At the end of 2021, we announced the ability for Google Cloud Certificate Authority (CA) Service to issue certificates for workloads reflecting their federated identities, even if the workloads are hosted on-premises or in other clouds. We are excited to announce this capability is now generally available, advancing our work to support customers’ implementation of zero trust strategies across all their IT environments.
At the core of a zero trust approach to security is the idea that trust needs to be established via multiple mechanisms and continuously verified. A zero trust approach to end user access (such as Google’s BeyondCorp model or using our BeyondCorp Enterprise product offering) establishes trust in end-users by considering identities and context. A zero trust approach to protecting workloads on cloud-native infrastructure (such as Google’s BeyondProd model) creates trust between workloads by defining and enforcing access policies based on service identities, rather than the IP addresses of the host infrastructure.
From our partners:
Users can create credentials for service identities using Certificate Authority Service, a highly available and scalable private certificate authority that can be used to issue workload credentials (in the form of certificates) reflecting the workload’s identity. The certificates issued by the service conform to standards (RFC 5280) so you can specify name constraints limiting which domain names the CA can issue certificates to (a capability currently in preview) or you can request custom extensions in the certificate (e.g., for your unique application semantics).
The new federated identity feature means that even if you manage your workload identities in other clouds or in on-premises environments with Active Directory, you can now issue a certificate from CA Service reflecting their federated identity. As a result, by using these certificates, you can avoid manually configuring access policies using IP addresses. Further, using CA Service allows you to issue certificates at scale (with the principle of least privilege) saving significant time and resources while increasing security. Based on early feedback from customers, these savings are proving to be hugely valuable.
Jonathan Perry, Managing Director, Consolidated Trade Ledger, at Goldman Sachs, recently spoke about his experience with this new capability and how Google Cloud continues to democratize security for users, saying:
“At Goldman Sachs, the key principle for our zero trust strategy is homogeneity and CA Service is a super important piece of this strategy. The fact that we can use the same technology to talk to on-premises workloads and get point-to-point connectivity to Google Cloud services with zero trust principles is fantastic. Building CA Service on our own would have been difficult and would not have provided the same integration with all other cloud services, like GKE or Traffic Director, that we benefit from today.”
At-scale certificate issuance for federated workload identities is extremely difficult to build and manage without a capability like CA Service, and shows the value that a managed cloud service provides when moving to a zero trust approach. Jonathan discusses this in more detail during a Google Cloud Security Talks presentation, which is available on-demand if you’d like to learn more about how Goldman Sachs is applying a zero trust approach to its identities and workloads on-premises.
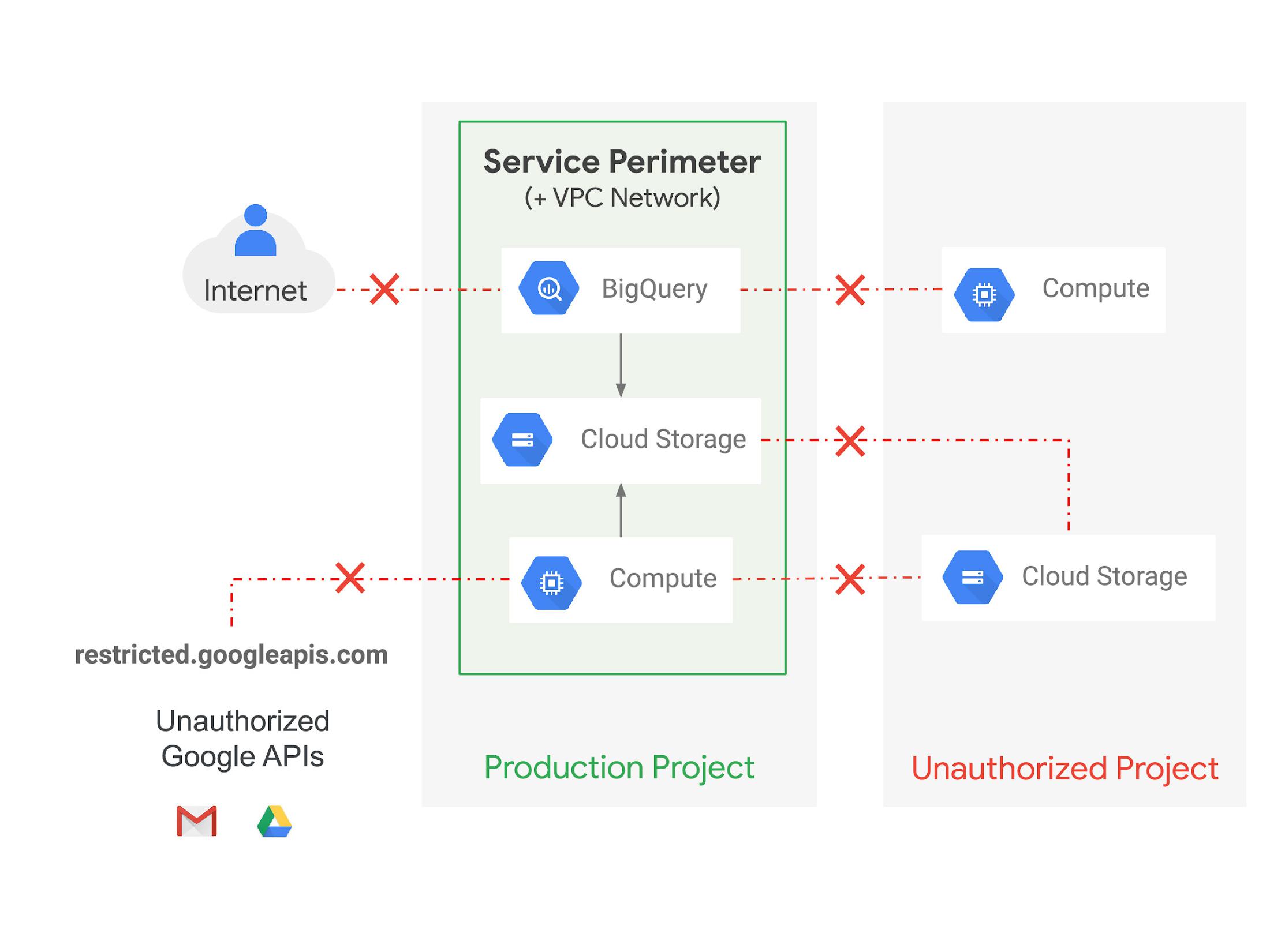
In addition to CA Service, another Google Cloud product that’s useful in implementing the BeyondProd approach is VPC Service Controls (VPC-SC). VPC-SC enables users to define and enforce a security perimeter around multi-tenant Google Cloud services such as BigQuery. With VPC-SC, you can define a service perimeter around a set of Google Cloud services (grouped together using projects) and define zero trust access policies (for instance, based on the identity of the caller) for all the services in a project.
In the example below, there are three services (BigQuery, Cloud Storage, and Compute Engine) within the service perimeter. The perimeter provides an additional layer of protection on top of Google Cloud Identity & Access Management (IAM), which can be used to manage the identity of the workload. Access to resources outside the perimeter will be blocked, even if an attacker is using valid credentials. Moreover, the VPC-SC perimeter blocks any data flow from within the boundary to outside of the boundary, providing strong data exfiltration protection.
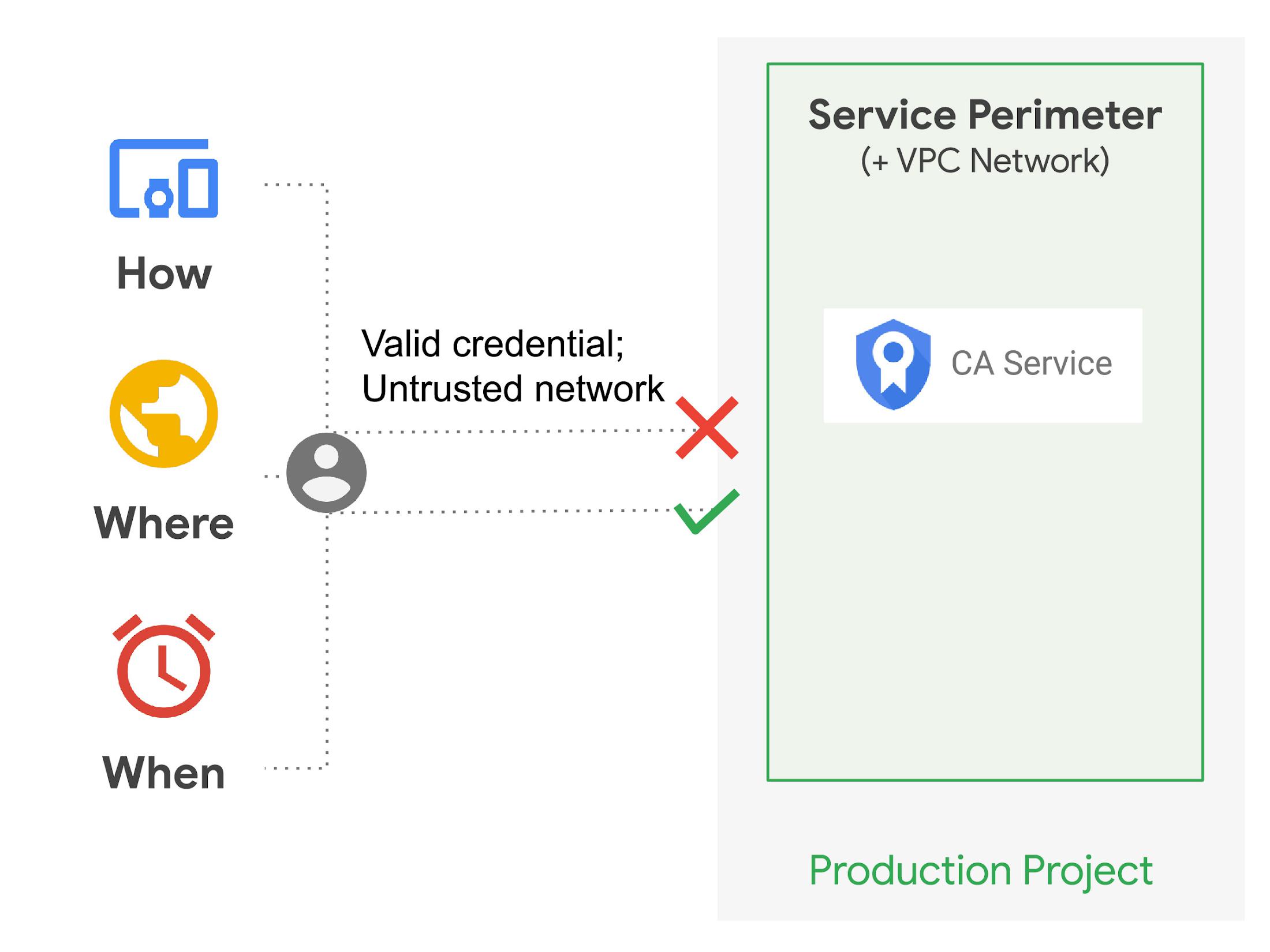
CA Service can also be configured to run inside a VPC-SC service perimeter, further supporting zero trust principles by limiting certificate issuance to a set of service accounts coming from authenticated devices with certain attributes or limiting CA configuration to authorized networks and sets of managed devices.
In a recent presentation called “Bringing BeyondProd to Life with Google Cloud,” Christian Gorke, Head of Cyber Center of Excellence, Big Data and Advanced Analytics, at Commerzbank AG, discussed how CA Service and VPC-SC are foundational capabilities for his organization to build their compliance as code framework, where every resource and access model is programmed and automated. He said:
“As a financial institute in Europe, we are part of a strictly regulated environment. At the same time, we process confidential and personal data, for which we need to reduce the data exfiltration risk. Our goal is to minimize data movements outside of Commerzbank AG and between development, testing, and production environments, but even further, between organizations within Commerzbank AG itself. It is where VPC Service Controls come into play and provides us with a tool to control data flow even in the presence of insider threats – based on zero trust principles. Without a solution, we would need to invest a great deal of time and resources and still run into scalability issues. In addition, with Certificate Authority Service, we finally can minimize our certificate issuance tooling and leverage scalable security backed by HSM across all Google Cloud.”
As customers look to build identity-based zero trust policies, VPC-SC and CA Service are two Google Cloud services that can help make implementing the BeyondProd principles a reality. Getting started with CA Service is easy; the product overview documentation is a great place to begin. If you’re interested in exploring the new feature to federate a third-party identity and obtain certificates, give it a try today and see for yourself how easily you can integrate certificates within your cloud-native applications.
To learn more about Google’s BeyondProd approach, we encourage you to watch the “Applying Zero Trust Principles Beyond Access with BeyondProd” session on-demand. Be sure to also check out all of the other great sessions from the zero trust Security Talks event in December, as well as the threat detection and response sessions from our Security Talks event earlier this month!
By: Anoosh Saboori (Product Manager, Google Cloud Zero Trust)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!