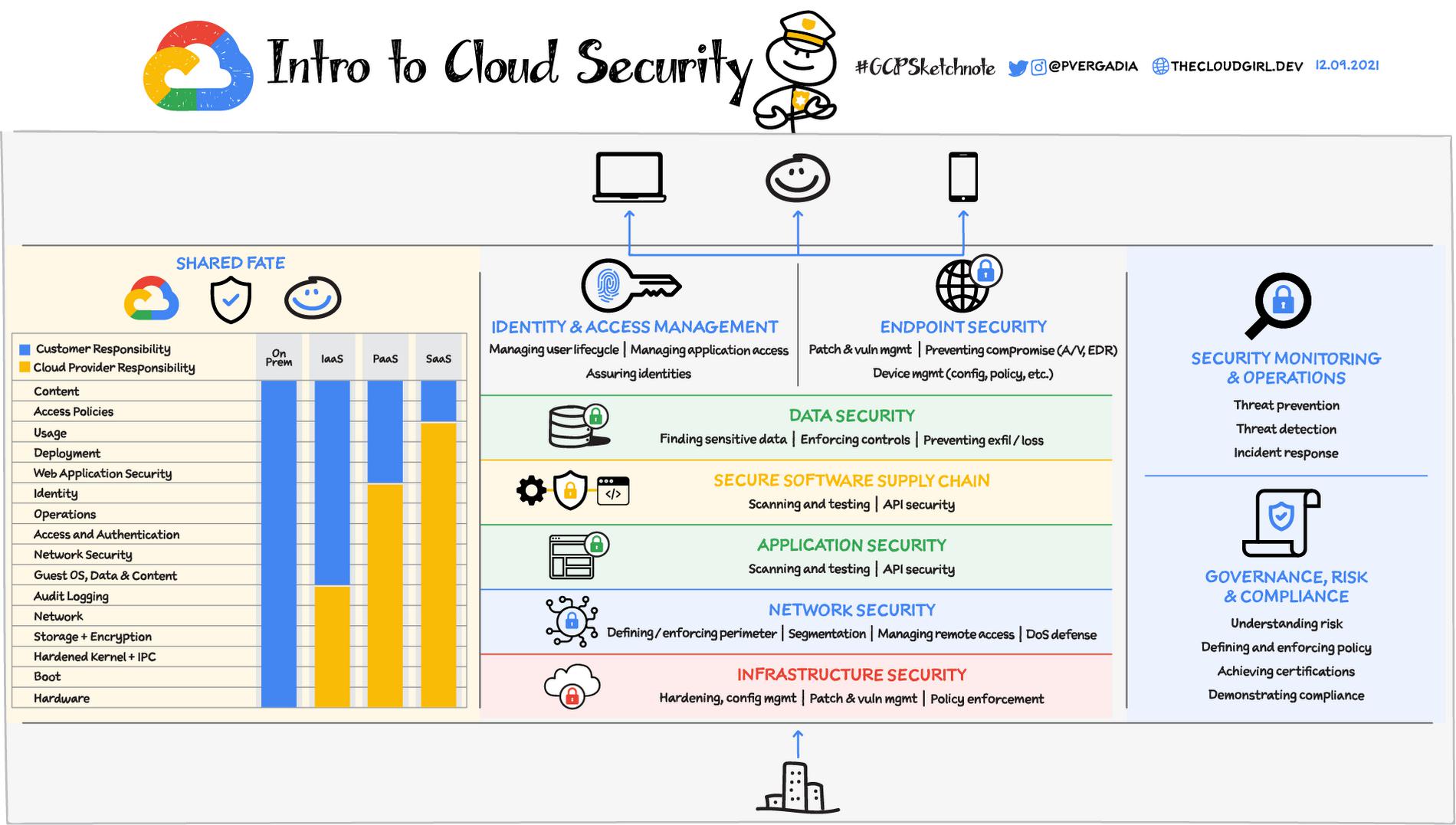
When you think about Cloud Security there are many areas of responsibility – securing infrastructure, network, data, applications, and managing identities and access. There are also ongoing processes for security operations and governance, risk & compliance management. But the best part of building your application on cloud is that you share the security responsibility with the cloud provider.
Shared Responsibility and Shared Fate
Cloud security requires collaboration and is usually operated on a shared responsibility model where the cloud provider is responsible for the security of the underlying cloud infrastructure and you are responsible for securing the applications you deploy on the cloud. This gives you the flexibility and control you need to implement the required security controls for your application and business. Depending on your use case you can restrict access to the sensitive data and projects or selectively deploy public applications.
At Google Cloud, we strive to go beyond the basics of this shared responsibility model to an operating model based on Shared Fate . Shared fate is about preparing a secure landing zone for a customer, guiding them while there, being clear and transparent about the security controls they can configure, offering guardrails, and helping them with cyber-insurance. This is to help ensure that customers have a robust security posture with secure-by-design services, secure defaults, and a rich set of best practices, templates, blueprints, documentation, and professional services that we make available.
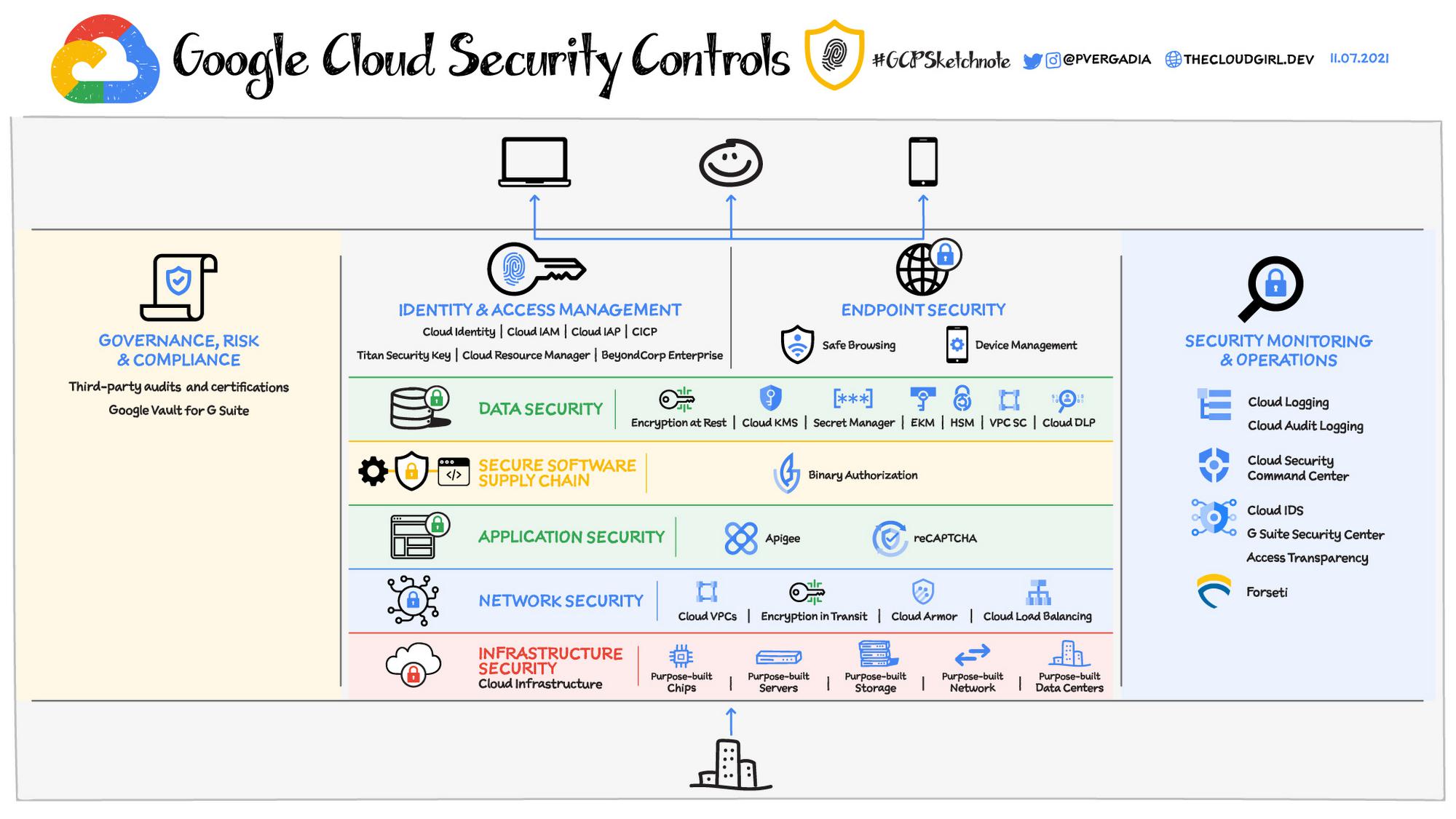
Now, let’s see how Google Cloud provides capabilities across the different layers of security:
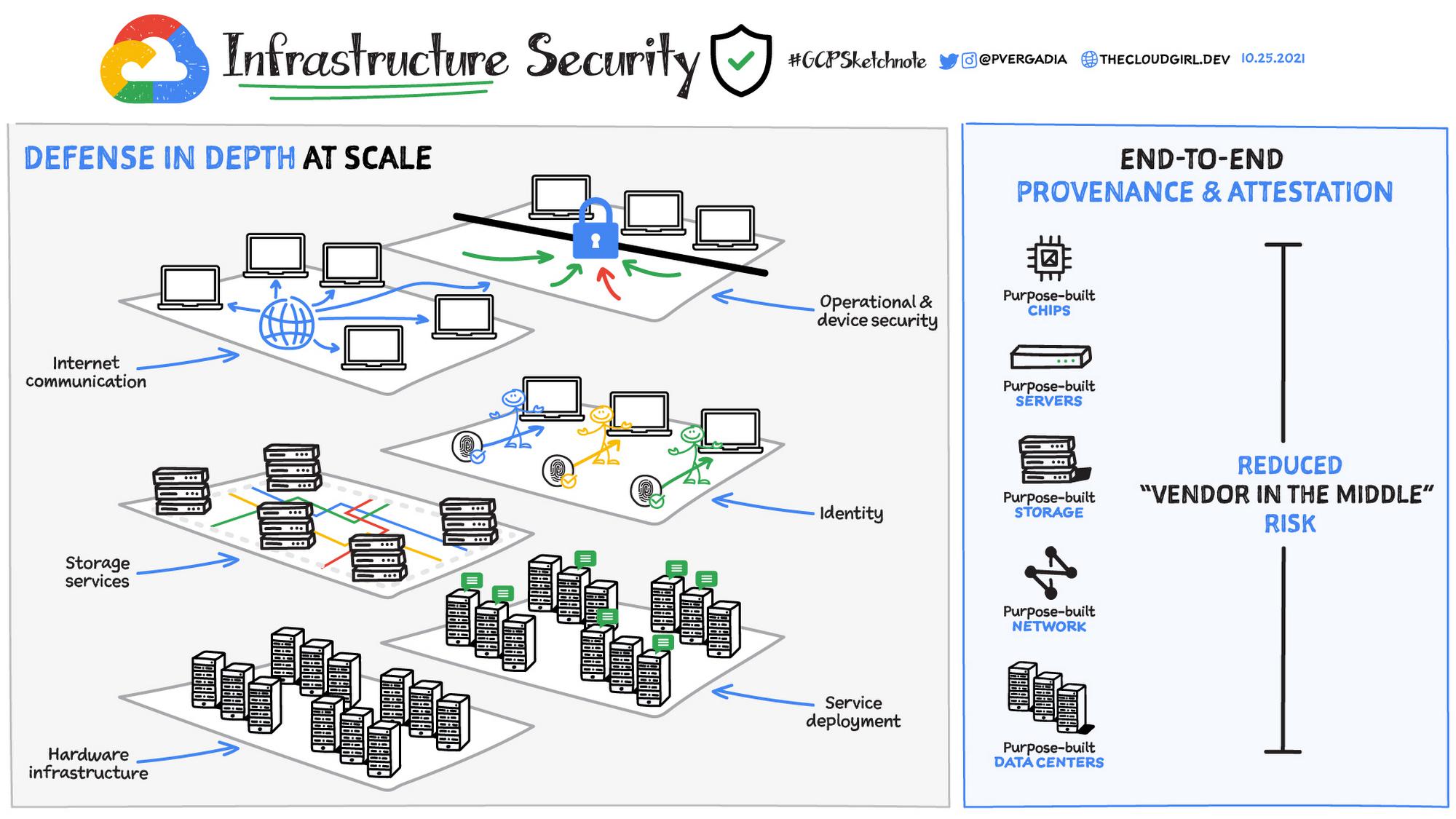
Infrastructure security
Cloud providers are responsible for providing infrastructure security, which includes security through the entire information processing life cycle including hardware infrastructure, service deployment, storage services, user identity, internet communications and operational and device security.
Google’s stack builds security through progressive layers that deliver true defense in depth at scale. Google’s hardware infrastructure is custom-designed “from chip to chiller” to precisely meet specific requirements. Its software and OS are stripped-down, hardened versions of Linux. Titan purpose-built chips help establish a hardware root of trust. This end-to-end provenance and attestation helps Google greatly reduce the “vendor in the middle problem”.
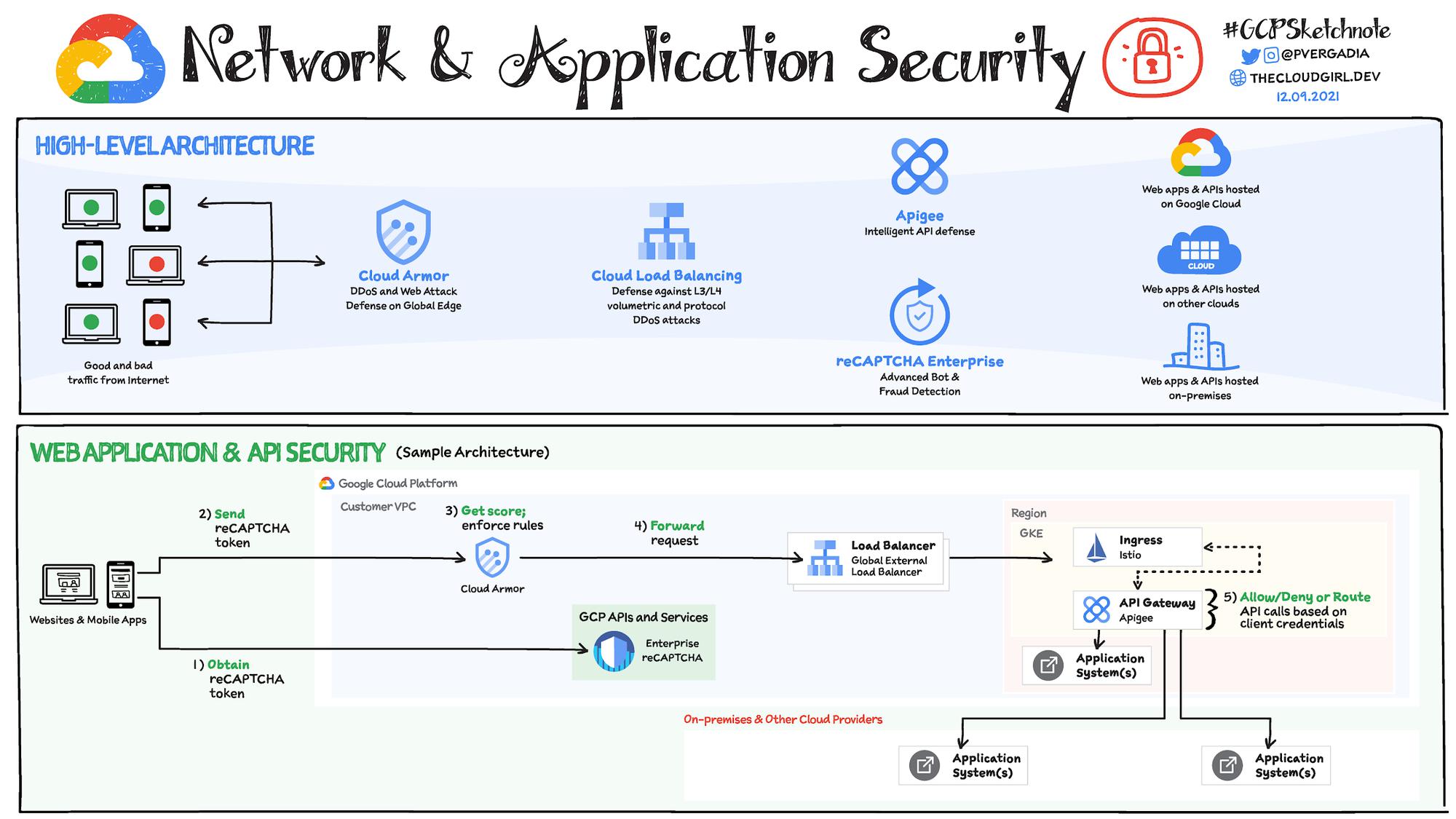
Network security
Network security is partly the cloud providers responsible and partly yours. Providers work to make sure the traffic is secure and encrypted and the communication with others services on the public internet are secure. They also offer strong baseline protection against network attacks.
You are responsible for defining and enforcing your application perimeter, segmentation of your projects between teams and organizations, managing remote access for your employees and implementing additional DoS defense.
- Google Cloud Virtual Private Cloud (VPC) offers private connectivity between multiple regions without communicating across the public internet. You can use a single VPC for an entire organization, isolated within projects.
- VPC flow logs capture information about IP traffic to and from network interfaces and help with network monitoring, forensics, real-time security analysis, and expense optimization.
- Shared VPC helps configure a VPC network to be shared across several projects in your organization. Connectivity routes and firewalls associated are managed centrally. You can also segment your networks with a global distributed firewall to restrict access to instances.
- Firewall Rules policies lets you set rules for access and logging lets you audit, verify, and analyze the effects of your firewall rules.
- VPC Service Controls extend the perimeter security to manage Google Cloud services by preventing access from unauthorized networks.
- Application security
- Cloud IDS: Cloud Intrusion Detection System provides managed, cloud-native network threat detection from malware, spyware, command-and-control attacks
Application security
When building an application or API on cloud you are responsible for the application security including the scanning and testing. Adopt practices such as:
- Allow and deny traffic based on authentication and authorization of the user.
- Use or implement services to block off bot & fraudulent users from your website.
You can protect your internet facing application against attacks by using Web App and API protection (WAAP) solutions. This solution is a combination of:
- Cloud Load Balancing: Provides automatic defense against Layer 3 and Layer 4 DDoS attacks
- Cloud Armor: Filter incoming web requests by geography or a host of L7 parameters like request headers, cookies, or query strings
- reCAPTCHA Enterprise: Provides protection against bots and fraudulent users.
- Apigee API Gateway: Protects API backend by throttling API traffic against DDoS attack and control access to APIs with OAuth, API key validation, and other threat protection capabilities.
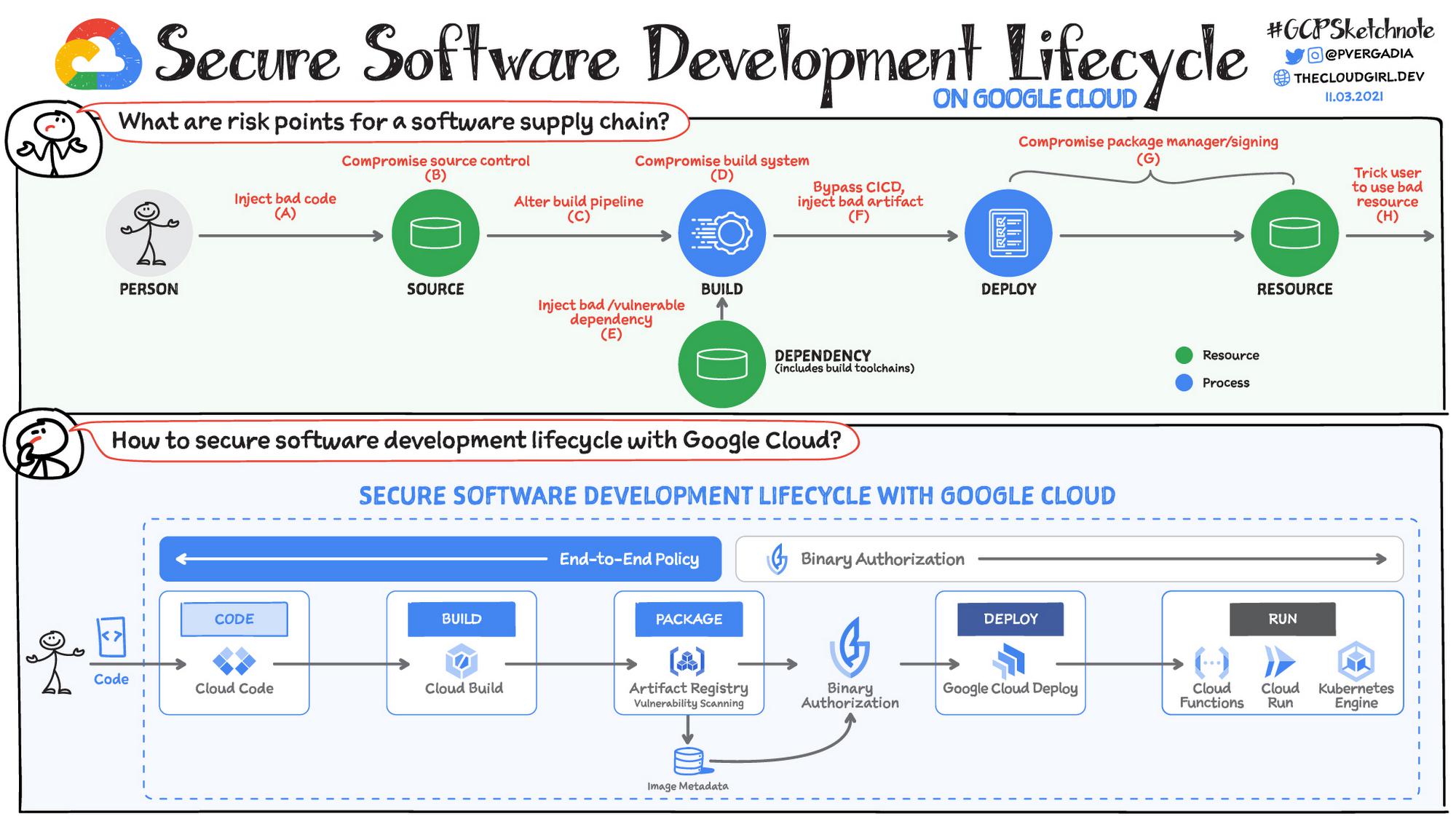
Software Supply Chain Security
Securing your software requires establishing, verifying, and maintaining a chain of trust, to establish the provenance or origin trail of your code, via attestations, generated and checked throughout your software development and deployment process. Open source SLSA Supply chain Levels for Software Artifacts is an end-to-end framework for Supply Chain Integrity that you can adopt incrementally to increase your security posture.
In Google, Cloud Binary Authorization service establishes, verifies, and maintains a chain of trust via attestations and policy checks across different steps of the SDLC process.
- Code: Using Open Source Insights identify dependencies, security advisory, license across open source code.
- Build: Cloud Build captures another set of attestations (tests run, build tools used etc) that add to your chain of trust.
- Test & scan: Complete build when stored in Artifact Registry is automatically scanned for vulnerabilities.
- Deploy & run: Binary Authorization verified for authenticity & deploys when attestations meet organization policy. It even continuously validates conformance to the policy after deployment.
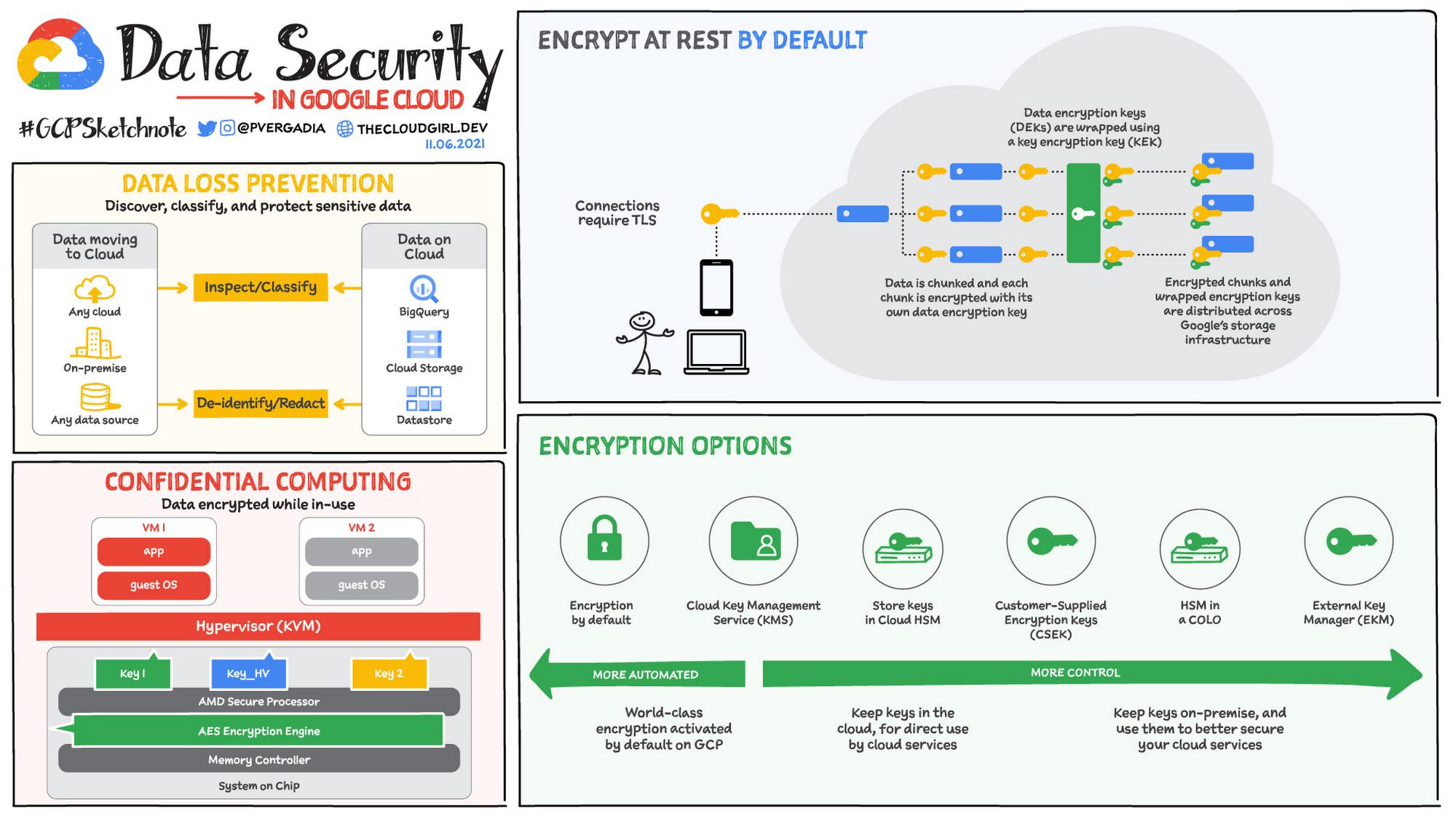
Data Security
Data security is a shared responsibility between you and the cloud provider. The cloud provider offers some capabilities built into the infrastructure such as data encryption at rest and in transit while you are responsible for your applications’ data security. This includes features such as key and secret management, finding sensitive data, enforcing controls, preventing exfiltration and data loss.
Google Cloud offers data encryption at rest and in transit with the option to encrypt data in use using Confidential Computing. If you need the data to be encrypted via your own keys you can bring your own key (CSEK), use Google’s managed Key Management Service (KMS), use a hardware security module (HSM) or an external key manager (EKM). Data Loss Prevention (Cloud DLP) helps discover, classify, and protect sensitive data.
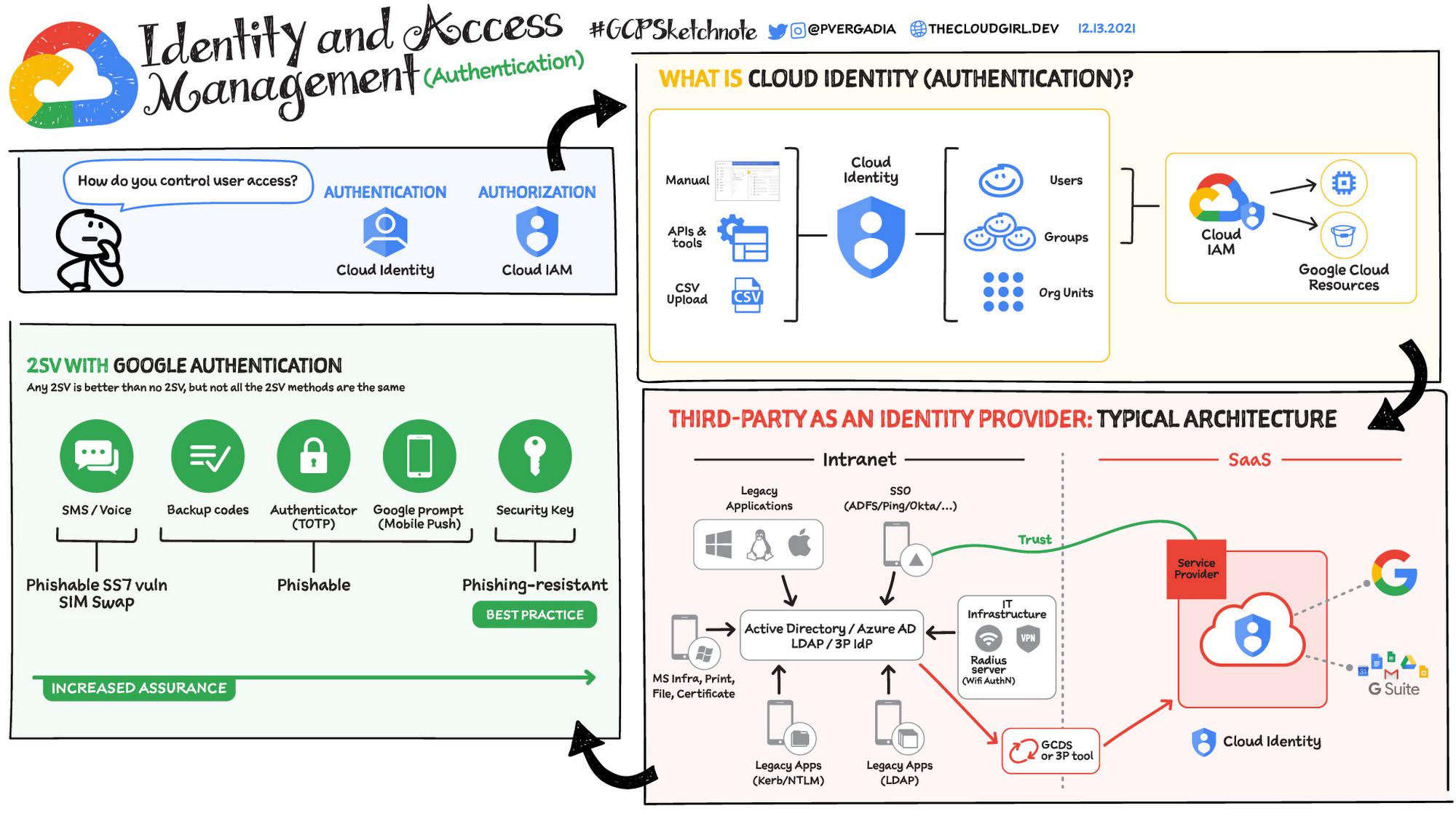
Identity and access management
This requires securely managing the user lifecycle and application access, including authentication of the user and authorization of those users to appropriate services.
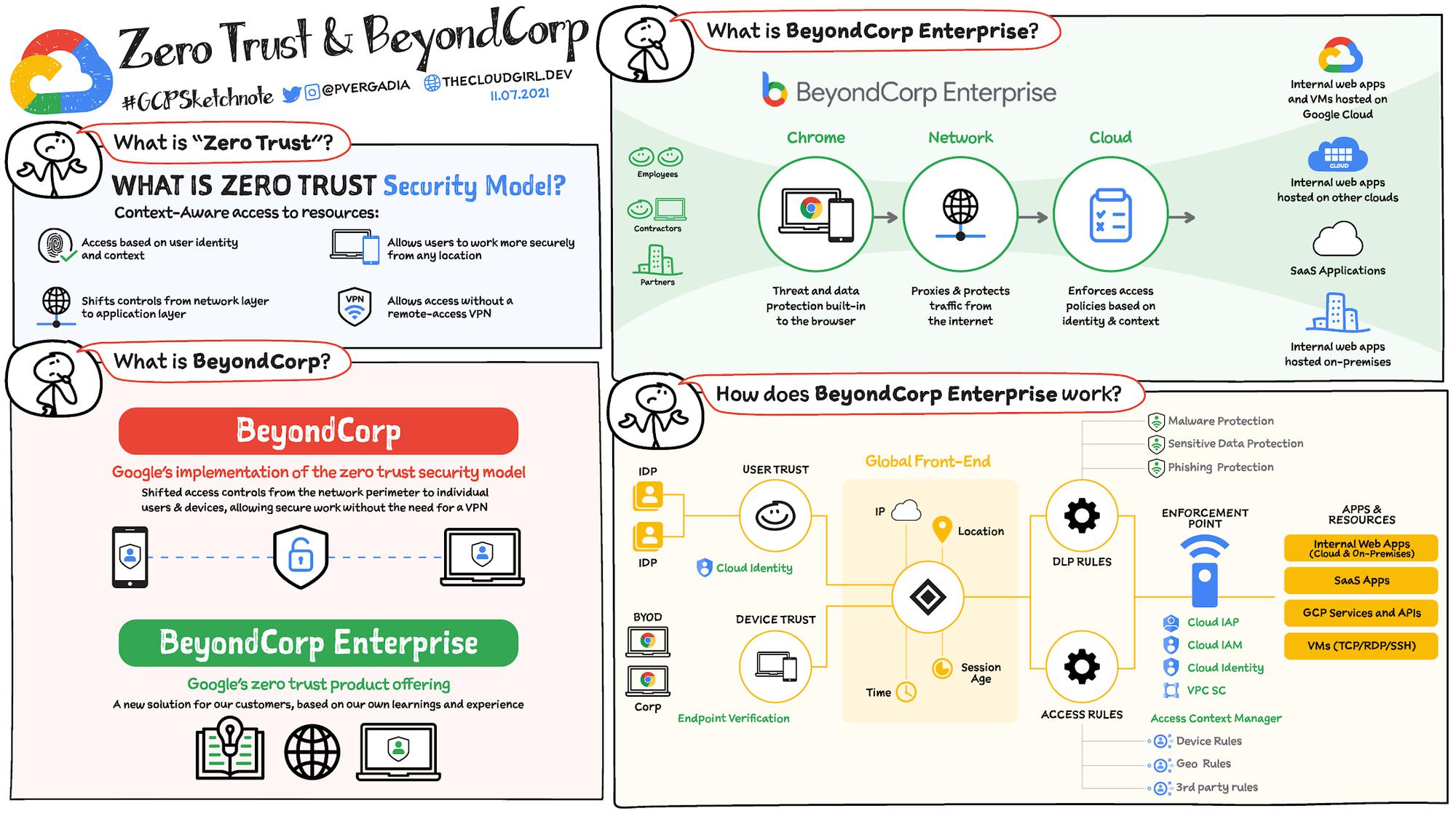
In Google Cloud, Cloud Identity is the IdP which provides the authentication options. It stores and manages digital identities for cloud uses, also provides 2 step verification and SSO integration with third party identity provider such as Okata, Ping, ADFS or Azure AD.
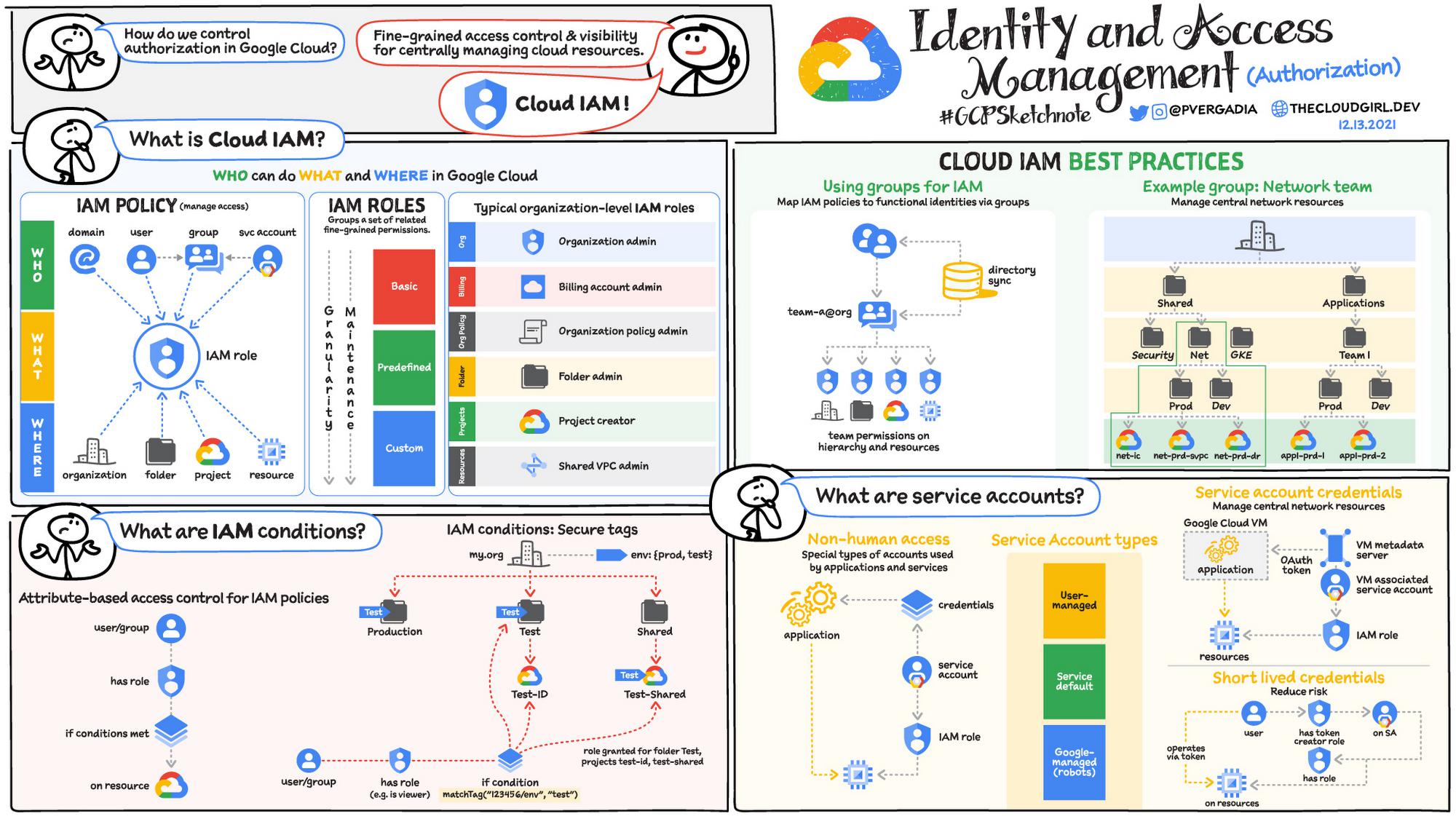
Once authenticated, Cloud IAM provides the authorization – “who can do what and where on Google Cloud” by providing fine-grained access control and visibility for centrally managing cloud resources. IAM policies manage access control for Google Cloud resources and IAM Roles help set fine-grained permissions.
BeyondCorp Enterprise enacts a zero-trust model for access to your applications and resources. No one can access your resources unless they meet all the rules and conditions codified in per-resource access policies:
Endpoint security
Endpoint security is critical for protecting users and access. You need to make sure you apply patches, prevent compromises and manage user devices including the policies that define which device has access to which resources in your application or projects.
Safe Browsing or Web Risk API: Lets client applications check URLs against Google’s constantly updated lists of unsafe web resources. With Safe Browsing you can:
- Check pages against our Safe Browsing lists based on platform and threat types.
- Warn users before they click links in your site that may lead to infected pages.
- Prevent users from posting links to known infected pages from your site.
Security monitoring and operations
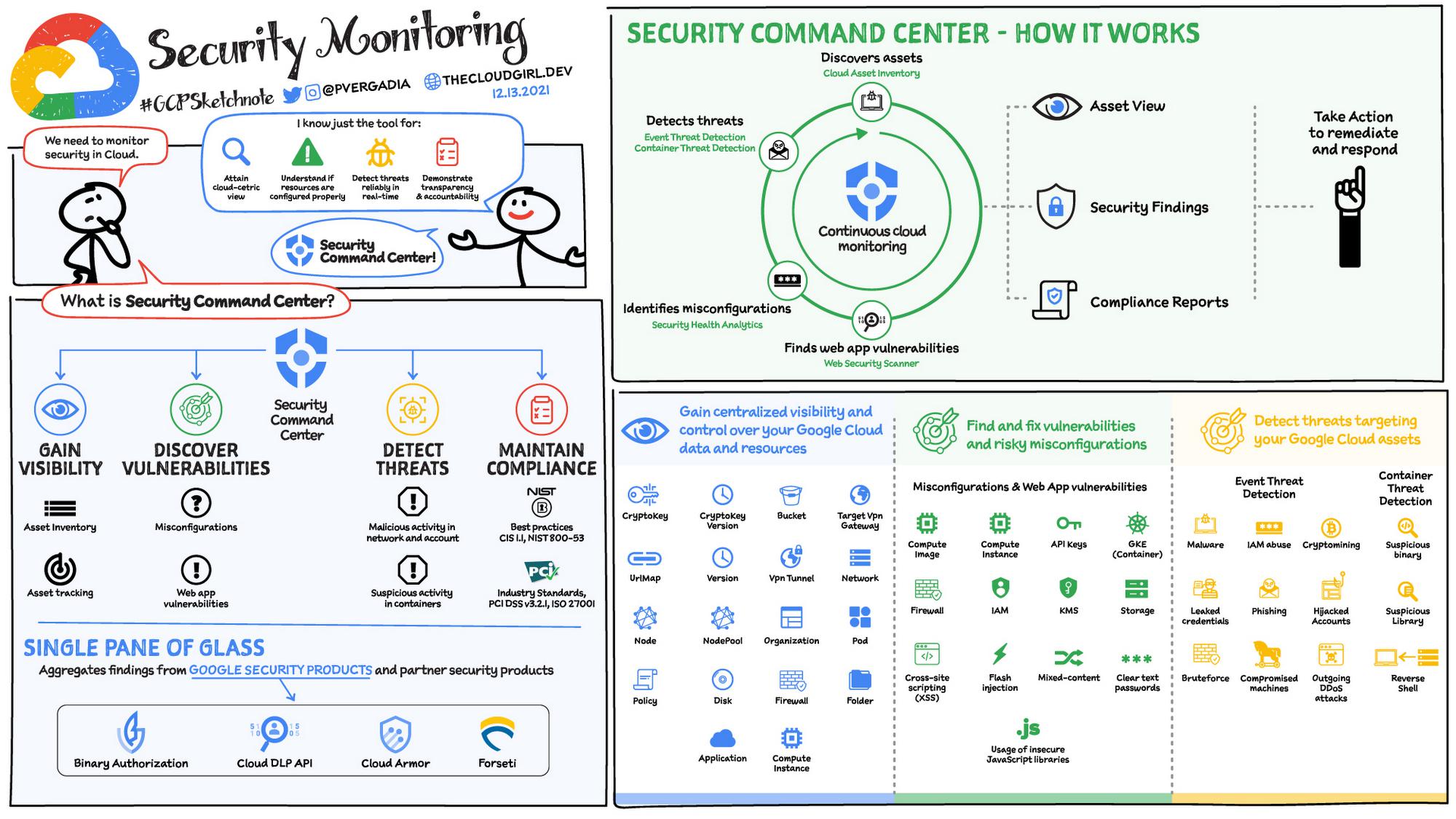
From a Security Operations (SecOps) perspective, you need to detect, respond to, and remediate threats in the Cloud.
In Google Cloud this can be achieved through:
- Security Command Center: Continuously monitors your Google Cloud environment for misconfigurations, detects threats, malicious activity and helps maintain compliance.
- Audit Logs: Cloud Logging offers Audit logs that record administrative activities and accesses within your Google Cloud resources. Audit logs help you answer “who did what, where, and when?”
- Access Transparency: Logs record the actions that Google personnel take when accessing customer content
- Siemplify Security Orchestration, Automation and Response (SOAR): enables modern, fast and effective response to cyber threats by combining playbook automation, case management and integrated threat intelligence in one cloud-native, intuitive experience.
Governance, risk and compliance
Includes understanding security risk, defining and enforcing policy, demonstrating compliance by achieving certifications and maintaining a sound security posture.
Google Cloud is compliant with major security certifications such as PCI DSS, FedRAMP, HIPAA and more. Google Cloud products regularly undergo independent verification of their security, privacy, and compliance controls, achieving certifications, attestations, and audit reports to demonstrate compliance. To learn more about it check out this page
That was a bird’s eye view of the Google Cloud Security Services. For a more in-depth look into the security check out the whitepaper here.
For more #GCPSketchnote, follow the GitHub repo. For similar cloud content follow me on Twitter @pvergadia and keep an eye out on thecloudgirl.dev
By: Priyanka Vergadia (Lead Developer Advocate, Google)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!