Answering the software supply chain security call
To further help our customers improve their software supply chain security, we’re now excited to announce Software Delivery Shield. This is a fully managed software supply chain security solution that offers a modular set of capabilities to help equip developers, DevOps, and security teams with the tools they need to build secure cloud applications. Software Delivery Shield spans across a family of Google Cloud services from developer tooling to runtimes like GKE, Cloud Code, Cloud Build, Cloud Deploy, Artifact Registry, Binary Authorization, and more.
From our partners:
Develop fast, securely
To help protect software from the beginning — at the development stage — we’re excited to introduce a new service in Preview at Google Cloud Next: Cloud Workstations, which provides fully managed development environments on Google Cloud. With Cloud Workstations, developers can access secure, fast, and customizable development environments via a browser anytime and anywhere, with consistent configurations and customizable tooling. At the same time, IT and security administrators can easily provision, scale, manage, and secure the development environments on Google Cloud’s infrastructure.
A critical part of Software Delivery Shield, Cloud Workstations plays a key role in “shifting security to the left,” by enhancing the security posture of the application development environment. With built-in security measures such as VPC Service Controls, no local storage of source code, private ingress/egress, forced image updates and IAM access policies, Cloud Workstations helps address common local development security pain points like code exfiltration, privacy risks, and inconsistent configurations.
In addition to helping secure dev environments with Cloud Workstations, we’re also giving developers tools to code fast and more securely from their laptops. Cloud Code, our family of IDE plugins, now features Source Protect in Preview. Source Protect gives developers real-time security feedback as they work in their IDEs, identifying issues such as vulnerable dependencies and license reporting. This kind of quick and actionable feedback can allow developers to promptly make corrections to their code, saving time from costly future fixes.
Safeguard the software ‘supply’
Securing the software supply — build artifacts and application dependencies — is another critical step in improving software supply chain security. The pervasive use of open source software makes this problem particularly challenging.
While working together with the broader community on establishing guidelines and frameworks to increase open source security as a whole, we are also bringing more services to help address this challenge directly. In May, we introduced Assured Open Source Software service, currently in Preview. Assured OSS is Google’s first “curated” open source where we are adding a layer of accountability on top of today’s free or “as-is” open source. A key part of the Software Delivery Shield solution, Assured OSS provides access to open source software packages that have been curated and vetted by Google. These packages are built in our secured pipelines and are regularly scanned, analyzed, and fuzz-tested for vulnerabilities. With Assured OSS, the security team can be much more confident knowing their developers are using vetted open source dependencies. This service now provides over 250 curated packages across Java and Python, with verified provenance. It automatically generates Software Bill of Materials (SBOM) – an inventory of all components and dependencies involved in the application development and delivery – identifying where there could be a potential risk.
With Software Delivery Shield, DevOps teams can store, manage and secure the build artifacts in Artifact Registry, and also proactively detect vulnerabilities with the integrated scanning provided by Container Analysis, to which we’ve added support for more language packs. In addition to scanning the base images, it can now do on-push vulnerability scanning of Maven and Go containers, as well as for non-containerized Maven packages (currently in Preview).
Lock down the CI/CD pipeline
Bad actors can attack software supply chains by compromising CI/CD pipelines. That’s why we’re always working to strengthen the security posture of our CI and CD platforms – Cloud Build, our fully managed CI platform, and Cloud Deploy, our fully managed CD platform. As key parts of the Software Delivery Shield solution, both platforms come with built-in security features such as granular IAM controls, VPC Service Controls, isolated and ephemeral environments, and approval gates to help DevOps teams better govern the build and deployment process.
Cloud Build now officially supports SLSA Level 3 builds, implementing SLSA level 3 best practices by default. In addition to providing ephemeral and isolated build environments, Cloud Build can now generate authenticated and non-falsifiable build provenance for both containerized applications and non-containerized Maven and Python packages, as well as display security insights for built applications.
Help protect applications in production
Strengthening the security posture of the runtime environments is another critical part of securing the software supply chain. Google Kubernetes Engine (GKE) and Cloud Run, our leading runtime platforms for containerized applications, both come with baked-in security features to help protect applications while they are running.
We’re excited to announce new built-insecurity posture management capabilitiesfor GKE, currently in Preview, to help identify and fix security concerns in GKE clusters and workloads. Based on industry standards and the GKE team’s security expertise, GKE now provides detailed assessments, assigns severity ratings, and advises on the security posture of the clusters and workloads, including insights into OS vulnerabilities and workload configurations.The GKE dashboard now clearly points out which workloads are affected by a security concern and then provides actionable guidance to address it. Beyond the dashboard, GKE can also log security posture concerns to Cloud Logging, while security event information can be routed to services like the ticketing systems or a security information and event management (SIEM) system through Pub/Sub eventing.
For customers of our Cloud Run serverless platform, we are introducing new enhancements to Cloud Run’s security panel. It now displays software supply chain security insights such as SLSA build-level compliance info, build provenance, and vulnerabilities found in running services (currently in Preview).
Build a chain of trust through policy
Beyond enhancing the security posture at each stage of the software delivery lifecycle, Software Delivery Shield features a trust-based policy engine to help establish, maintain, and verify a chain of trust across the entire supply chain.
Binary Authorization is a deploy-time security control that can ensure only trusted container images are deployed on GKE or Cloud Run. With Binary Authorization, DevOps or security teams can require images to be signed by trusted authorities during the development process and then enforce signature validation when deploying. By enforcing validation, they can gain tighter control over the container environment by ensuring only verified images are integrated into the build-and-release process.
Get started today
Software supply chain security is a complicated challenge. Software Delivery Shield offers an end-to-end solution to help protect the integrity of software from attacks that can take many shapes and forms along the software supply chain. With this collection of tools across many of our cloud services, organizations can get started today and incrementally adopt better security measures, big or small, based on existing environment and security priorities, towards holistic software supply chain security.
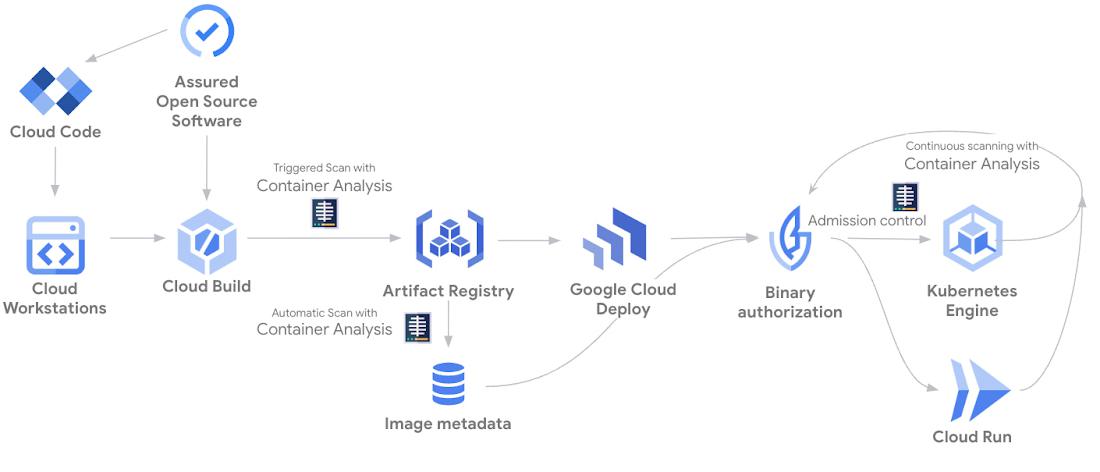
Different services of Software Delivery Shield work together to help protect your software supply chain from development to production.
- To learn more about Software Delivery Shield, check out the solution page, and follow the doc links there to get started right away and activate any of the relevant products and capabilities within the toolset.
- Watch this Next ’22 session to get a quick overview of Software Delivery Shield.
- To try out capabilities that are currently in Private Preview, please fill out this form.
- If you are interested in learning more about software supply chain security in general, please contact us or reach out to your sales representative to schedule a software supply chain security workshop.
By: Michael McGrath (VP of Engineering, Application Ecosystem)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!




