With so much information stored in the cloud, the consequences of cyber-breaches are only increasing in severity.
Some countries are better prepared than others when it comes to these threats. It is important to know the vulnerability of your own country in order to gauge if you’re doing enough when it comes to ensuring the security of the information you store in the digital world.
From our partners:
Analysing the data from Microsoft Intelligence Report, security experts from Specops collected instances of cloud provider attacks as well as encounters of cryptocurrency mining, malware, and ransomware in Europe and checked the contributions of each country.
In their published report, the following countries were revealed to be the most and least susceptible to cyberthreats:
Highlights
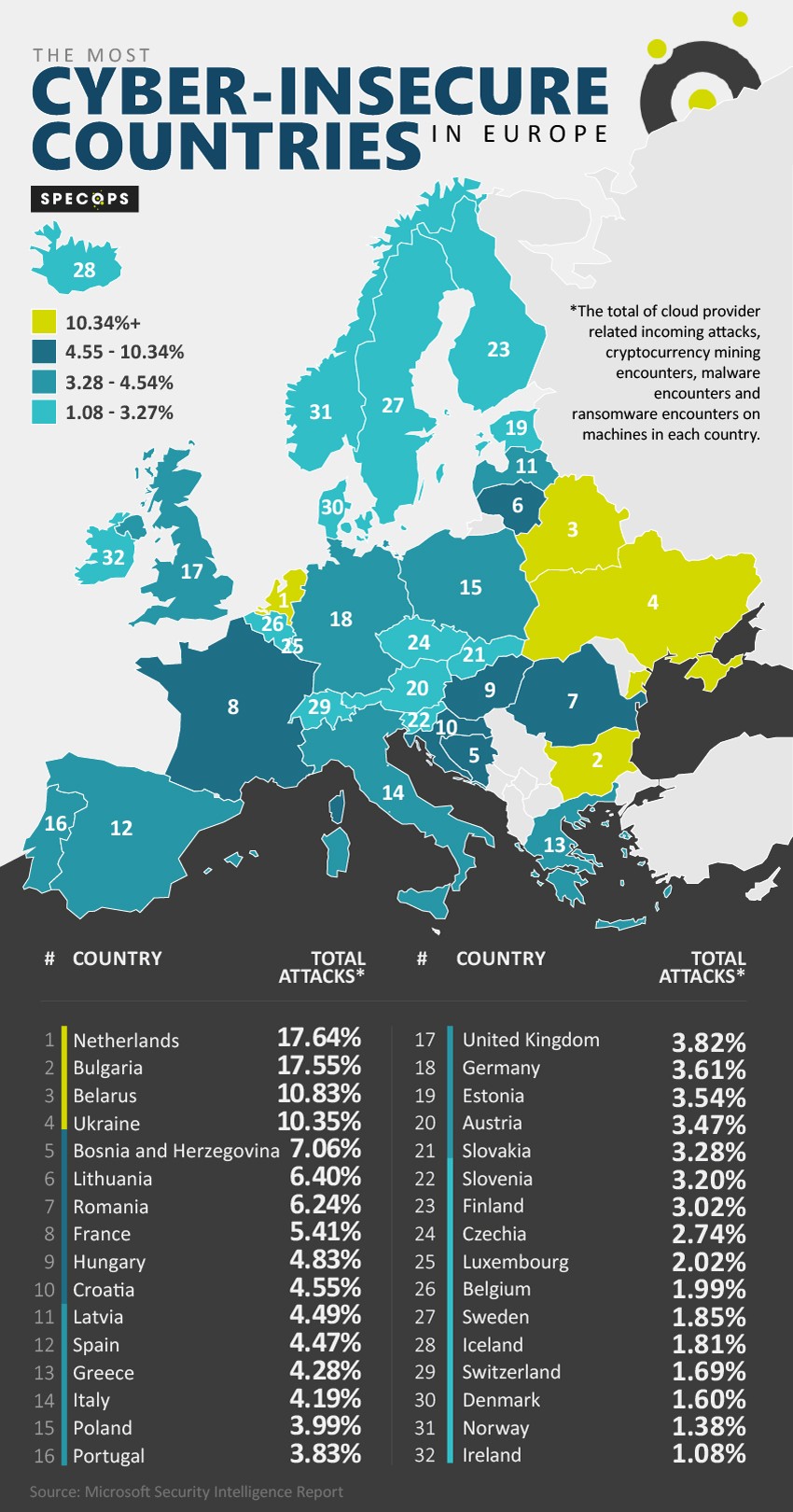
The Netherlands, with 17.64% of the total attacks, is the country most vulnerable to cybersecurity attacks for the year 2019. According to Specops, a huge contributor for the country being in the top of the list is the huge number of cloud provider attacks in the country. In fact, 16.28% of all the cloud provider attacks come from The Netherlands.
In the second spot is Bulgaria, accounting for 17.55% of the total attacks. Following it in third place is Belarus, where 10.83% of the attacks in 2019 were detected.
The fourth most vulnerable country when it comes to cyberattacks is Ukraine, where 10.35% of the attacks were recorded. In the fifth sport is Bosnia and Herzegovina, where the number of attacks amounted to 7.06% of the total number.
Together, these five countries account for more than 63% of the total observed cyberattacks in Europe in 2019.
On the flip side, the least vulnerable European country in terms of cyberattacks is Ireland, where only 1.08% of the attacks originated from. Ireland is followed by Norway (1.38%), Denmark (1.60%), Switzerland (1.69%), and Iceland (1.81%)
Staying safe
In order to stay safe, Specops recommended three steps that users can easily accomplish.
First, they advised users to refrain from reusing passwords since this makes it easy for attackers to attack all accounts once they managed to break through one. With the abundance of free password managers, keeping track of passwords and making sure that they are secure enough should no longer be a hassle.
They also recommended the use of multifactor authentication, a feature which is quite commonly offered in online services now. With multi-factor authentication, attackers cannot access an account even if they manage to know the password, thanks to the extra layer of protection.
Lastly, they also advised not to click on suspicious links. These links may be within emails that seem reliable. Some can even appear to come from people that you personally know. If you are not certain about the safety of the link, it is better not to click it at all.
For a more detailed breakdown of the cyberattacks in Europe for the year 2019, you may want to check the Specops’ report.
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!