Most of us are now living the connected life. The Internet has become an indispensable tool in our modern lives. We use it for communication, entertainment, education, business, and other multitudes of everyday tasks. But the Intenet’s benefits also come with a caveat. Privacy is one of the top concerns and people with ill-intent want to collect and steal data from users.
Here are some quick ways to make sure that your online privacy is protected :
From our partners:
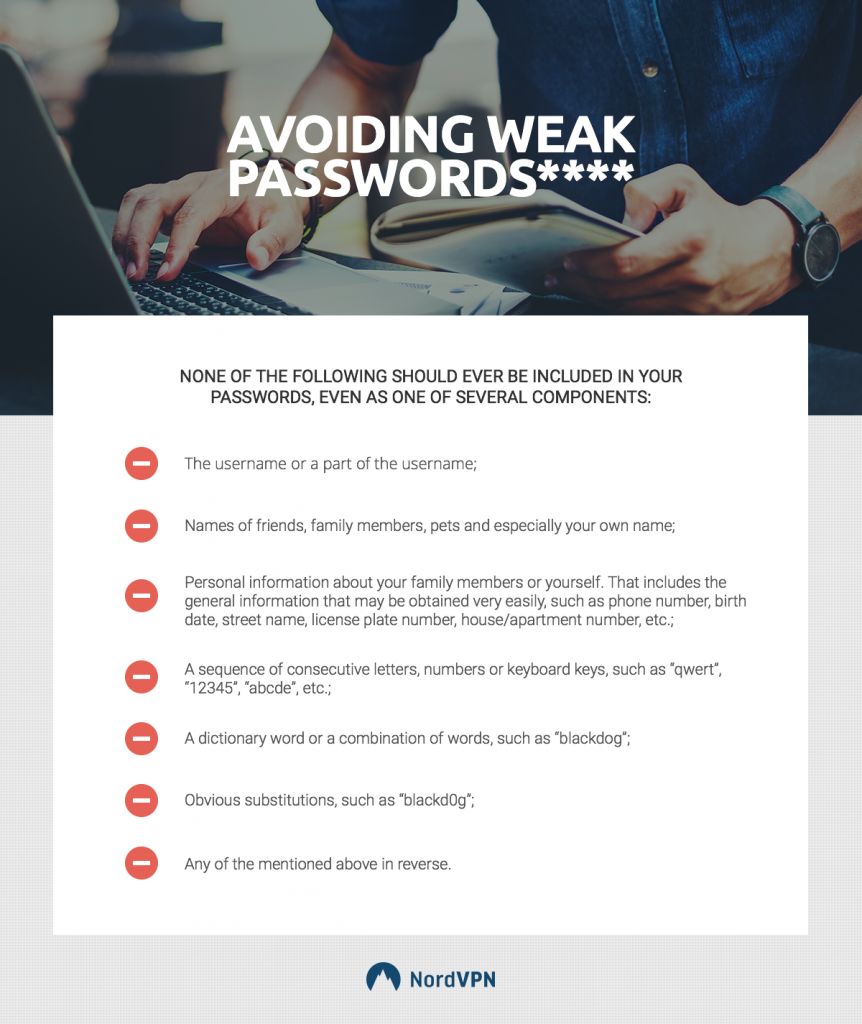
01: Avoid Weak Passwords
Weak passwords are often exploited by hackers and thieves. Check out this guide to ensure that your password is secure:
02: Do Not Immediately Give Out Your Personal Info
The Internet is teeming with sites that inadvertently asks you for your email or personal details or encourage you to immediately signup to their services. Do not be quick to hand out your info. Double check the site first and read their terms and conditions if possible to be sure. If a company or an institution asks for your contact info, double check them first or call them to verify.
03: You Don’t Have To Share Everything In Social Media
Without being fully aware of it, users may be sharing a bit too much of their personal information on their social media accounts. You may be posting your location or displaying photos that are not meant for public viewing. Double check if location services are enabled on your mobile phones for your social network accounts and disable them. In Facebook, you can also control what other users can see on your account. You can check out Facebook’s tool to assess your account’s privacy.
04: Refrain From Connecting To Public WiFi
Update the settings of your devices so that you don’t immediately connect to public networks. As convenient as they may be, refrain from connecting to public wifi as they are a common hotspot for hackers. If you need to use it make sure that you are secured with a VPN.
05: Secure Your Devices With PINs & Passwords
Make sure to lock your devices’ screens when not in use. Use a PIN on your mobile phones and a password on your laptops to ensure that no unauthorized person handles your device.

06: Keep Your Software Updated
Be sure to run to those updates regularly especially the ones with security enhancements or patches included. It may be annoying to see popups of update while you’re in the middle of binge-watching a series, playing games or doing something else on your device but no matter how annoying it may be just run those updates.
07: Back Up Your Data
Keep an updated backup of your files on a secure drive or location. In case someone hacks your data you can still recover your files from your backup. For Mac users, setting up a Time Machine backup is a quick and easy way to secure your files.
08: Use A Virtual Private Network (VPN)
A virtual private network like NordVPN sends your online traffic through a remote server within a worldwide network of secure VPN servers. This way, your real IP address is changed, and your online traffic is snoop-proof. NordVPN keeps no logs of your Internet activity along the way, so you can surf the web without leaving a trace. Signup with NordVPN now and get an exclusive 75% discount.
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!