Google Cloud Storage Transfer Service (STS) enables you to move or backup your data to a Cloud Storage bucket or POSIX file system. It offers flexibility and allows horizontal scaling, encryption and checksum verification. In most cases, storage administrators use this to migrate the whole file system including all files with different access rights.
It can be challenging to migrate data in a multi-tenant storage environment when users need to make sure POSIX access is observed. Transfer tool has to be able to transfer only what is allowed. Although the STS operates under root privileges, there are ways to apply access control to the transfer agent(s). Users / Storage administrators can transfer data with the peace of mind that POSIX access rights are being enforced during the transfer operation
From our partners:
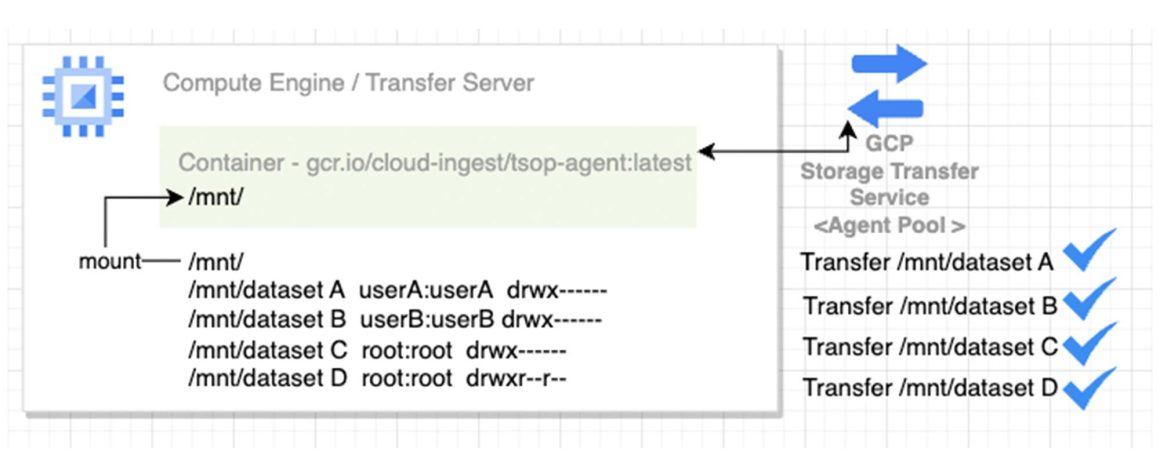
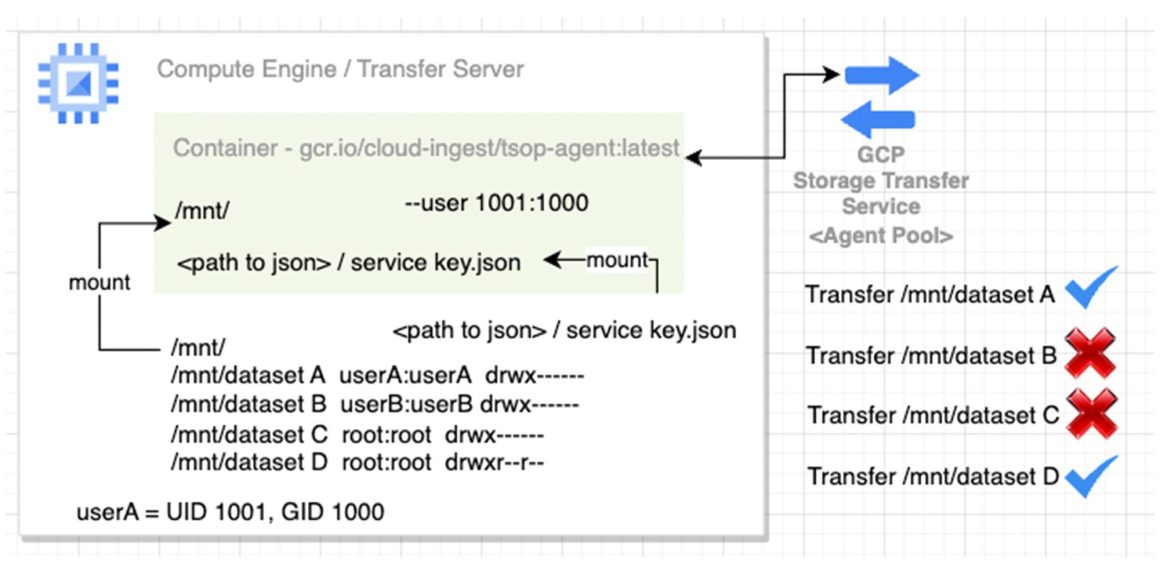
Without the mount / permission setup, the transfer agent(2) can transfer any data within the mount. In the setup shown in the diagram, an agent mounted at /mnt/ can transfer data from all the underlying directories – datasetA, datasetB, datasetC, and datasetD to Cloud Storage.
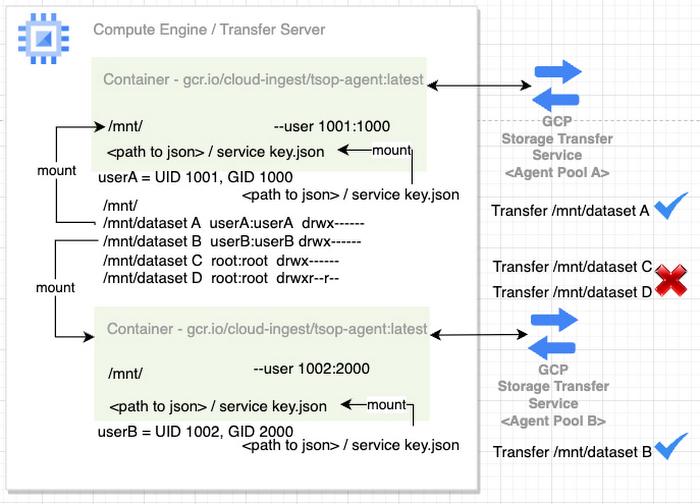
If you need to set up the transfer service for a specific group of users in a multi-tenant NAS / NFS storage environment, you need to limit the access to data which does not belong to the group by using specific mount / POSIX user account permissions. Multiple set up can be done with different POSIX user account permissions for different groups.
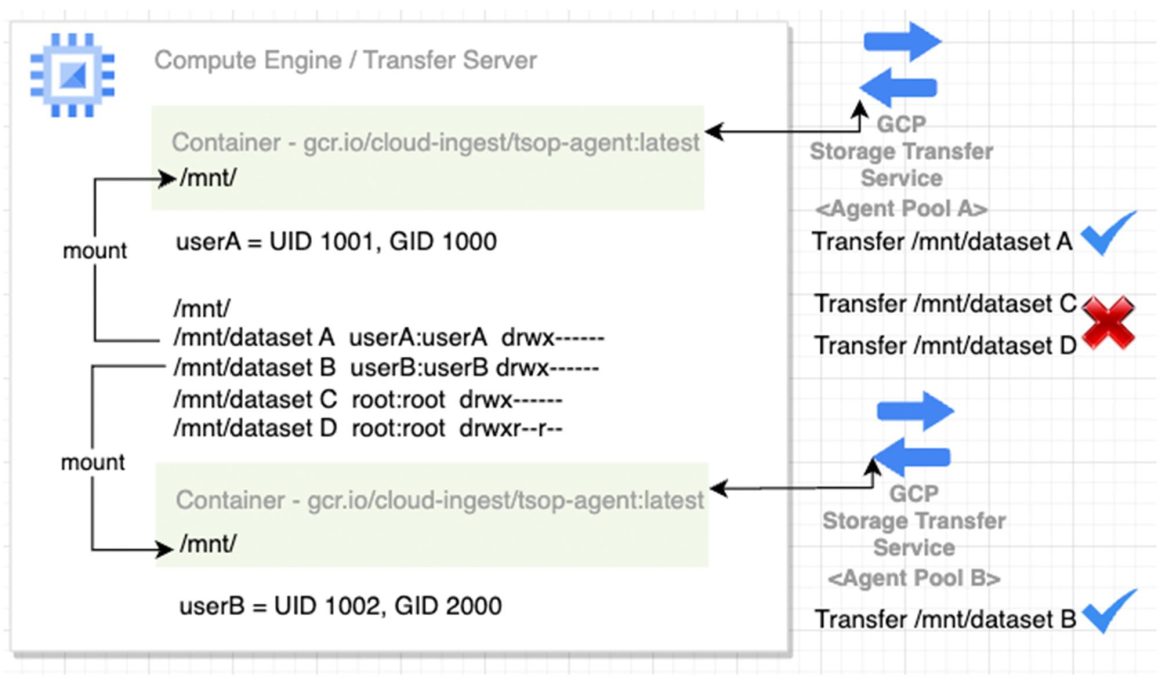
With permission and / or mount setup shown in the diagram, specific agent(s) can only transfer data from its specific mount and the underlying directories to Cloud Storage. All agent(s) in Agent Pool A can only access data from /mnt/dataset A. They do not have access to other dataset B C and D. Also, All agent(s) in Agent Pool B can only access data from /mnt/dataset B. They do not have access to dataset A, C and D.
Access control methods overview:
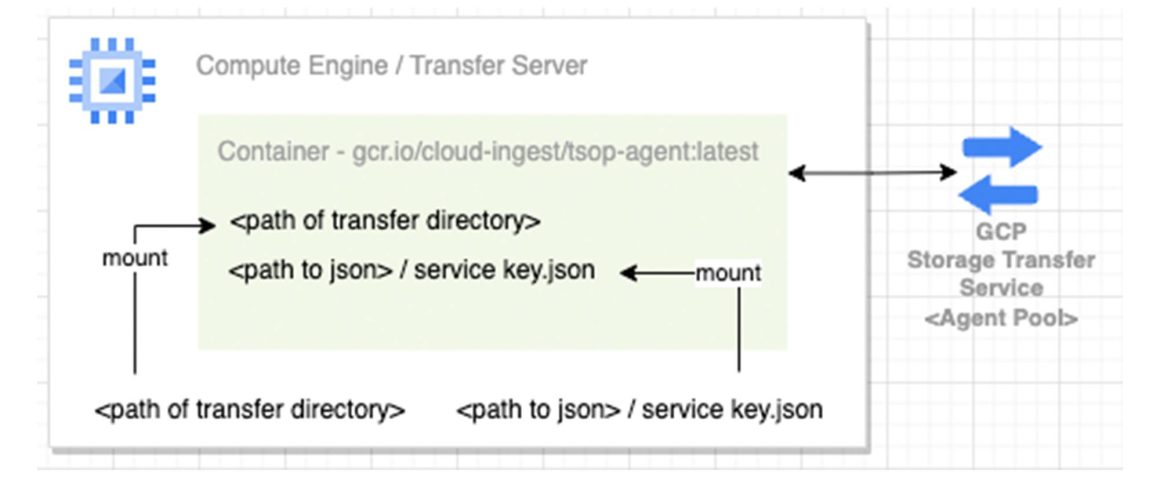
Set up the container(s) as transfer agent(s)
There are two methods to limit transfer agent(s) access right to data. Both access control methods can be used solely or combined.
- Mount
- POSIX user account permission
Mount – By specifying the directory in the mount option at the container, transfer service
CANNOT access data outside of the mount location. Even if the transfer node / VM has access to the directory, data cannot be accessed if it is not mounted to the docker container / agent.
Advantage: In a large file system, projects are most likely being organized in directory structure. By mounting a specific directory to the agent, the agent pool can target specific project data.
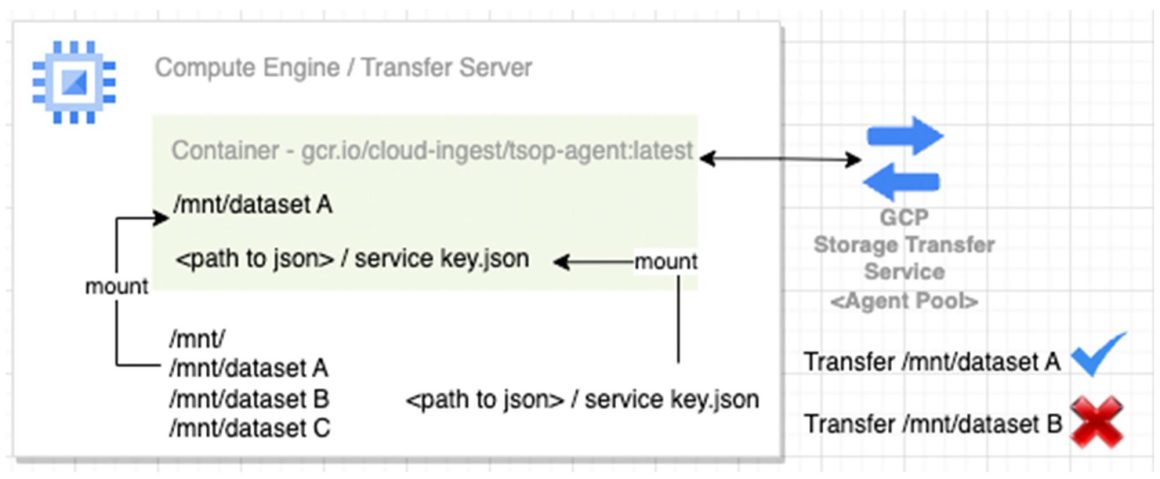
POSIX user account permission – Although agent(s) may have access to the top of the directory, access is limited based on the POSIX user account permission.
Advantage: In a multi-tenant environment, administrators can limit the user access with POSIX permissions.
Agent Setup Commands:
Here is the example command to setup the the transfer agent with Mount / POSIX user account permissions:
Setup the service account json key
gcloud iam service-accounts keys create service_account.json --iam-account=<service account name>
Setup the transfer agent:
docker run --ulimit memlock=64000000 -d --rm -v <directory to be transferred>:<directory to be transferred> -v <path to the service account key>/service_account.json:<path to the service account key>service_account.json --user 1000:1001 gcr.io/cloud-ingest/tsop-agent:latest --project-id=thomashk-migration1 --creds-file=<path to the service account key>service_account.json --hostname=$(hostname) --agent-pool=<name of the agent pool>
Mount: using the “–user uid:gid”, this will setup the POSIX user permission.
POSIX user account permission: Using the -v <directory to be transferred>:<directory to be transferred>
Error message shown if transfers directory without permission:
The following error will show up:
Error message:
202x-11-23T10:10:10Z transferOperations/xxxx_transferJobs/OPI476239788276320xxx_000000000166923xxxx FIND FAILED PERMISSION_FAILURE PERMISSION_DENIED failed to list the contents of directory “/etc/ssl/private/”. open /etc/ssl/private/: permission denied
You can set up the multiple transfer agents with access control in a multi-tenant NAS environment:
Google Cloud Storage Transfer Service does not only offer you the ability to move or backup data to the Cloud Storage bucket. The common use cases include transfer between Cloud Storage Buckets, Move Cloud Storage data to another location and Transfer data between file systems. Please refer to the link for future reference and documentation.
By: Thomas Leung (HPC Technical Solution Consultant, Professional Service Organization, Google Cloud)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!








