Java and Go vulnerability scanning support
Google Cloud’s Container Scanning API now automatically scans Maven and Go packages for vulnerabilities.
With the Container Scanning API enabled, any containers including Java (in Maven repositories) and Go language packages that are uploaded to an Artifact Registry repository will be scanned for vulnerabilities. This capability builds on existing Linux OS based vulnerability detection and provides customers with deeper insight into their applications. This feature is in Public Preview which makes it available to all Google Cloud customers.
From our partners:
Get started with Artifact Registry via the instructions for Go or the instructions for Java.
How it works
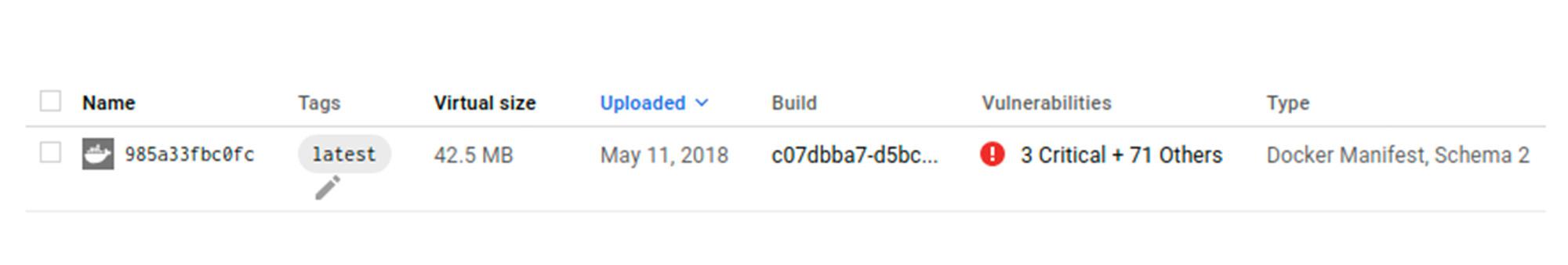
Once the API is enabled, upload a container image which contains Go and/or Maven packages.
Vulnerability totals for each image digest are displayed in the Vulnerabilities column. Customers can then drill down on the vulnerability to get CVE numbers, and if available, a suggested fix.
Vulnerabilities can also be displayed via the gcloud CLI and the API.
To view a list of vulnerabilities from the gcloud CLI, the following can be used.
gcloud artifacts docker images list --show-occurrences LOCATION-docker.pkg.dev/PROJECT_ID/REPOSITORY/IMAGE_ID --format=json
To view a list of vulnerabilities with the API, run the following command.
curl -X GET -H "Content-Type: application/json" -H \"Authorization: Bearer $(gcloud auth print-access-token)" \https://containeranalysis.googleapis.com/v1/projects/PROJECT_ID/occurrences
Integrate your Workflows via API and Pub/Sub
This feature now makes it possible to scan Java (in Maven repositories) and Go language packages both via the existing On-Demand scan capability, and with an automatic scan on push to Artifact Registry. Language scanning is in addition to the Linux OS scanning which is already available.
This capability can be combined with Pub/Sub notifications to trigger additional actions for the vulnerabilities and other metadata. An example of this is sending an e-mail notification to those who need the information.
Organizations are increasingly concerned about the supply chain risks associated with building their applications using open source software. Being able to scan applications for vulnerabilities is an important step for customers to enhance their security posture. Language package vulnerabilities are available in the same formats that customers are already familiar with. They appear alongside OS vulnerabilities within the Artifact Registry UI, and are available through existing CLI and APIs. These steps aid customers in identifying the potential vulnerabilities introduced in software packages and make appropriate decisions with that information.
Learn more about types of vulnerability scanning.
By: Nate Avery (Outbound Product Manager) and Greg Mucci (Product Manager, Developer Experience)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!