When the man who invented passwords says it’s time to move on, it probably is. Four years ago, Fernando Corbato, who invented the first computer password in the 1960s, said that passwords had become “a nightmare”. Considering that his creation was not intended for the web, how data breaches have shaped the digital era, and the rise of privacy-awareness, it’s clear that things need to change.
Passwords were once one of our most trusted security measures, but over the past decade, the average person’s digital footprint has been exposed to increasing numbers of third parties. Now the average consumer manages over 191 pairs of usernames and passwords. It is almost guaranteed that people reuse the same passwords or tactics to authenticate across various services.
From our partners:
What’s wrong with passwords?
Most of the recent data breaches stem from stolen passwords. As digital platforms pile up gigabytes of data, including personal information and the credentials we use to get access to their digital services, the cost of attacks for hackers has decreased significantly. You can now buy login credentials to someone’s bank or Uber account on the dark web for as little as $7. Knowledge-based authentication, whether with PINs, passwords, passphrases, or whatever we need to remember, are not only a major headache for users – they cost a lot of money to maintain. Without even looking at the costs of a cyberattack, the mere costs of password management, of time lost by employees typing passwords and chasing the IT department when they fail, can climb up to $70 per incident. And with up to 50% of all help-desk calls being password resets, the costs can mount up quickly.
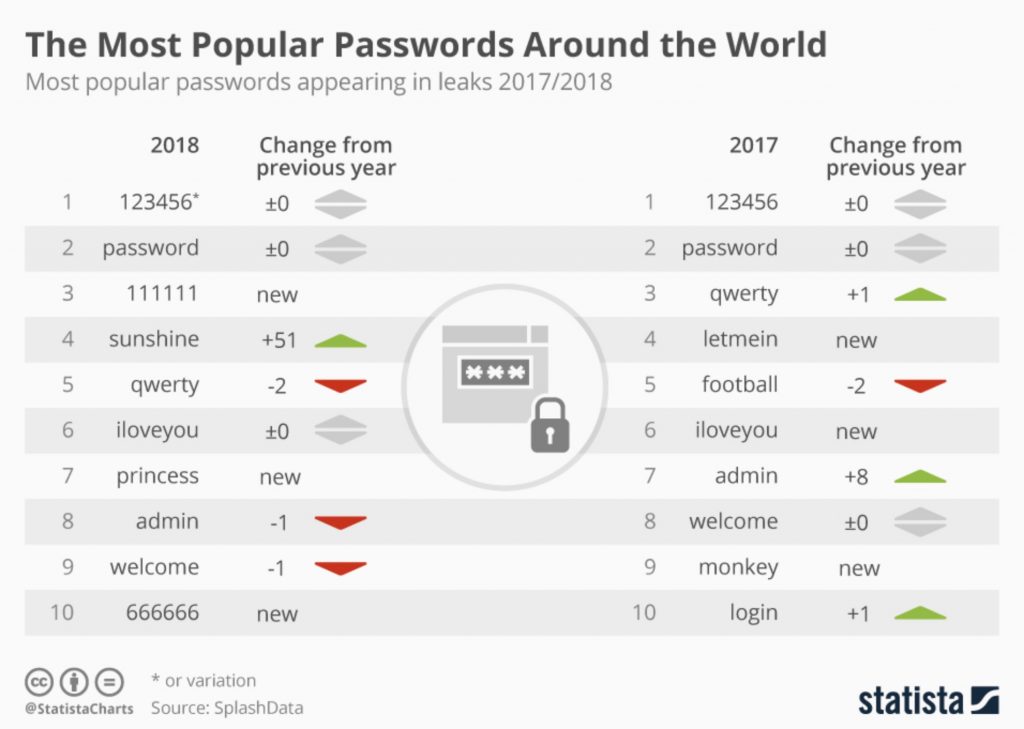
Passwords aren’t just difficult to manage, they are inconvenient, insecure and expensive. Gartner predicts that by 2022, 60% of large businesses and all medium-sized companies will have cut their dependence on passwords by half. How?
Privacy-enhancing authentication technologies
Several trends have begun to enable the market to go passwordless and users to finally have control of their data. The first major government push has come with GDPR in Europe and the California Privacy Rights and Enforcement Act.
Consumers have become accustomed to having ‘free’ services, which are ultimately paid for from the sale of their data and without their explicit consent or knowledge – but users are starting to resist. Examples include the class action lawsuit filed against Facebook in Illinois and the Swedish data protection authority issuing its first fine under GDPR to a school for its improper use of facial recognition technology.
To meet the requirements established by these new laws, products and services must be designed with privacy at their core and provide complete transparency to their users. If services are built in this manner, we will be able to build biometrics in a trusted manner, which leaves only the question of whether companies can verify the information being submitted by their applicants. One way to solve this is with a scan of a person’s government-issued ID and a facial similarity check in combination with verified attributes.
A multistakeholder challenge that requires a multistakeholder approach
Both governments and private industry have a critical role to play in providing access to verified attributes. In 2018, the Better Identity Coalition released a report that calls for trusted government sources to open up access to the attributes they hold. Many governments have looked to help solve the problem of how to verify who someone says they are in a remote setting, with initiatives such as eIDAS in the EU, the Pan-Canadian Trust Framework, and Australia’s Trusted Digital Identity Framework.
For the world to become passwordless, we need to put users in control of their own data. This will allow the work of bodies such as the World Wide Web Consortium, which develops global standards for the web, and the Fido Alliance – an industry association dedicated to replacing passwords as our means of digital authentication – to rely on our devices and real-time attributes, so that users can verify themselves remotely and more securely.
The passwordless future is close. We will continue to see progress in 2020, but we need to act now to close the gap between trusting real-time verifications and ending our dependency on passwords. This can be done by providing a more trusted, secure, and convenient user experience, one which helps people protect how their data is being used while at the same time providing companies with access to a decentralized network to trust digital identities at scale. It will allow digital platforms to more easily onboard users between different digital services in real time, providing a trusted level of interoperability for an unparalleled user experience. Managing 191 digital accounts will become a breeze, and people will win back control of their identity.
Adrien Ogée, Project Lead, Cyber Resilience, World Economic Forum
Parker Crockford, Director of Policy & Strategic Accounts, Onfido
This article originally appeared in the World Economic Forum.
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!








