Editor’s note:
- As of 12/20/2021 at 2:15pm PST, this post was updated to indicate that detections for CVE-2021-4104 are present in production
- As of 12/19/2021 at 1:51pm PST, this post was updated to indicate that detections for CVE-2021-45046 are now present in production.
- As of 12/16/2021 at 3:45pm PST, this post was updated to include information about detections for CVE-2021-45046.
From our partners:
NIST has announced a recent vulnerability (CVE-2021-44228, CVE-2021-45046, & CVE-2021-4104) in the Apache Log4j library. To help with detection, Google Cloud IDS customers can now monitor and detect attempted exploits of these CVEs.
Background
The Apache Log4j utility is a commonly used component for logging requests. On December 9, 2021, a vulnerability was reported that could allow a system running Apache Log4j version 2.15 or below to be compromised and allow an attacker to execute arbitrary code.
On December 10, 2021, NIST published a critical Common Vulnerabilities and Exposure alert, CVE-2021-44228. More specifically, Java Naming Directory Interface (JNDI) features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from remote servers when message lookup substitution is enabled.
If you have workloads you believe may be vulnerable, you can use Google Cloud IDS to help monitor and detect for exploit attempts in your Google Cloud environment. You can read further details on the NIST website here, Google Cloud’s security advisory here, and recommendations for investigating and responding to the Apache “Log4j 2” vulnerabilities here.
Addressing Apache Log4j vulnerability with Google Cloud IDS
Google Cloud’s Cloud IDS is a native network-based threat detection product that helps detect exploit attempts and evasive techniques at both the network and application layers, including buffer overflows, remote code execution, protocol fragmentation, and obfuscation. The detection capability is built with Palo Alto Networks threat detection technology. To help our customers monitor the Cloud IDS team has worked with Palo Alto Networks, and the Google Cybersecurity Action Team team, to analyze this issue and update the Cloud IDS detection systems to help detect the most common types of Log4j 2 exploit attempts in their GCP environments for CVE-2021-44228, CVE-2021-45046, & CVE-2021-4104.
For customers currently using Cloud IDS, detections for CVE-2021-44228 were automatically deployed as of December 12, 2021 at 9:00PM UTC and no further action is required to enable it. Detections for CVE-2021-45046, & CVE-2021-4104 were automatically deployed as of December 19, 2021 at 8:19 PM UTC. Any new deployments or new Cloud IDS endpoints will have these detections enabled by default. The alerts from these detections have a severity level of Critical. All Cloud IDS endpoints will alert on these detections with no configuration changes required to your IDS endpoint threat severity profile.
Monitoring for potential threats
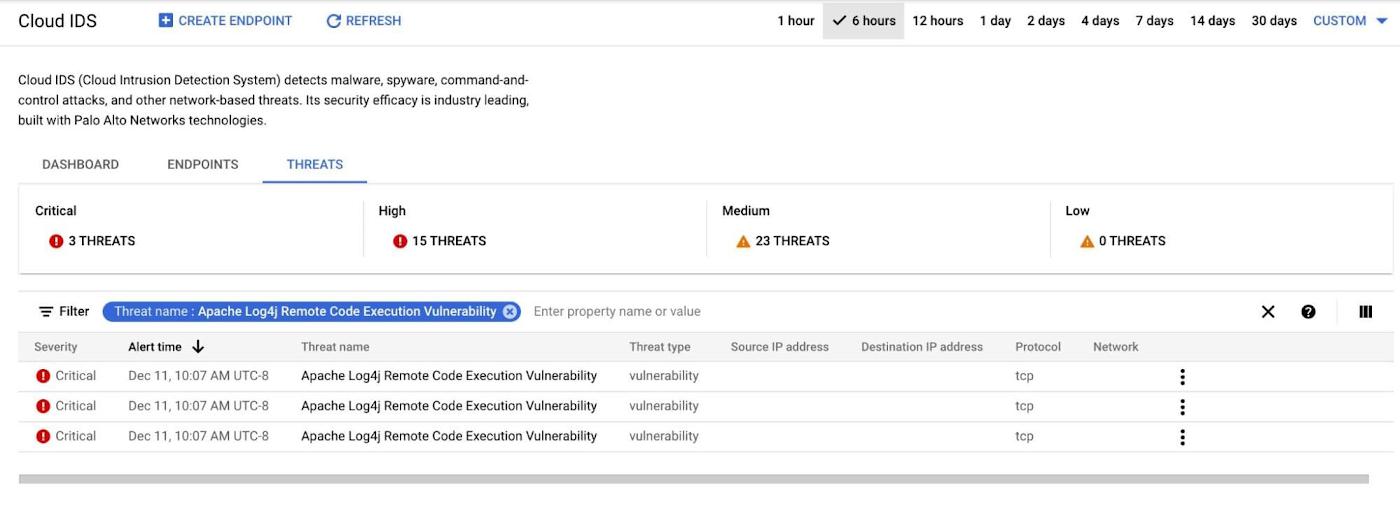
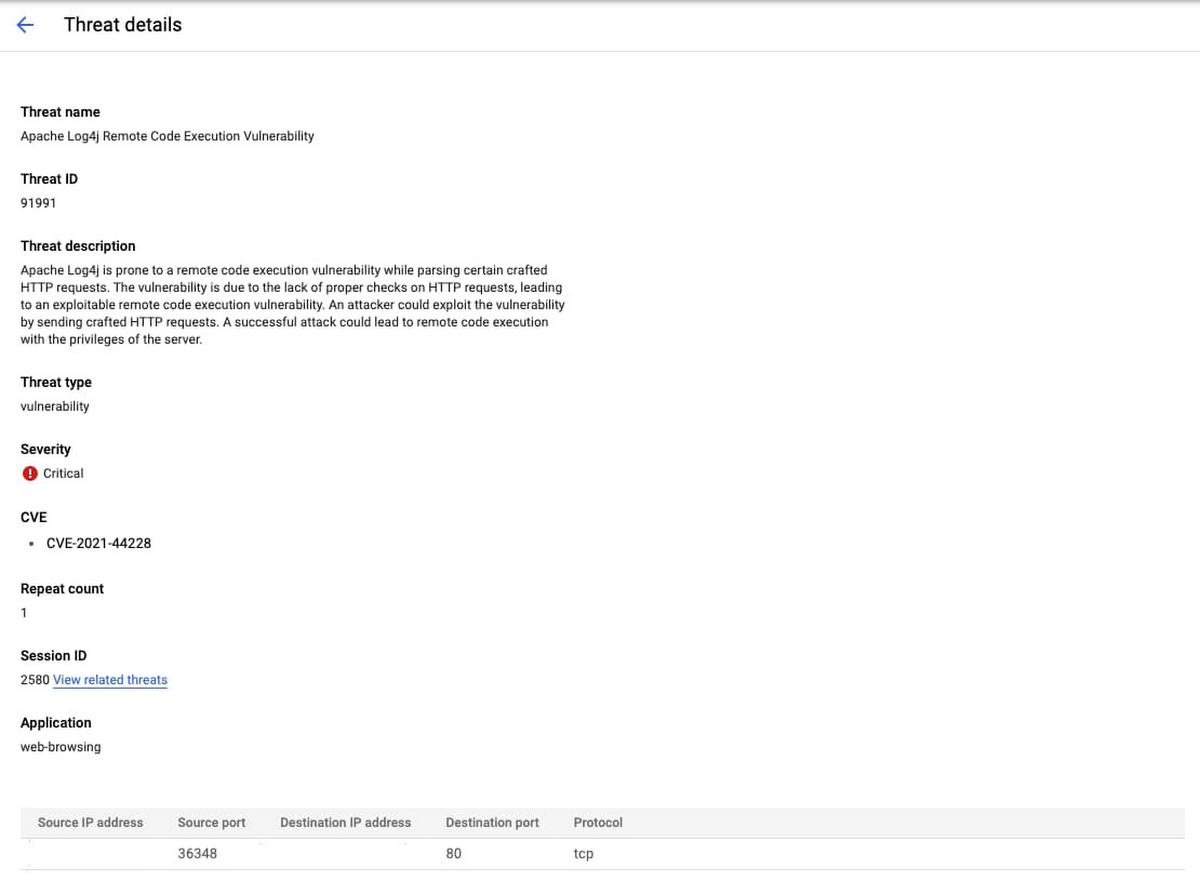
After you set up Cloud IDS to inspect traffic to/from application workloads that may be exploited due to this vulnerability you can quickly search for alerts related to CVE-2021-44228, CVE-2021-45046, & CVE-2021-4104 in the Cloud IDS console by using a filter on “Threat Name:Apache Log4j Remote Code Execution Vulnerability”
In addition to monitoring for Log4j threat alerts in the Cloud IDS console you can also view more detailed logs in Cloud Logging. More details about Cloud IDS logs can be found here.
Addressing potential threats
In addition to updating your systems to the latest version of Apache log4j, customers using Google Cloud Armor can enable new pre-configured WAF rules to help block requests to vulnerable infrastructure.
Complete Cloud IDS product documentation for configuring Cloud IDS and filtering on alerts and logs is available here:
Please contact Google Cloud’s technical support or your Google Cloud account team for assistance if required. Additionally, you can seek support assistance in the Google Cloud Platform Community Slack Channel under gcp-security for non-urgent questions.
By: Megan Yahya (Product Manager Cloud IDS) and Peter Blum (Group Product Manager, Network Security)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!