The before times
Let’s consider the default scenario – before we apply the principle of least privilege. In this scenario, we have a Cloud Build trigger connected to a repository.
From our partners:
When an event happens in your source code repository (like merging changes into the main branch), this trigger is, well, triggered, and it kicks off a build in Cloud Build to build an artifact and subsequently push that artifact to Artifact Registry.
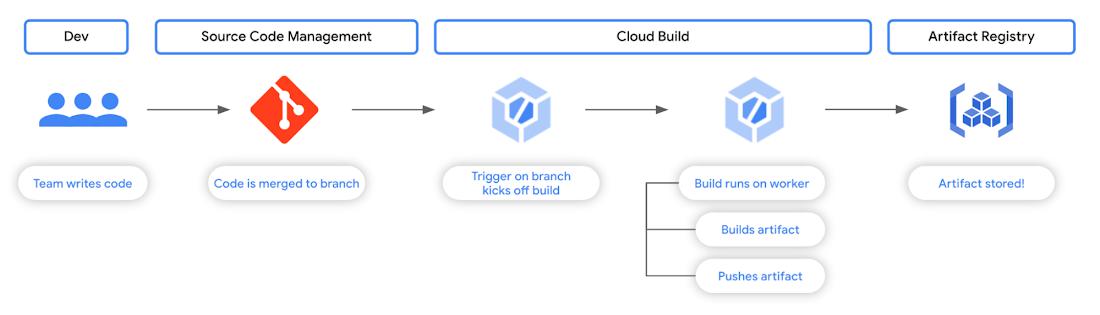
Fig. 1 – A common workflow involving Cloud Build and Artifact Registry
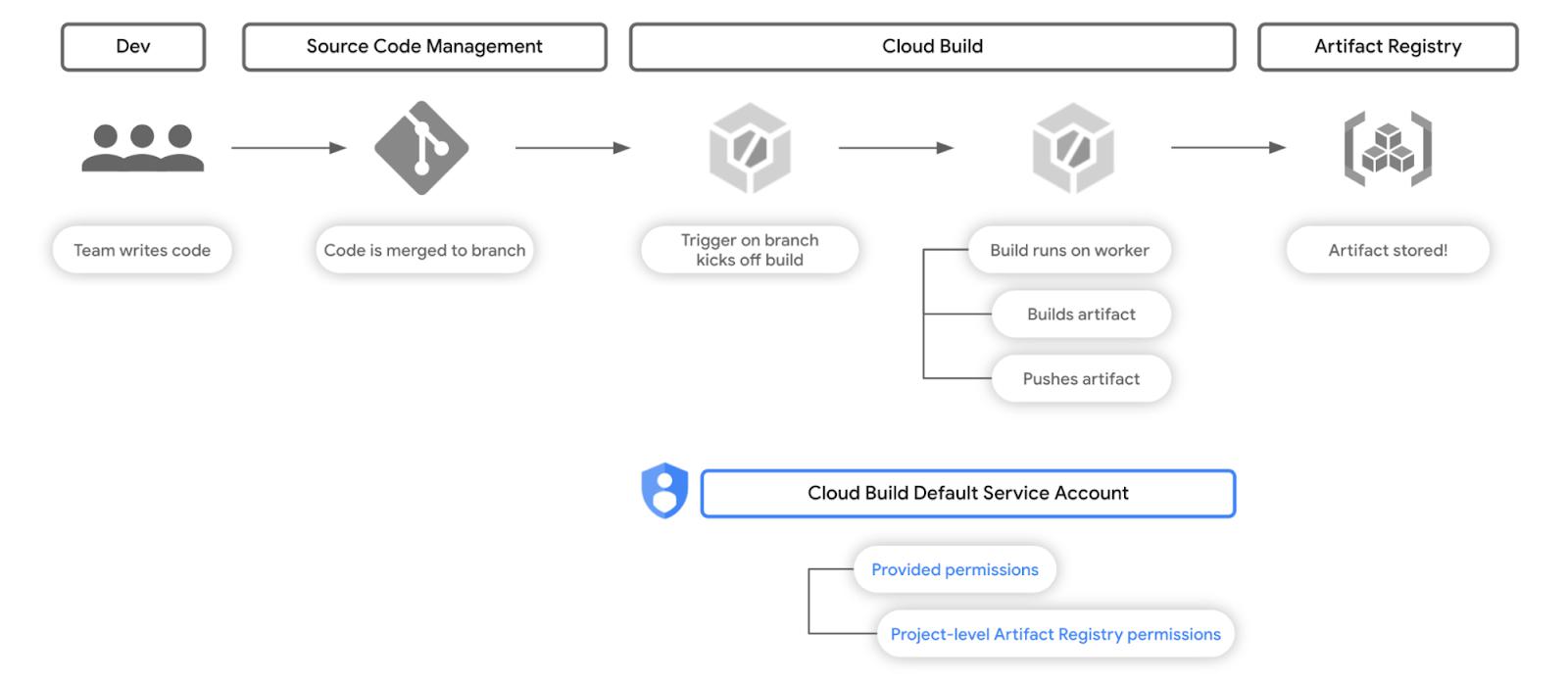
Fig. 2 – The permissions scheme of the workflow in Fig. 1
Putting it into practice
In this scenario, we’re going to walk through how you might set up the below workflow, in which we have a Cloud Build build trigger connected to a GitHub repository. In order to follow along, you’ll need to have a repository set up and connected to Cloud Build – instructions can be found here, and you’ll need to replace variable names with your own values.
This build trigger will kick off a build in response to any changes to the main branch in that repository. The build itself will build a container image and push it to Artifact Registry.
The key implementation detail here is that every build from this trigger will use a bespoke service account that only has permissions to a specific repository in Artifact Registry.
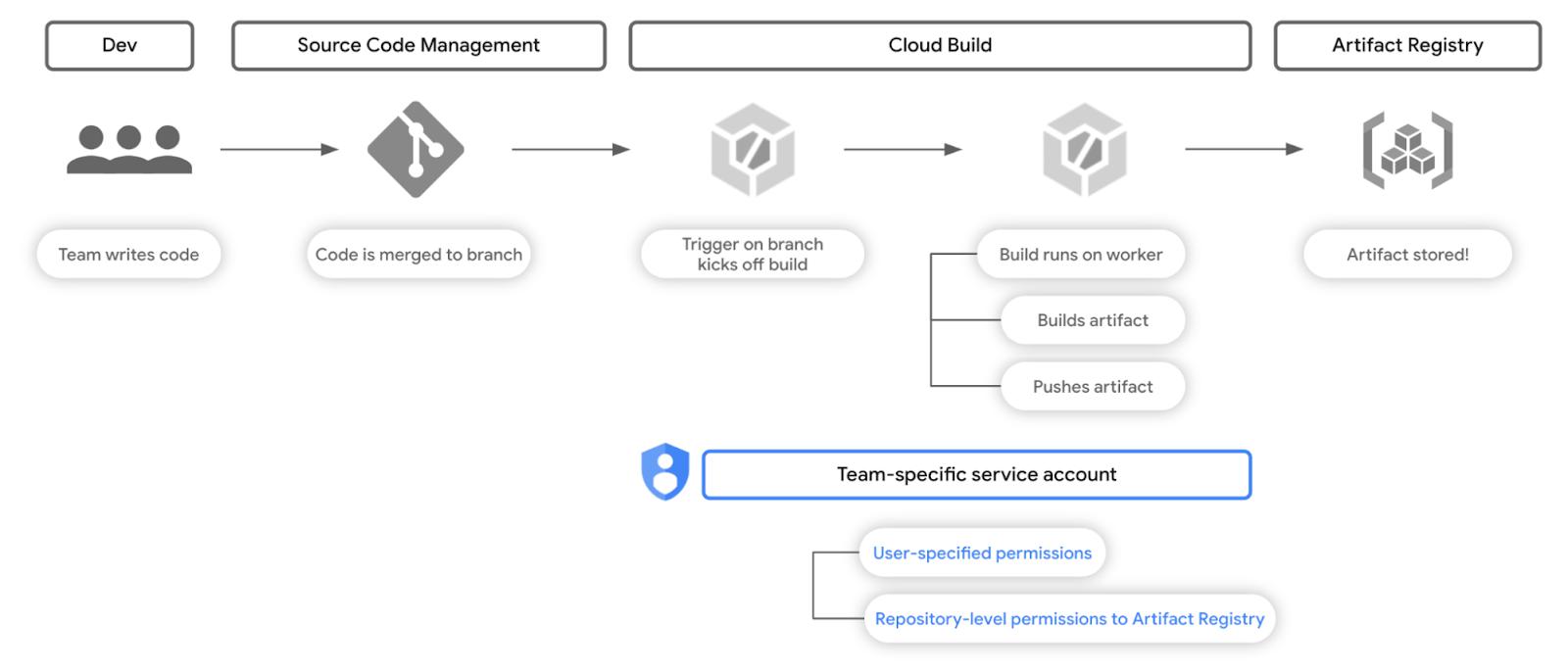
Fig. 3 – The permissions scheme of the workflow with principle of least privilege
gcloud artifacts repositories create ${TEAM_A_REPOSITORY} \
--repository-format=docker \
--location=${REGION}
gcloud iam service-accounts create ${TEAM_A_SA} \
--display-name=$TEAM_A_SA_NAME
gcloud artifacts repositories add-iam-policy-binding ${TEAM_A_REPOSITORY} --location $REGION --member="serviceAccount:${TEAM_A_SA}@${PROJECT_ID}.iam.gserviceaccount.com" --role=roles/artifactregistry.writer
artifactregistry.writer role, but only for a specific Artifact Registry repository.Now, for many moons, Cloud Build has already allowed for users to provide a specific service account for use in their build specification – for manually executed builds. You can see an example of this in the following build spec:steps:
- name: 'bash'
args: ['echo', 'Hello world!']
logsBucket: 'LOGS_BUCKET_LOCATION'
# provide your specific service account below
serviceAccount: 'projects/PROJECT_ID/serviceAccounts/${TEAM_A_SA}
options:
logging: GCS_ONLY
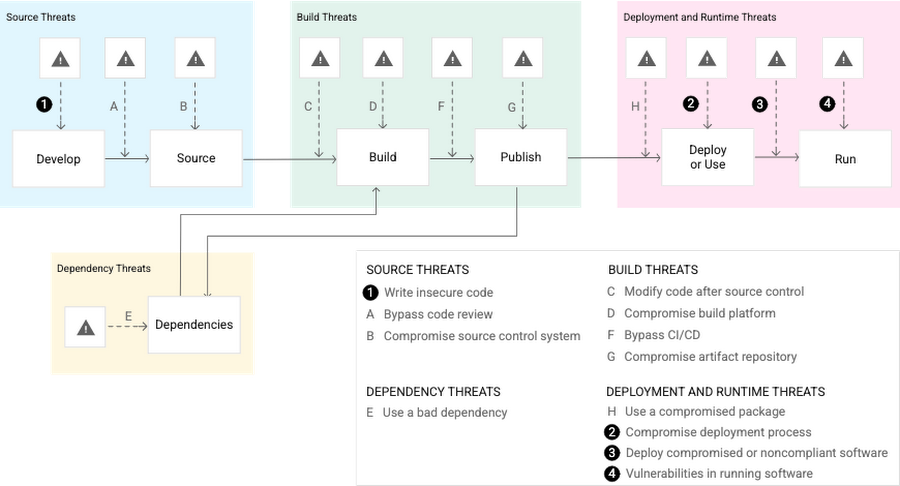
Fig. 4 – Threats in the software supply chain identified in the SLSA framework
–-service-account parameter as follows:gcloud beta builds triggers create github \
--name=team-a-build \
--region=${REGION} \
--repo-name=${TEAM_A_REPO} \
--repo-owner=${TEAM_A_REPO_OWNER} \
--pull-request-pattern=main \
--build-config=cloudbuild.yaml \
--service-account=projects/${PROJECT_ID}/serviceAccounts/${TEAM_A_SA}@${PROJECT_ID}.iam.gserviceaccount.com
TEAM_A_REPO will be the GitHub repository you created and connected to Cloud Build earlier, TEAM_A_REPO_OWNER will be the GitHub username of the repository owner, and TEAM_A_SA will be the service account we created earlier. Aside from that, all you’ll need is a cloudbuild.yaml manifest in that repository, and your trigger will be set!With this trigger set up, you can now test the scope of permissions your builds that run based on this trigger have, verifying that they only have permission to work with the TEAM_A_REPOSITORY in Artifact Registry.
In conclusion
Configuring minimal permissions for build triggers is only one part of the bigger picture, but a great step to take no matter where you are in your journey of securing your software supply chain.
To learn more, we recommend taking a deeper dive into the SLSA security framework and Software Delivery Shield – Google Cloud’s fully managed, end-to-end solution that enhances software supply chain security across the entire software development life cycle from development, supply, and CI/CD to runtimes. Or if you’re just getting started, check out this tutorial on Cloud Build and this tutorial on Artifact Registry!
By: Anthony Bushong (Developer Relations Engineer)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!








