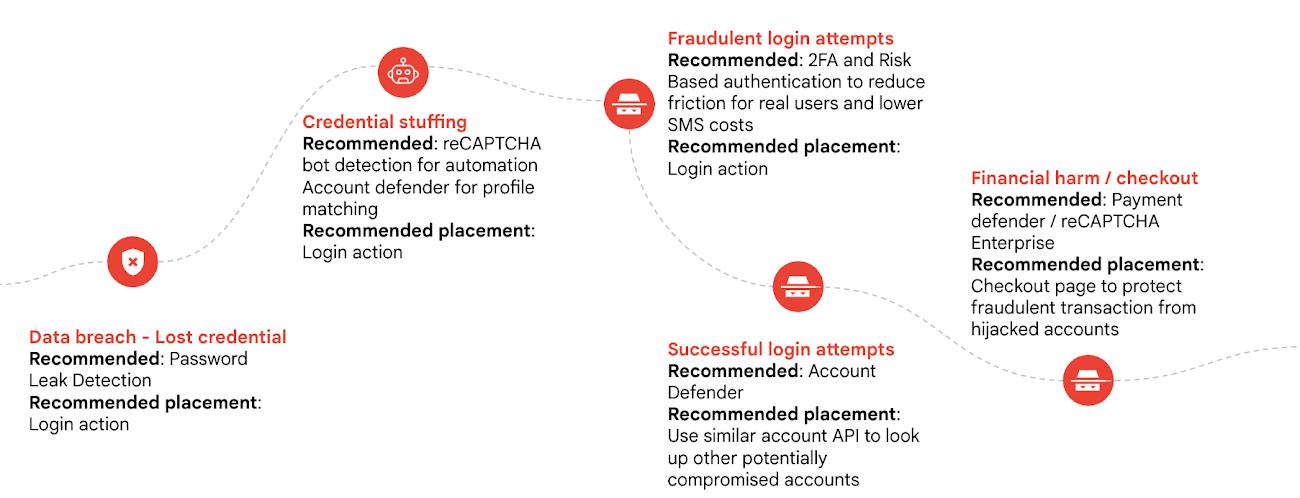
As long as passwords remain an incredibly common form of account authentication, password reuse attacks—which take advantage of people reusing the same password across multiple services—will be one of the most common ways for malicious hackers to hijack user accounts.
Password reuse is such a serious problem that more than 52% of users admitted to reusing their password on some sites, and 13% confessed that they use the same password on all their accounts, according to a Google/Harris Poll conducted in 2019. When malicious hackers steal passwords in data breaches, they’re looking to exploit password reuse and increase the chances that future attacks against organizations will be more successful. They can automate these attacks with bots, too, which enables them to scale their attacks. Ultimately, these attacks can lead to account takeovers and can create real regulatory, trust, and reputational risk for organizations.
From our partners:
reCAPTCHA Enterprise password leak detection can help prevent account takeovers
Although it’s considered a best-practice to discourage password reuse, we realize that it still happens. That’s why we’ve built into reCAPTCHA Enterprise a password leak detection capability, now generally available to all reCAPTCHA Enterprise users. One of the most effective ways to prevent a successful account takeover is to warn users as early as possible that their passwords need to be changed. Customers can take immediate action on user credentials as part of any assessment to ensure that they have not been leaked or breached elsewhere.
reCAPTCHA Enterprise provides organizations with the ability to protect their users against account takeovers. The reCAPTCHA Enterprise password leak detection feature is implemented using a privacy-preserving API which hides the details of the credentials and the result from Google’s backend services, and allows customers to keep their users’ credentials private.
When paired with reCAPTCHA Enterprise bot management, account defender, and two-factor authentication, organizations can build robust protections against attacks such as credential stuffing and account takeovers.
Get started protecting your app against account takeovers, bots, and credential stuffing
New and current reCAPTCHA Enterprise customers can now activate password leak detection following the detailed documentation available in our help center, or reach out to sales to learn more about the capabilities of reCAPTCHA Enterprise.
By: Badr Salmi (Product Manager reCAPTCHA Enterprise) and Aaron Malenfant (Technical Lead reCAPTCHA)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!