For many of those building in the cloud, speed and security of deployments are amongst their top priorities. At times these goals can seem at odds with each other, especially if security guidance is distributed, written more as reference than opinion, and lacking in tooling for actual implementation in your environment. But they don’t have to be. In fact, these are some challenges the security foundations blueprint was created to address. We recently started diving into the blueprint here on the blog to introduce what it is and who it is for, outline some best practices it recommends for creating and maintaining a security-centric infrastructure, and demonstrate how to get started with the automation repo that turns these best practices into deployable Terraform modules.
From our partners:
In today’s post, we’re highlighting the direct experiences of Google Cloud users as they adapt, adopt, and deploy the security foundations blueprint in their cloud environments. These organizations, of all sizes and across industries, reported valuable impact to their development teams and their business. As we worked with them and listened, top themes emerged across the board in how the security foundations blueprint brings value:
- It helps educate brand new users on Google Cloud security capabilities and best practices.
- It collects foundational security decisions together into a single resource, and provides a Google opinionated reference template.
- It provides an automated deployable example that speeds up their secured deployments and secured operations.
- It enables partners to build subject matter-specific solutions on top of a secured foundation.
Let’s take a look at each of these qualities more closely.
Educating customers on security in Google Cloud
Moving workloads to the Cloud opens a number of opportunities to modernize and improve, and among them is strengthening your infrastructure’s security posture. If you are accustomed to administering security in an on-prem environment, however, transitioning to Google Cloud does require familiarizing yourself with a new set of infrastructure primitives (the building blocks available to you), control abstractions (how you administer security policy), and the shared fate model between you and Google Cloud.
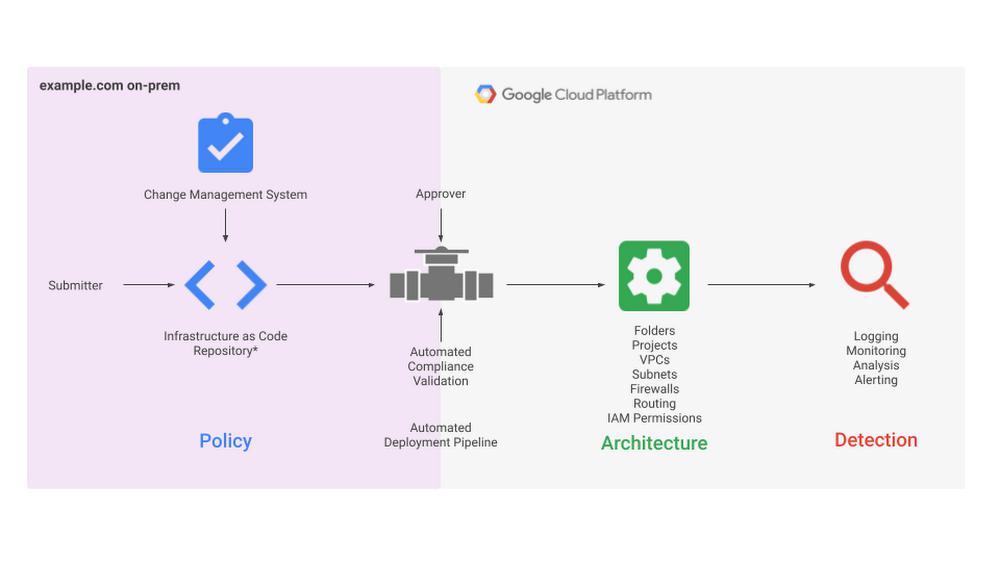
The security foundations blueprint guide brings these topics together into a comprehensive resource to help educate new users on Google Cloud’s security capabilities. It covers your network, your resource hierarchy, how you provide access, and a whole lot more (which you can read about in our recent blog post). It is a reference document for customers to use when designing architecture and establishing policies and guides that support a more secure environment. For those customers that have already established their security strategy, the blueprint can be used to validate and adjust their existing architecture to align with best practices we’ve established for Google Cloud security.
Opinionated guidance from security experts
Once you are familiar with the products and options available for securing your deployment, it’s time to translate that knowledge into a security strategy. However, this can be a challenging process as you try to navigate the large, complex web of interdependent decisions you need to make.
Pause right there, because the security foundations blueprint does this heavy lifting for you. As designed, it provides a tested path through these decisions that ensures they are integrated to hit a strong security posture. In other words, it is written as opinionated best practices for securely deploying workloads on Google Cloud. And it’s written by the platform-maker itself with a deep understanding of the product configuration for today and tomorrow.
By following the best practices provided by the blueprint, you will be laying a foundation that supports a strong security posture. It provides both background considerations and discussions of the tradeoffs and motivations for each of the decisions, so that you can assess the risks and customize it to your own needs. In fact, the blueprint is designed for flexibility so that it can be used in its entirety as it is written, or as a starting point for designing your architecture and security policies. The blueprint is also regularly updated to incorporate practitioner feedback, product updates and additional threat models, so your security strategy can stay up-to-date as well.
Speeding up deployments
Time to market is one of the universal goals in any project implementation, including your cloud deployments. Manual settings and scripting for configuration and policy setting of your deployment’s IAM, firewalls, logging, and backups, can create complexity and reduce repeatability, slowing down development velocity.
By adopting the security foundations blueprint, code is pre-written and tested for you, having been translated from best practices into Terraform modules. Additionally, operational tasks are automated into the deployment process itself, allowing you to increase the speed of your deployments. You can also manage and track changes increasing the ability to govern the state of your infrastructure. Speeding up deployments without compromising on security is the number one benefit we consistently hear as a result of adopting the blueprint and underlying Terraform modules.
At Deloitte, we’ve been able to successfully leverage the Security Foundations Blueprint with our customers to help them accelerate their secure adoption of Google Cloud, which is accretive to the development of our own delivery methodologies and solutions.
Foundation for building context-specific customized cloud guidance
Beyond foundational security, customers and partners may have more specific use cases and requirements they need to meet based on industry, geography, or regulatory constraints unique to their business. Approaching each case as a completely new and fresh build can be challenging to scale. In addition, both customers and partners hold valuable knowledge from their own experience and expertise which they apply in building their solutions.
Having a Google Cloud curated starting point for foundational security enables customers and partners to focus on the key differences and enhancements needed for each specific use case, and to build on top of this foundation. This accelerates the process, as it removes the requirement to reimplement the basic controls and policies. Also, the Google Cloud curated reference enables both customers and partners to more easily understand and align their security approaches to the Google Cloud best practices. The security foundations blueprint provides this consistent and foundational starting point so that all users and consumers can start from the same perspective.
What’s next
Whether you are onboarding to Google Cloud for the first time, designing your architecture and security policies, or validating and evolving your existing architecture decisions and policies, the security foundations blueprint is a useful tool for making your deployments more secure (and speedy!).
If you haven’t already, be sure to read the first three posts in this series which introduce the security foundations blueprint, outline the topics it addresses, and give tips for getting started with the Terraform modules. If you want to head straight to the blueprint itself, remember it is made up of both the step-by-step guide and the Terraform automation repo.
Thanks for joining us on this deep dive into the security foundations blueprint! Go forth, deploy and stay safe out there.
By: Alicia Williams (Developer Advocate)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!