The Canadian government’s security guidance for cloud environments outlines a standardized set of security controls to protect data and workloads in the cloud. The security guidance, known as the Security Control Profile for Cloud-based GC Services, also outlines security controls and profiles from a different publication, the IT Security Risk Management: A Lifecycle Approach (ITSG-33).
The ITSG-33 publication has made Protected B Medium Integrity Medium Availability (PBMM) a key compliance measure for the Canadian government and crown corporations.
From our partners:
As part of our commitment to serving the Canadian government with the security capabilities and controls they need, we’ve developed a set of open-source recommendations that map Google Cloud capabilities and security settings to Canadian Protected B regulatory requirements to help our customers place their sensitive data in the cloud. With the Google Cloud landing zones, we’re helping to ensure Canada has the easy-to-administrate, cost-effective, and more secure cloud environment needed for your biggest projects.
Cloud environments built for Canada
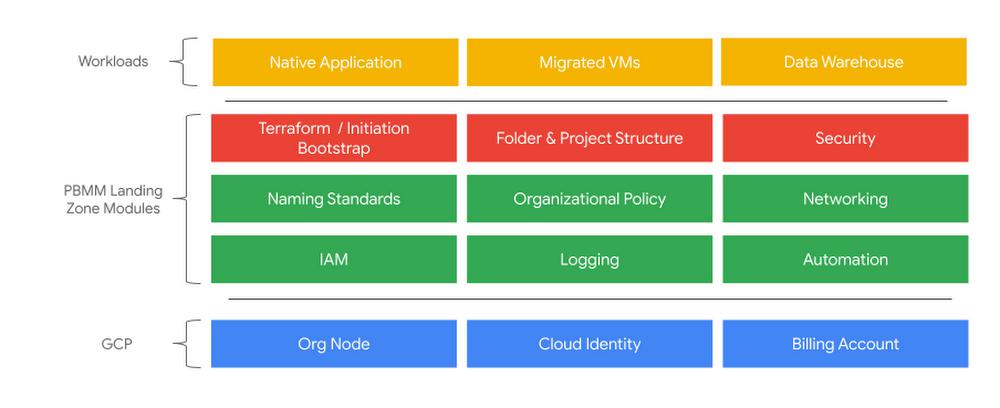
Google Cloud’s Protected B landing zones are a set of codified recommendations focused on establishing Google Cloud projects, Identity Access Management (IAM), networking, naming schemes, and security settings in line with regulatory requirements and best practices. Using these as a baseline, Canadian public sector customers are better positioned to quickly meet their compliance requirements.
Google Cloud has published a Terraform-based Infrastructure-as-Code (IaC) template on Github to ensure the foundational settings, policies, and folder structures are correctly configured in alignment with the Annex 4A – Profile 1 (PBMM and ITSG-33).
Codified, built-in security
Landing zones enable a secure environment that is quick to deploy, easy to administer, and provides cost savings for organizations. To make our templates easily understandable, we’ve selected the open-source infrastructure-agnostic IaC tooling provided by HashiCorp’s Terraform. Terraform gives organizations the flexibility to adopt a DevSecOps methodology within their infrastructure. It also provides a security foundation by allowing the IaC to be modified, versioned, change controlled, and automatically provisioned.
The template and instructions on how to use landing zones can be found on GitHub.
Included security controls
There are effectively three different types of security controls described in ITSG-33 documentation:
- Technical security controls implemented using technology, such as firewalls.
- Operational security controls implemented using human processes, such as manual procedures.
- Management security controls focused on the management of IT security and IT security risks.
Within the landing zone template, we’ve focused on controls that can be represented via code. Addressed controls fall into these primary families:
- Access Control (AC)
- Audit and Accountability (AU)
- Configuration Management (CM)
- Contingency Planning (CP)
- Identification and Authentication (IA)
- Risk Assessment (RA)
- System and Services Acquisition (SA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
How it works
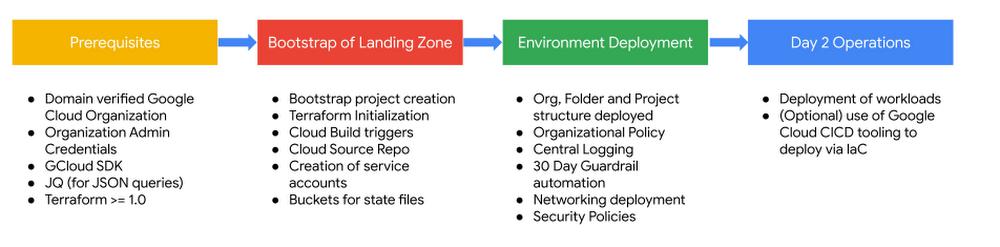
The landing zone deployment phases
To deploy the landing zone, a user with Organizational Administrator privileges will need access to a shell terminal with the Google Cloud (gcloud) CLI, JSON Query (jq) and Terraform installed (which can be done in Google Cloud’s integrated terminal, Cloud Shell). As part of the initial bootstrap script, a single project will be created. This Google Cloud project will be used to set up the landing zone core infrastructure, network infrastructure, automated pipeline, code repository, logging and bunkering aggregation capabilities, and security policies via infrastructure as code automation. After deployment completes, workloads can be deployed in alignment with IT and regulatory policies. This can include leveraging the Cloud Build & Cloud Source Repo (CICD) pipeline established as part of the landing zone bootstrapping.
Several Terraform modules are used to establish the required controls for meeting PBMM requirements:
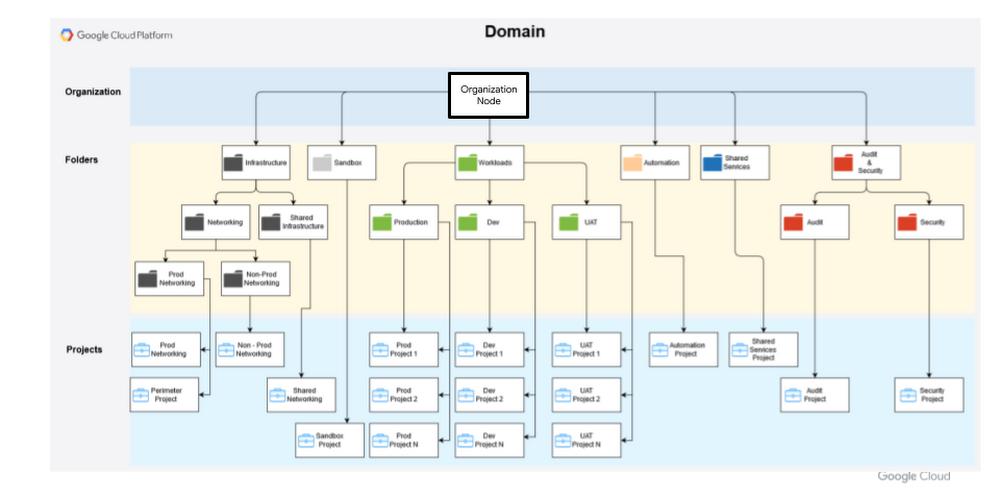
The landing zone can be applied with either a Google Cloud organizational node (default and illustrated below), or with a folder as the root node of the landing zone.
How to deploy it
- Have a shell environment with the required prerequisites installed (Cloud Shell can be used for this)
- Clone repo from https://github.com/GoogleCloudPlatform/pbmm-on-gcp-onboarding
- Update the relevant .auto.tfvars files as indicated in the README.MD file within the repo
- From bash, run the bootstrap.sh script from the environments/bootstrap/ directory. The script will prompt for the domain and user that will be deploying the bootstrap resources.
Committed to serving Canada
Our landing zone template extends upon our existing 30-day Guardrails created to meet Canadian Centre for Cyber Security requirements, allowing organizations to have a compliant landing area for production workloads quickly. Visit the Terraform-based Infrastructure-as-Code (IaC) template on GitHub for more detailed deployment instructions and to learn more about meeting CCCS requirements.
By: Mike Craigen (Customer Engineer, Public Sector, Google Cloud)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!