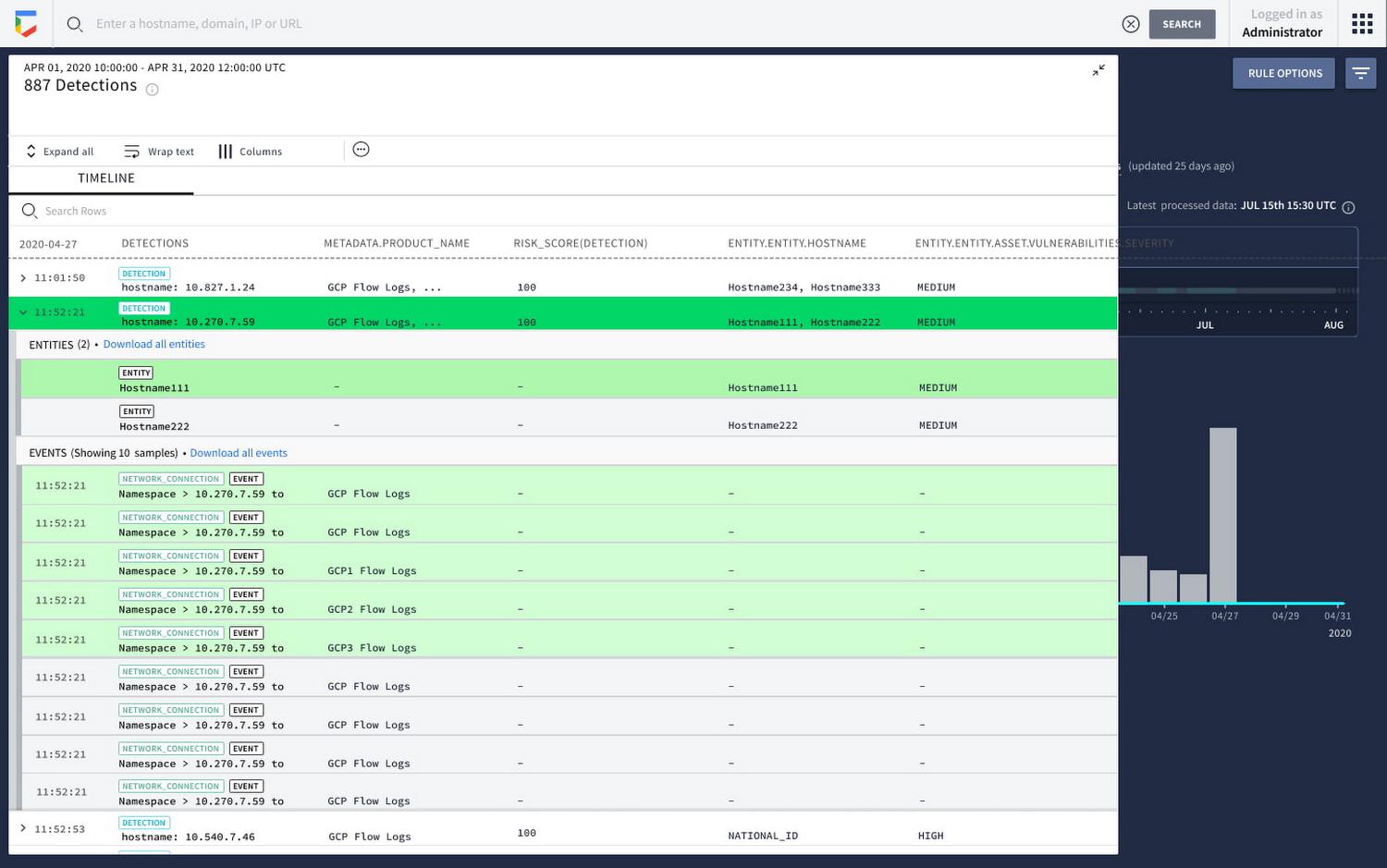
Once a detection is enabled, customers will now see a new risk score field populate that allows them to prioritize by risk. This will provide immediate orientation on what must be prioritized for escalation. In addition to the risk score, we now contextualize results with additional enrichment around the entities contained in the events to preemptively answer why higher risk findings warrant prioritization.
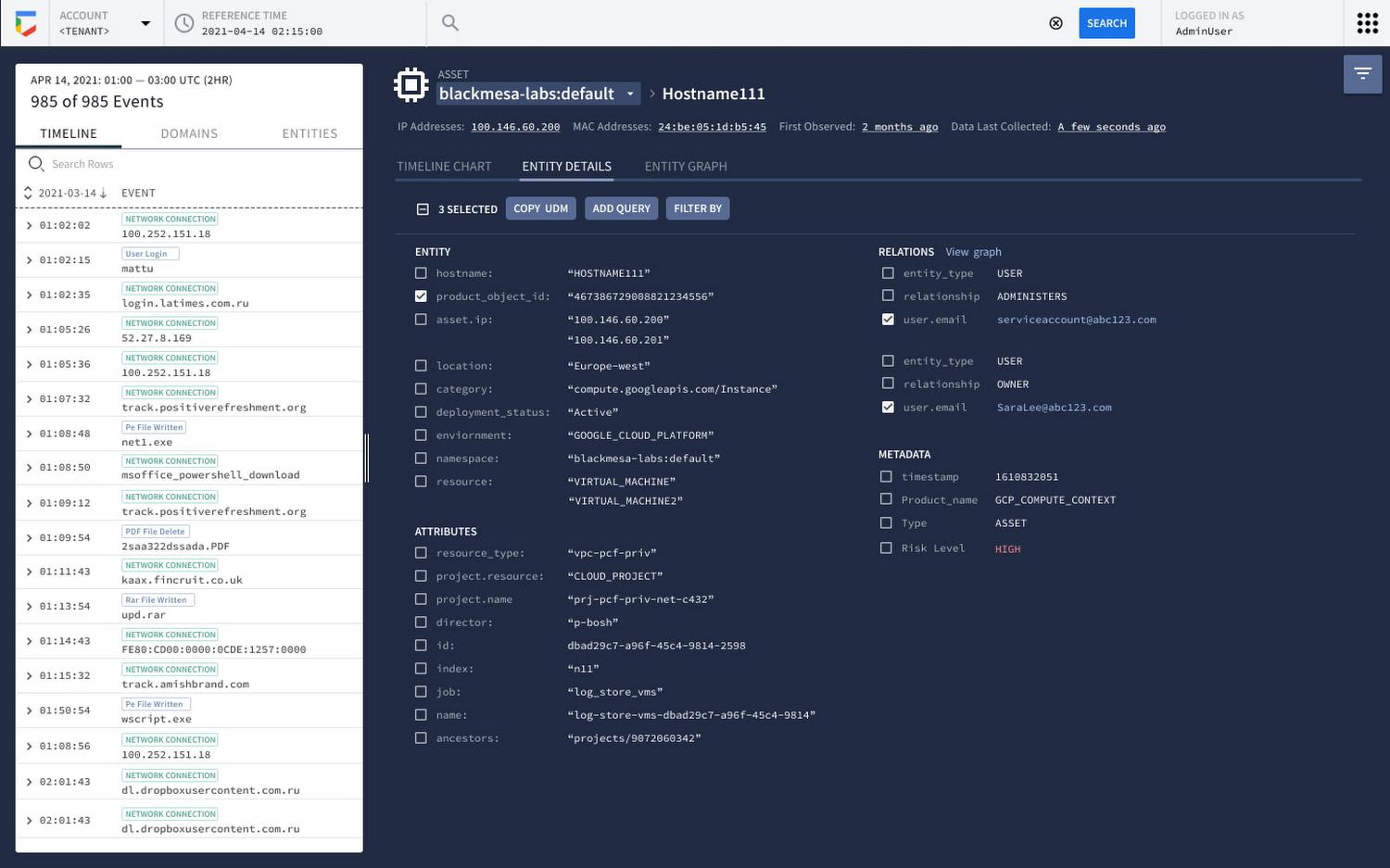
From there, customers can pivot into Asset View to inspect affected hosts and examine specifics with prioritized assets identified in their rule results. We have added a new section that summarized entity details.
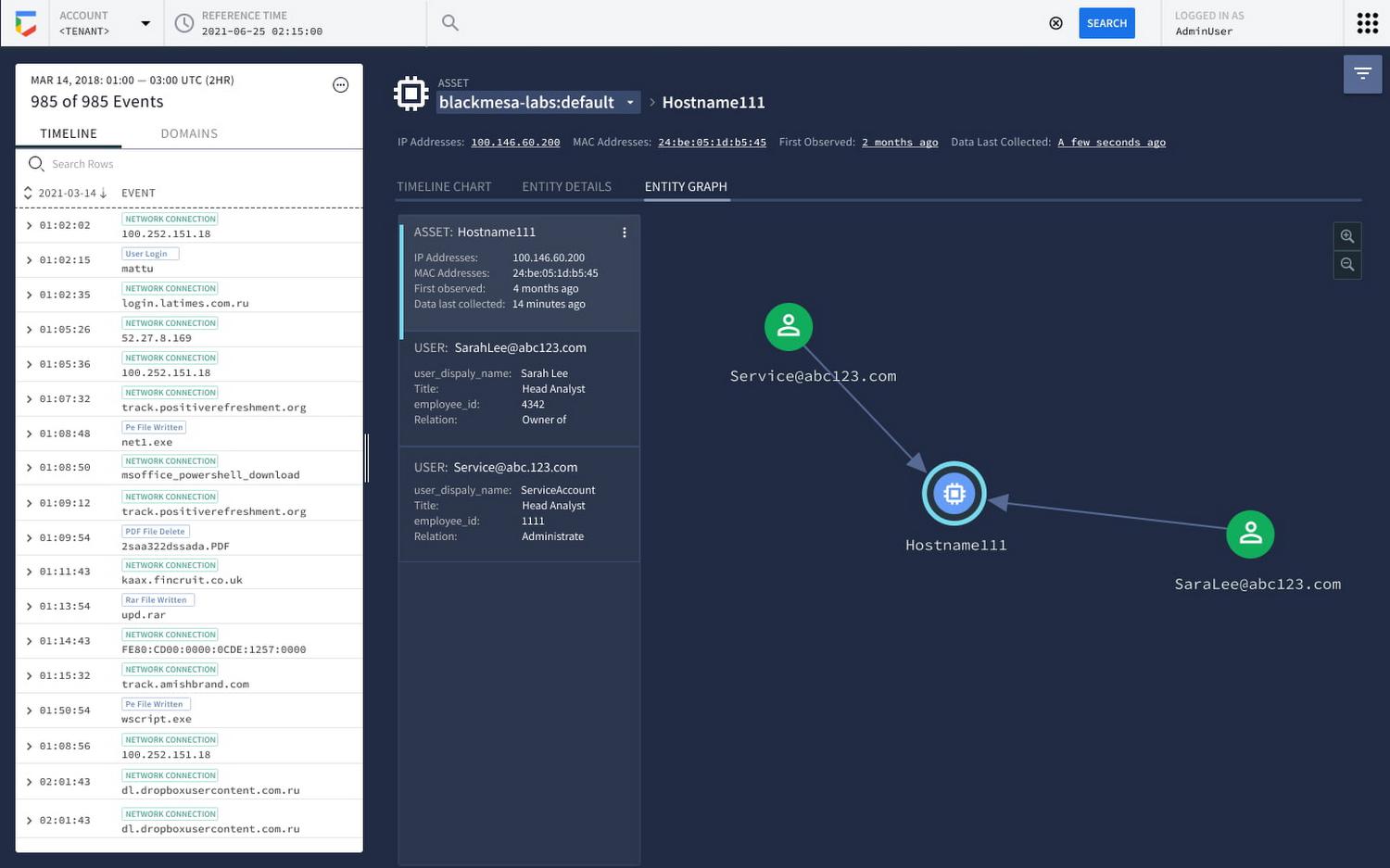
Finally, we provide a graph view that depicts immediate entity relationships to provide useful data that customers may want to pivot their investigation to.
This launch fixes a paradigm gap in legacy analytics and SIEM products, where data has historically been logically separated due to prohibitive economics. Customers can now operationalize all their security telemetry and enriching data sources in one place, giving them the ability to develop flexible alerting and prioritization strategies. Simply put, this will reduce mean time to respond (MTTR) for users by minimizing the need to wait for contextual understanding before making a decision and taking an investigatory action.
We’re excited about the kinds of detection that are possible with this launch. During our public preview, customers used these modules to detect various threats and took remedial actions to prevent threats earlier in their lifecycle.
Over the next months as we move these modules towards general availability, you can expect to see a steady release of new detection capabilities and integrations with other services and security controls in Google Cloud and additional third party providers.
To learn more about these new capabilities, contact your Google Cloud sales and CSM team. You can learn more about all these new capabilities in Google Chronicle in our product documentation. To learn more about our overall Google Chronicle vision please view our recorded sessions at Security Talks.
By: Mike Hom (Product Architect, Google Chronicle) and Travis Lanham (Engineering Lead, Google Chronicle)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!