Overview
This guide will show you how to install and configure an FTP(s) server in CentOS.
From our partners:
Prerequisites
- Operating System of (s)FTP server : CentOS 7
Installation
01. Update the system package resources
$ sudo yum update
02. (Optional) Install nano, a simple text editor. Or use the default editor “vi”.
$ sudo yum install nano -y
03. Install the SFTP package
$ sudo yum install vsftpd -y
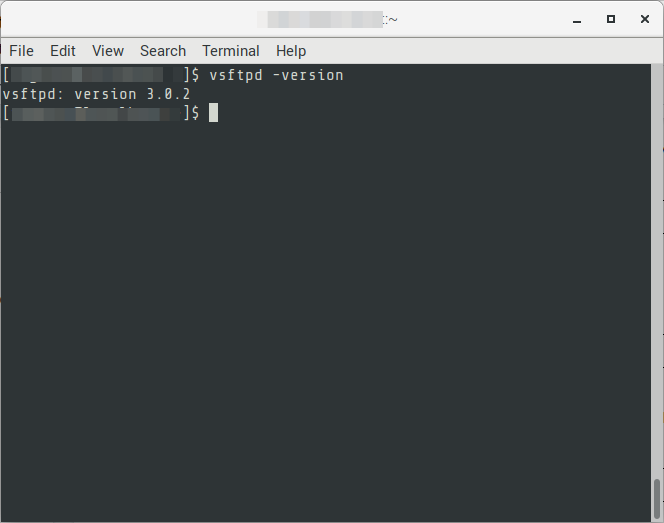
04. Verify that Very Secure FTP (VSFTP) has been installed by checking the version.
$ vsftpd -version
05. Start the service, since it is disabled by default
$ sudo systemctl start vsftpd
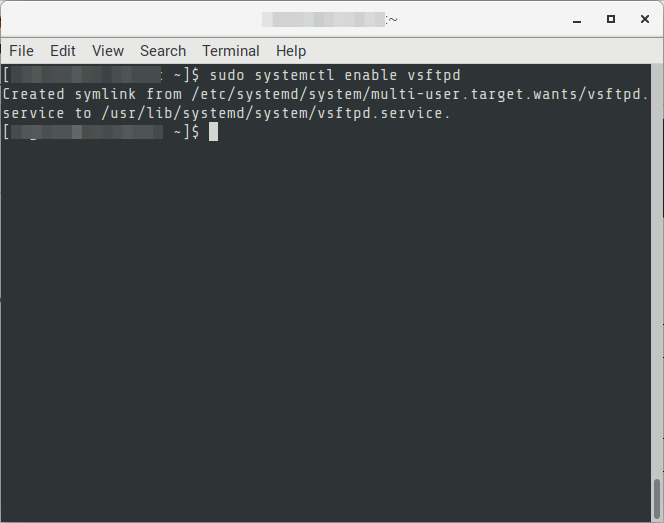
06. Set the service to automatically start on boot
$ sudo systemctl enable vsftpd
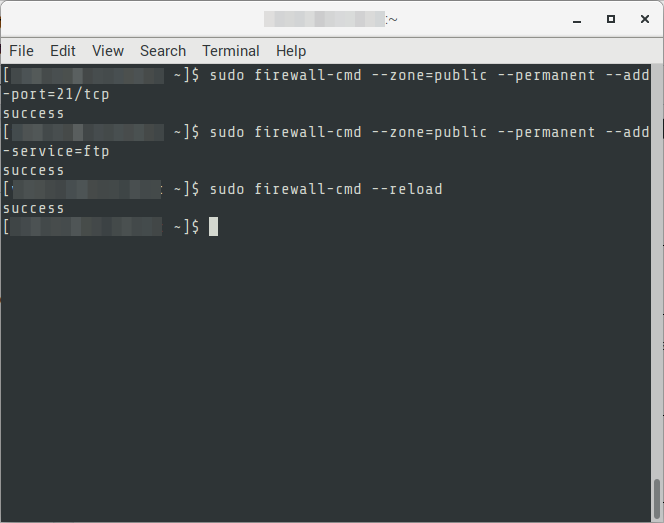
07. Create the firewall rules to allow FTP traffic on Port 21.
$ sudo firewall-cmd --zone=public --permanent --add-port=21/tcp $ sudo firewall-cmd --zone=public --permanent --add-service=ftp $ sudo firewall-cmd --reload
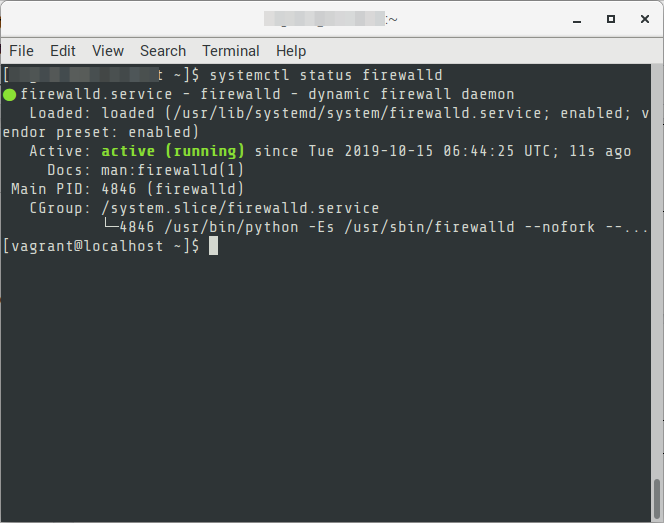
If an error saying that “FirewallD is not running” execute the following first then retry the commands
$ sudo systemctl enable firewalld $ sudo systemctl start firewalld # Check that the service is running $ systemctl status firewalld
Configuration
01. Backup the original version of the VSFTP configuration
$ sudo cp /etc/vsftpd/vsftpd.conf /etc/vsftpd/vsftpd.conf.original
02. Edit the configuration file
$ sudo cp /etc/vsftpd/vsftpd.conf /etc/vsftpd/vsftpd.conf.original
03. For FTP access for registered users. Applicable for registered Users with Password or SSH (or SFTP).
| anonymous_enable | NO
When enabled non-registered users will be able to access the FTP service. Set the value as “NO” to not allow anonymous access. |
| local_enable | YES
Set value as “YES” |
| write_enable | Value: YES
Uncomment this setting. Set value as “YES” |
| chroot_local_user | Value: YES
Uncomment this setting. Limit the FTP users to their own directory. Set value as “YES” |
| chroot_list_file | Value: /etc/vsftpd/chroot_list
Uncomment this setting and set the value as “/etc/vsftpd/chroot_list”. |
Add the following configurations at the bottom.
| …
userlist_file=/etc/vsftpd/user_list userlist_deny=NO … |
04. Restart the service to apply the changes
$ sudo systemctl restart vsftpd
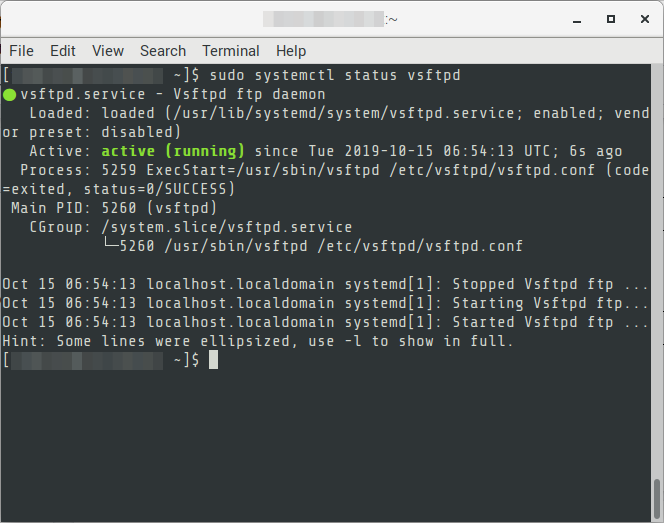
05. Check the status of the service to see if there are errors.
$ sudo systemctl status vsftpd
Configuration – SSL / FTPS
To secure the FTP with SSL/TLS certificate use the following steps. Note that if SSL is configured, anonymous access via Username and Password will not be allowed if you perform the following steps. Only SFTP or registered user with SSH keys configured will be allowed.
Also note that you can also provide or install your own/bought SSL certificate. In this example we will be creating a self-signed certificate.
01. Create the directory to place the SSL file
$ mkdir /etc/ssl/private/
02. Create a new certificate or ignore this and install/copy your own certificate. You will be asked for details on the SSL, this is also standard process if you bought an SSL certificate.
$ sudo openssl req -x509 -nodes -keyout /etc/ssl/private/vsftpd-selfsigned.pem -out /etc/ssl/private/vsftpd-selfsigned.pem -days 365 -newkey rsa:2048
Explanation for the parameters used
- req – is a command for X.509 Certificate Signing Request (CSR) management.
- x509 – means X.509 certificate data management.
- days – validity for the certificate, number of days before it expires
- newkey – flag saying this is a new key
- rsa:2048 – RSA key processor, will generate a 2048 bit private key
- keyout – sets the key storage file
- out – sets the certificate storage file
03. Enable the TCP port in the firewall
$ sudo firewall-cmd --zone=public --add-port=990/tcp --permanent # For passive mode $ sudo firewall-cmd --zone=public --add-port=40001-40100/tcp --permanent # Apply the changes $ sudo firewall-cmd --reload
04. Open the VSFTP configuration for editing
$ sudo nano /etc/vsftpd/vsftpd.conf
05. Add the following at the end of the file
# SSL configuration (TLS v1.2) ssl_enable=YES ssl_tlsv1_2=YES ssl_sslv2=NO ssl_sslv3=NO # configure the location of the SSL certificate and key file rsa_cert_file=/etc/ssl/private/vsftpd-selfsigned.pem rsa_private_key_file=/etc/ssl/private/vsftpd-selfsigned.pem # prevent anonymous users from using SSL allow_anon_ssl=NO # force all non-anonymous logins to use SSL for data transfer force_local_data_ssl=YES # force all non-anonymous logins to use SSL to send passwords force_local_logins_ssl=YES # Select the SSL ciphers VSFTPD will permit for encrypted SSL connections with the ssl_ciphers option. ssl_ciphers=HIGH # turn off SSL reuse require_ssl_reuse=NO pasv_min_port=40001 pasv_max_port=40100 # For debug Purpose debug_ssl=YES
06. Restart the service to apply the changes
$ sudo systemctl restart vsftpd
07. Check the status of the service to see if there are errors.
$ sudo systemctl status vsftpd
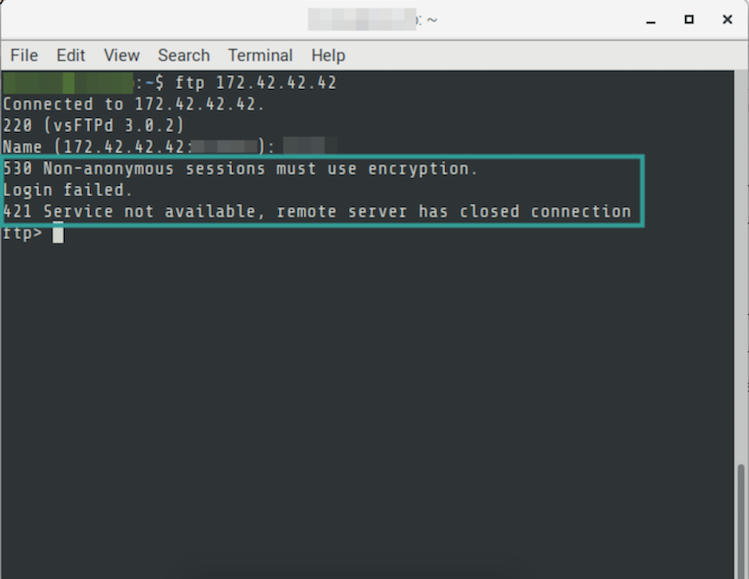
If you try to access the FTP server when using a client that does not use encryption. You will get the following message. Solution for this is to use an account with SFTP (User with SSH key) or FileZilla.
Adding an FTP User
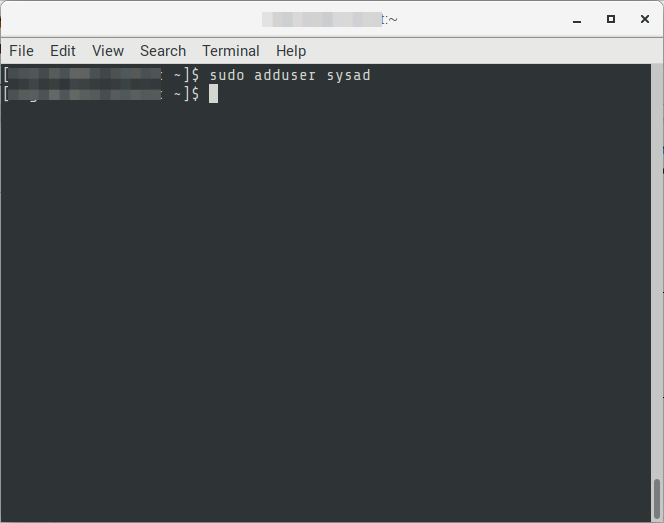
01. Create a new FTP user
Note that using SSH requires the SSH service running. If it is not installed, follow the instructions here on how to install it.
# FORMAT
$ sudo adduser {{username}}
# EXAMPLE
$ sudo adduser sysad
Switch to the new user
# FORMAT
$ sudo su - {{username}}
# EXAMPLE
$ sudo su - sysad
Create SSH directory and update the permissions
$ cd ~ $ mkdir .ssh $ chmod 700 .ssh $ nano .ssh/authorized_keys
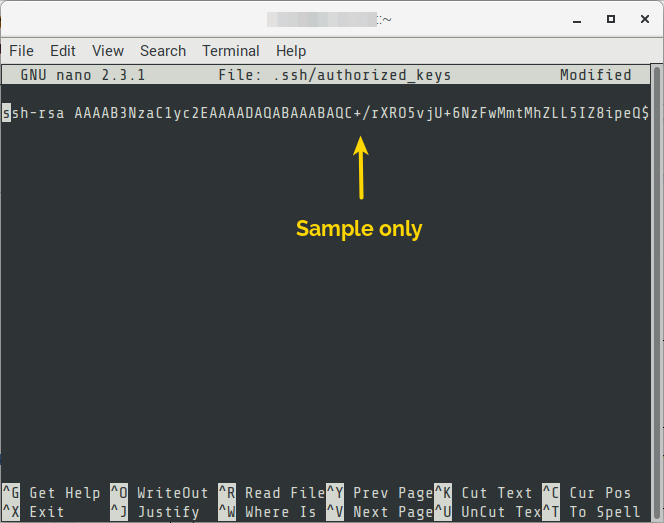
Set the content of the file with the public key of the user. It should contain something like. You can generate new key using online tools like the one here.
Update the permission of the authorized key
$ chmod 600 .ssh/authorized_keys
Exit from the user session.
$ exit
Restart the SSH service
$ sudo service sshd restart
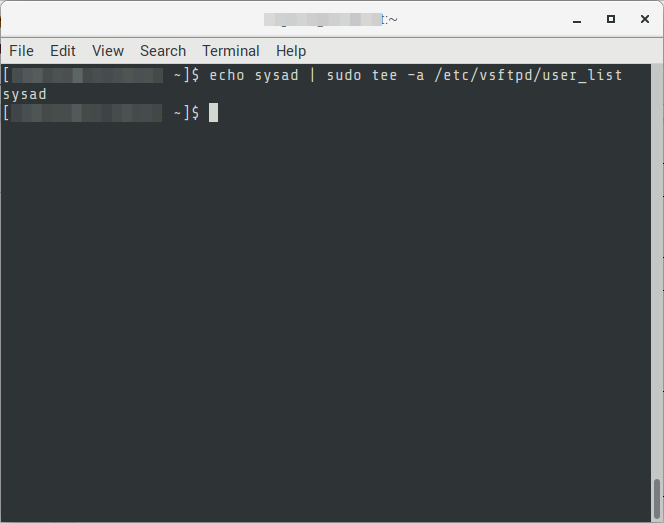
02. Add a new user to the list FTP users.
# FORMAT
$ echo {{username}} | sudo tee –a /etc/vsftpd/user_list
# EXAMPLE
$ echo sysad | sudo tee –a /etc/vsftpd/user_list
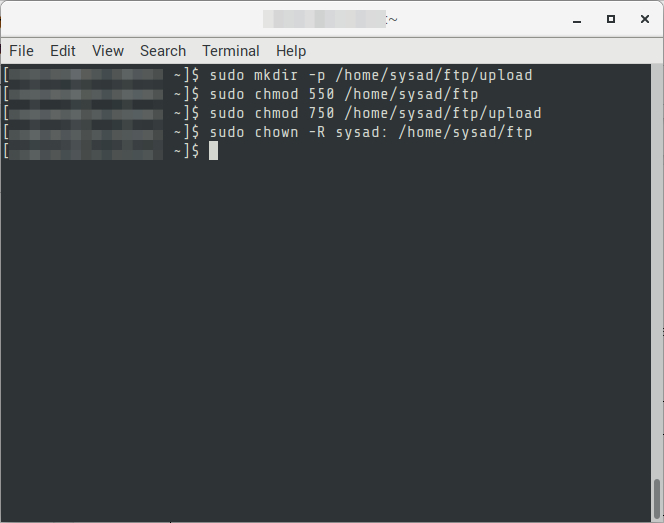
03. Create the directory for the new user, and update the permissions. The following is only a sample structure for the user. Depending on the directory structure is designed the steps may be different. It will also disable accessing of the user directories from other users.
# FORMAT
$ sudo mkdir –p /home/{{username}}/ftp/upload
$ sudo chmod 550 /home/{{username}}/ftp
$ sudo chmod 750 /home/{{username}}/ftp/upload
$ sudo chown –R {{username}}: /home/{{username}}/ftp
# EXAMPLE
$ sudo mkdir -p /home/sysad/ftp/upload
$ sudo chmod 550 /home/sysad/ftp
$ sudo chmod 750 /home/sysad/ftp/upload
$ sudo chown -R sysad: /home/sysad/ftp
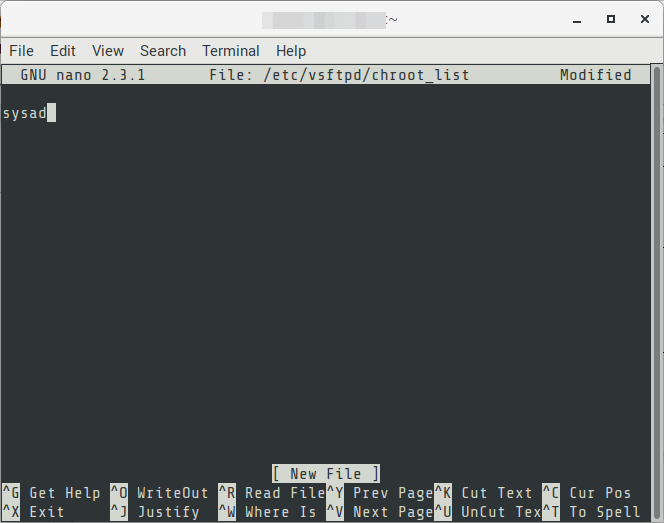
04. Create or update the chroot user list. These are the users who are “jailed”, meaning they can only access their own folders.
$ sudo nano /etc/vsftpd/chroot_list
Add the user to the file
# FORMAT
{{username}}
# EXAMPLE
sysad
Removing an FTP User
01. Access the server and execute the following command to remove the user. Add an “-r” before the username to remove the user files.
# FORMAT
$ sudo userdel {{username}}
# EXAMPLE
$ sudo userdel sysad
Remove also the user file.
# FORMAT
$ sudo userdel -r {{username}}
# EXAMPLE
$ sudo userdel -r sysad
Accessing the FTP Server
Via CLI (Ubuntu)
Registered User with SSH key
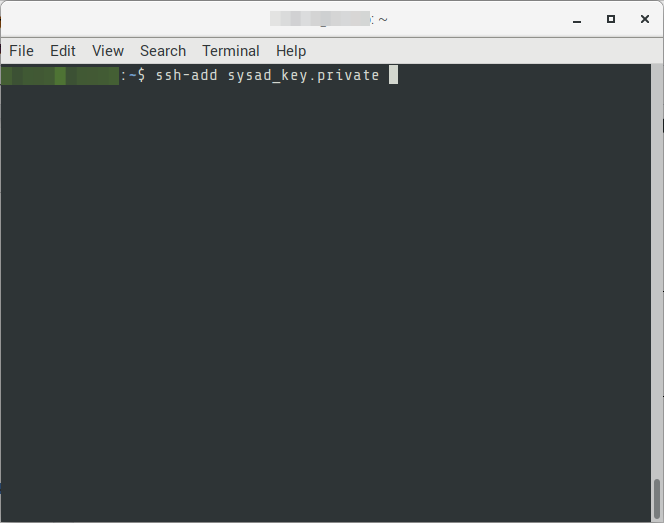
01. Add the Private key to the SSH session
# FORMAT
$ ssh-add {{private-ssh-key}}
# EXAMPLE
$ ssh-add sysad_key.private
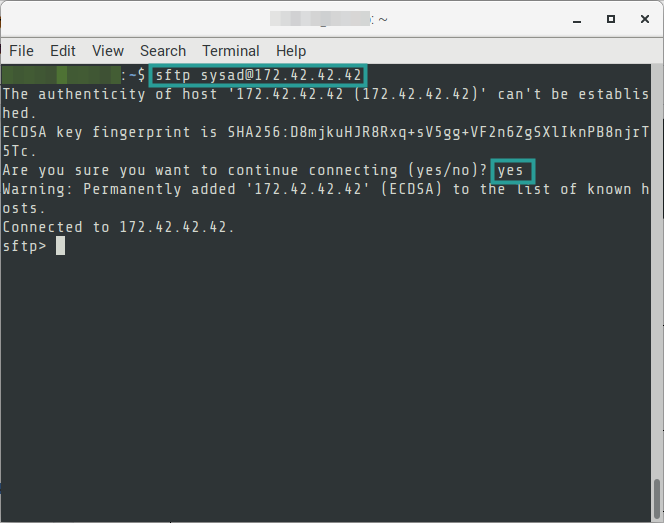
02. Login via SFTP. Accept the fingerprint confirmation the first time this command is executed.
# FORMAT
$ sftp {{username}}@{{hostname-or-ip-address}}
# EXAMPLE
$ sftp [email protected]
03. To list the files and folders of the current working directory.
$ ls -l
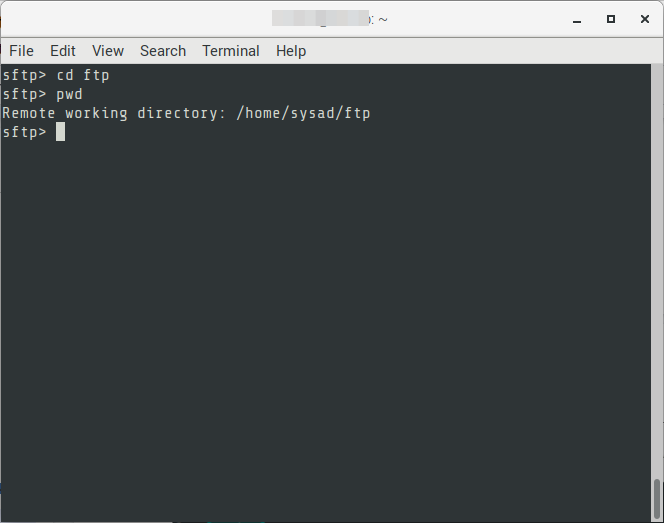
04. To change to a directory use “cd”, and use “pwd” to see the current directory.
# FORMAT
$ cd {{sub-directory}}
# EXAMPLE
$ cd ftp
05. To download a file from the FTP server
# FORMAT
$ get {{file-name}}
# EXAMPLE
$ get sample.txt
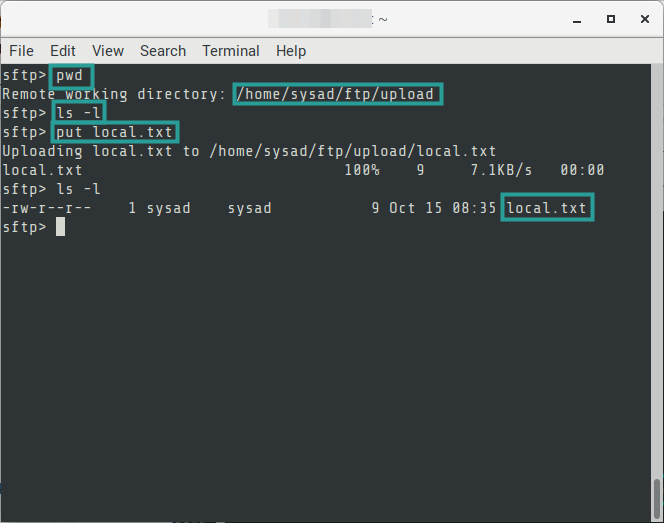
06. To upload a file to the FTP server. Note that the files you can upload are dependent on the directory where you performed the FTP login. You can also specify an absolute path of the file or directory you want to upload.
# FORMAT
$ put {{file-name}}
# EXAMPLE
$ put sample.txt
Via FileZilla
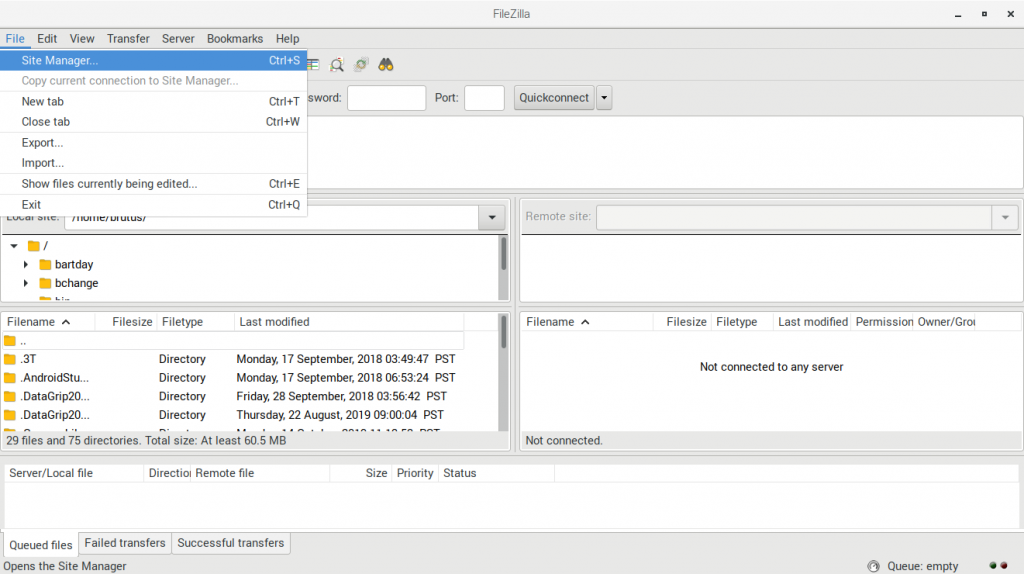
01. On the “File” menu, select “Site Manager”.
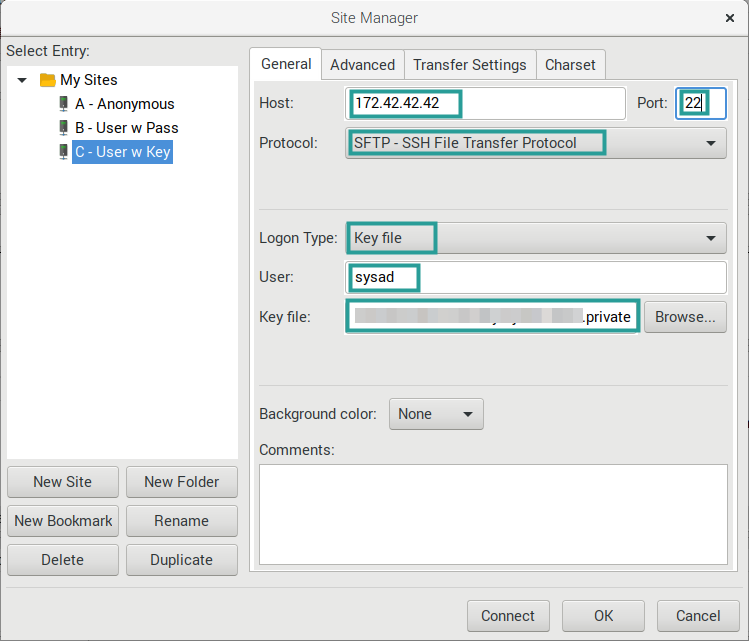
02. Create a new site, and set the settings as follows. Then click on the “Connect” button.
| Host | “{{ip-address-or-hostname}}”
IP Address or Hostname of the FTP server |
| Port | “22”
SFTP Port, 22 is the default |
| Protocol | “SFTP – SSH File Transfer Protocol” |
| Logon Type | “Key file” |
| User | “{{os-username}}”
Example: sysad |
| Key file | “{{key-file-path}}”
Key file in PPK format. |
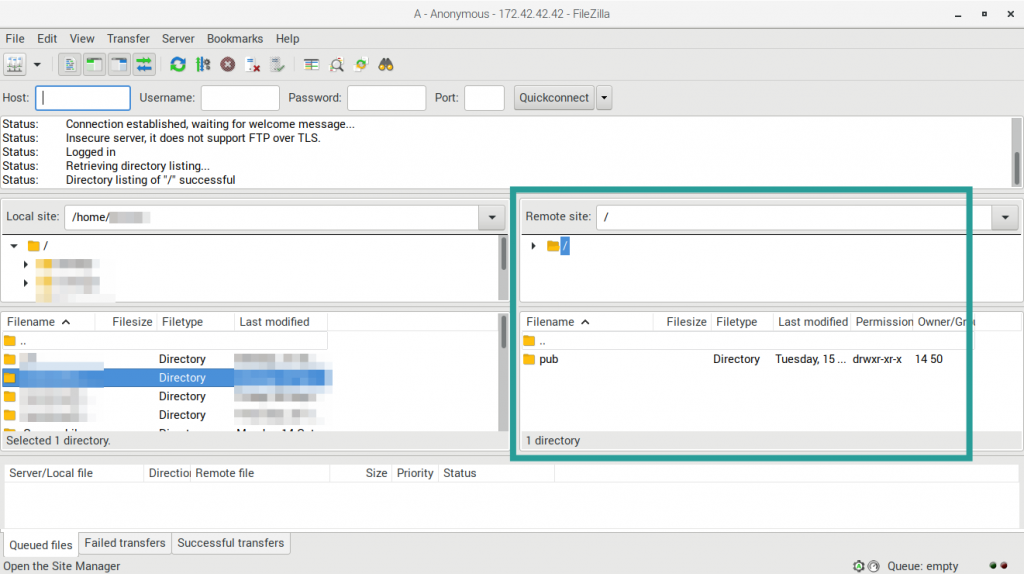
03. On successful authentication, the remote FTP server and its accessible folders will be visible.
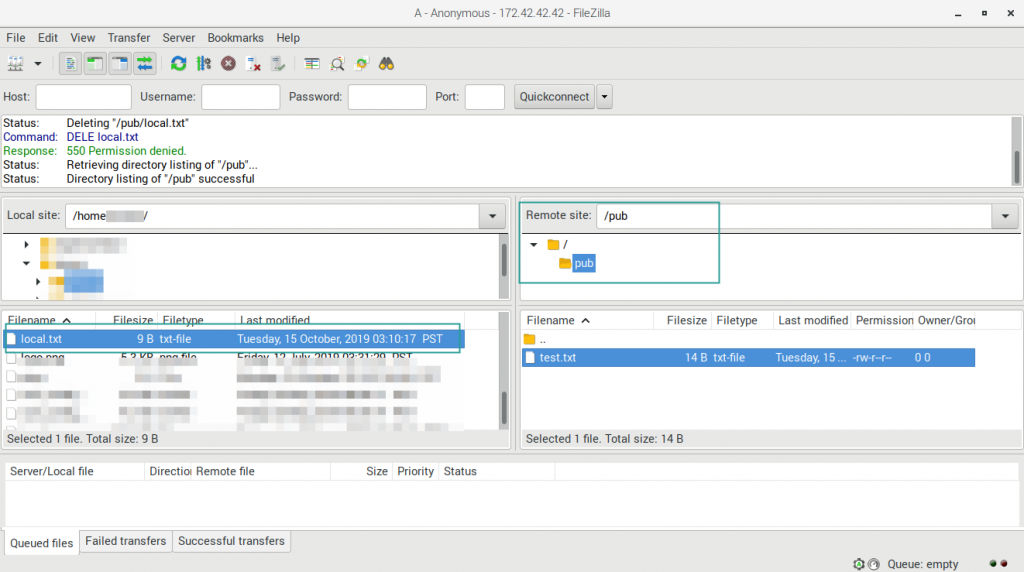
For the anonymous user with accessible “pub” directory:
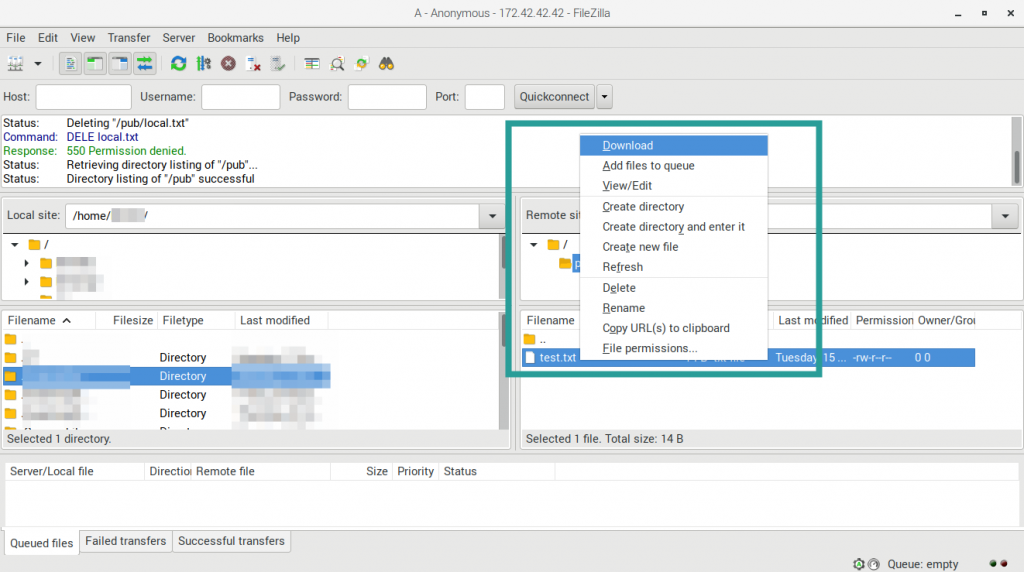
04. To download a file on the right side, there is “Remote site” section that looks like a file system directory and files. Select a file, then right-click to open the context menu. Then select “Download”. The file will be downloaded on the current value of the “Local site” on the left section.
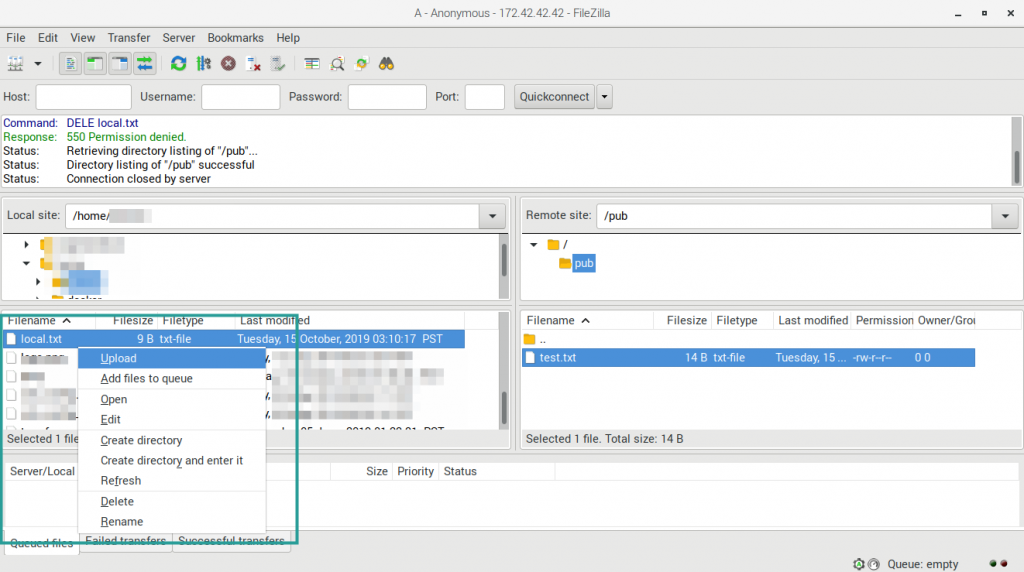
05. To upload a file. Select or navigate the value what file you want to upload on the “Local site”. Then select or navigate the directory for the destination on the “Remote site”. Select the file from the “Local site”, right-click, then select “Upload”.
Select file from local
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!