Watch out, these applications have vulnerabilities with the highest share of exploits used by cybercriminals.
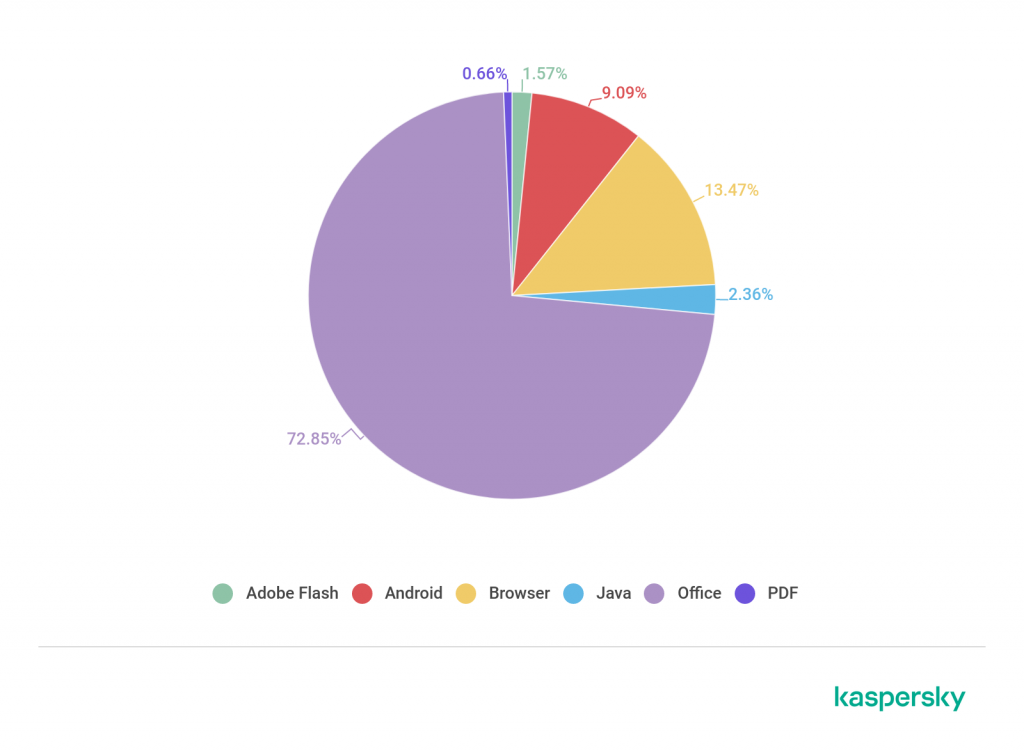
Microsoft Office Suite, Android applications, and browsers are the three most common targets of cybercriminals during cyber attacks, according to the latest analysis of the AO Kaspersky Lab which was conducted for Q3 2019.
From our partners:
These three accounts for 95.41% of all the cyberattacks for the quarter. Other application types which recorded attacks — albeit considerably smaller — are Java (2.36%), Adobe Flash (1.57%), and PDF (0.66%).
Making up nearly all of the vulnerabilities exploited that are recorded by Kaspersky, you might be curious how these three software types are being used by cybercriminals for their attacks. Let’s dig deeper.
The most vulnerable
Vulnerabilities in the Microsoft Office Suite are the most exploited by cybercriminals, accounting for 72.85% of the exploits for Q3 2019. This is a distinction which the software has unfortunately retained from the preceding quarter.
Stack overflow errors are the most exploited among the vulnerabilities discovered in the Suite. These come from the Equation Editor application, a functionality formerly a part of Microsoft Office.
An attacker can initiate the attack by convincing the user to open a link which directs them to a file that can exploit these errors.
This will allow an attacker to control the affected system. This lets them modify the installed programs in the device, modify data, or even create new users with administrative user rights.
Browser attacks
Kaspersky noted that modern browsers are complex software products which constantly produce new vulnerabilities, making them ideal targets for attacks. In Q3 2019, the exploitation of browser vulnerabilities accounted for 13.47% of the attacks recorded.
Kaspersky said that Microsoft Internet Explorer is the most vulnerable among today’s browsers. For that quarter in particular, the zero-day vulnerability, CVE-2019-1367, which allows an attacker to take full control of the system if the target user is logged in with administrative user rights was actively exploited.
An unscheduled security patch from Microsoft was released in order to remedy the situation, indicating how severe the vulnerability was.
Being a web-based attack, a cybercriminal usually sends a link to the user via email which directs them to a website specifically designed to exploit this vulnerability.
Mobile threats
A fairly huge chunk of attacks come from the exploits of Android application vulnerabilities. In the third quarter of 2019, these accounted for 9.09% of all the recorded exploits.
For that quarter, a notable threat was discovered in CamScanner, a popular Android application used for scanning documents. They detected a dropper component — a hard-to-detect malware which installs other malicious software — in an advertising library.
The dropper, known as Necro.n, executes a malicious code once the app is run. This allows the attacker to show intrusive advertising and even steal money by charging paid subscriptions.
These vulnerabilities arise from some of our most commonly used software. This brings to light the importance of installing the security updates regularly put out and being mindful of the applications that we download and use.
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!