Google owns and operates one of the largest backbone networks in the world to connect its data centers. When your traffic is on the Google network, it no longer transits the public internet, making it less likely to be attacked, intercepted, or manipulated. Data is encrypted in transit and the scale of the network provides robust denial-of-service protection. Along with this inherent network security you have access to services that help protect your applications against network-based threats and attacks even further. Let’s look at them now.
Application security
When you are building a website, web application or API-based service you need to think about protecting them from different attacks such as:
From our partners:
- Bot attacks – “robot” / scripted attacks can be used to take down a site or used for fraud
- Distributed Denial of Service (DDoS) attacks can cause unplanned application downtime
- Credential theft can take on many different forms from phishing for people’s username and passwords, or using leaked credentials to gain access to systems or accounts.
- Application Fraud can take on many forms such as a bad actor using a stolen or fraudulent identity to make purchases (tickets, limited released products) or apply for credit cards or bank loans.
- API Attacks – Can include DDoS attacks against an org’s APIs or a bot or a bad actor attempting to utilize APIs to to obtain sensitive information or to use the API for other malicious activities
Cloud Load Balancing
When you use HTTP(S) Load Balancing you are using a proxy-based Layer 7 load balancer that enables you to run and scale your services behind a single external IP address. The scale at which it operates provides automatic defense against Layer 3 and Layer 4 volumetric and protocol DDoS attacks. It also provides an SSL offload feature that enables you to centrally manage SSL certificates and decryption for highest level of security between your load balancing and backend layers.
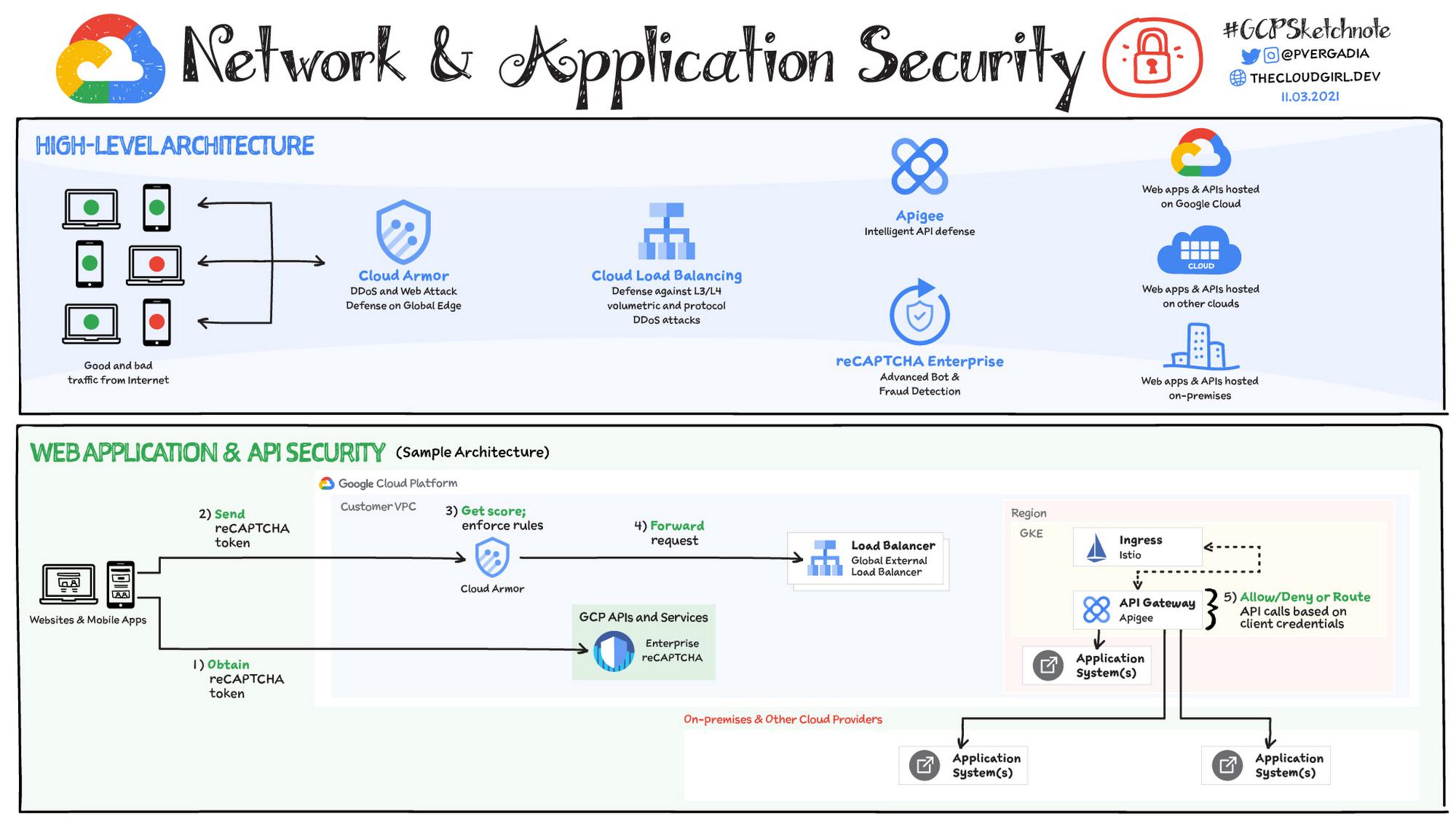
You can protect your internet facing application against all these attacks by using Google Cloud’s Web App and API protection (WAAP) solution. WAAP combines Cloud Armor, Apigee and reCAPTCHA Enterprise to help you mitigate many common threats. Let’s look at each of these in more detail.
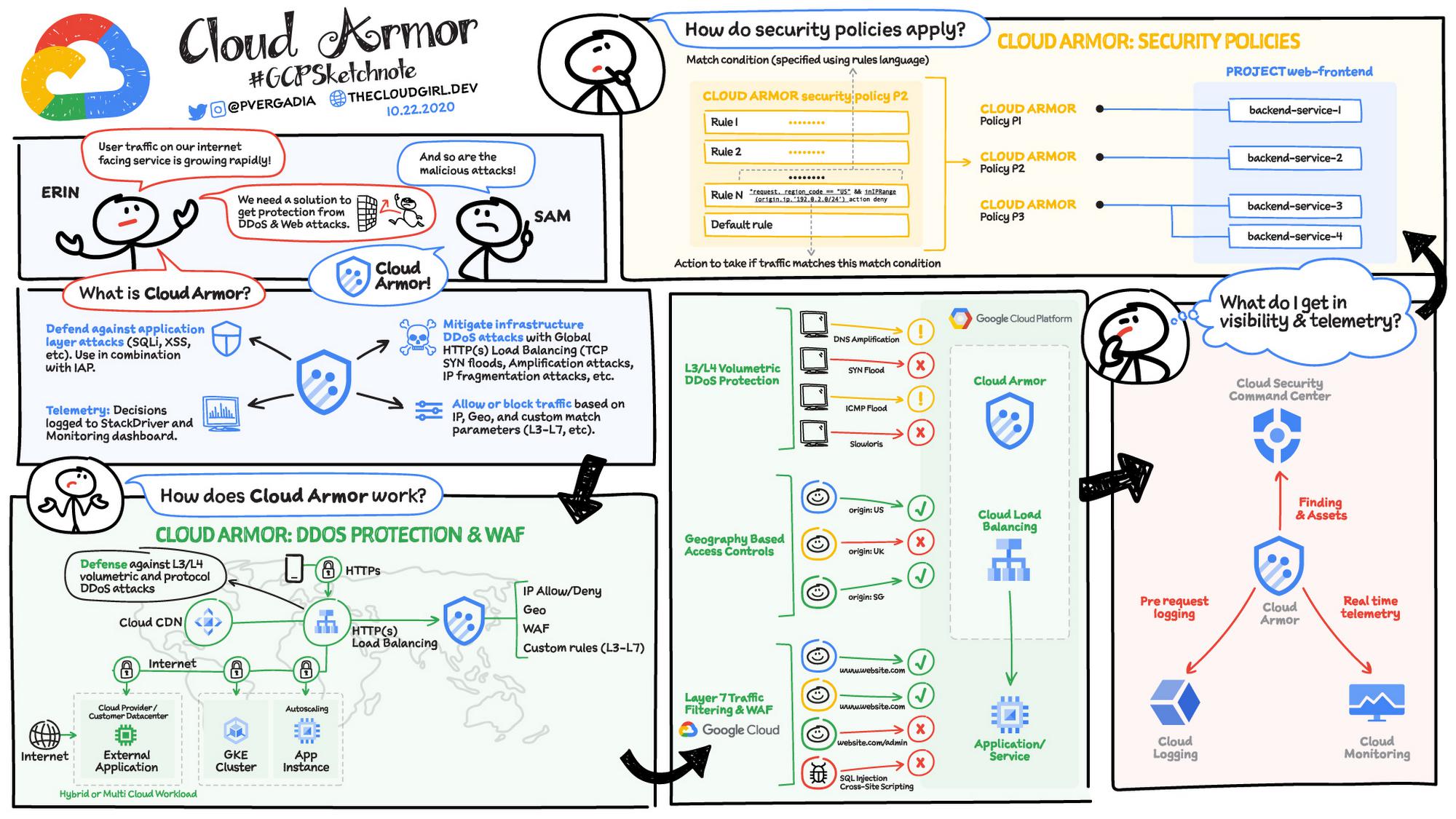
DDoS protection and Web Application Firewall: Cloud Armor
Cloud Armor works in conjunction with Cloud Load balancing and helps mitigate infrastructure DDoS attacks. It can filter incoming web requests by geography or a host of L7 parameters like request headers, cookies, or query strings. Each security policy in Cloud Armor is made up of a set of rules that filter traffic based on conditions such as an incoming request’s IP address, IP range, region code, or request headers.
Cloud Armor is also a full-fledged web application firewall (WAF), and contains preconfigured rules from the ModSecurity Core Rule Set to prevent against the most common web attacks and vulnerability exploit attempts such as SQL injection and Cross-site scripting. All decisions are logged to the Cloud Logging and Monitoring dashboard which gives granular views of allowed, denied, or previewed traffic.
Bot and Fraud protection with reCAPTCHA Enterprise
reCAPTCHA Enterprise is an Enterprise cloud service that provides fraud and bot protection. It leverages Google’s learnings with the reCAPTCHA service that already protects millions of sites on the web. The system brings in many signals from a JavaScript client in a browser or SDK in an app and learns per site what is human vs bot activity. It is headless (can work with any website backend) and does not require users to solve visual puzzles.The system provides a risk score, allowing for progressive action based on risk, such as requirement for a second factor, outright block or redirect, or letting the humans in.
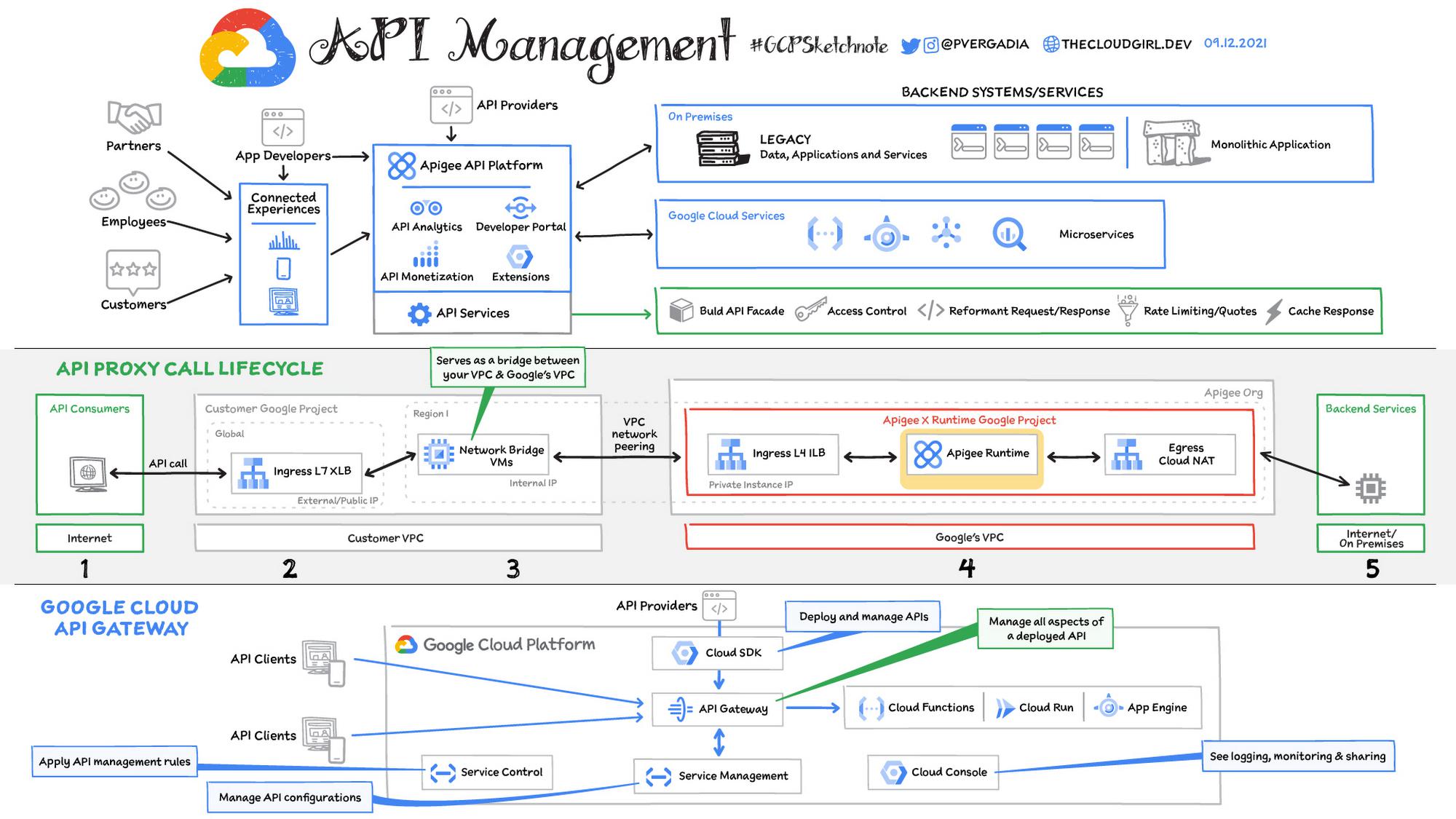
API security with Apigee
The Apigee API management platform provides a single point of management for APIs through the entire lifecycle from both a development and operations perspective. The platform inspects API requests to protect, scale, adapt, control, and monitor API traffic. Apigee’s out-of-the-box policies enable you to augment APIs with features to control traffic, enhance performance, and enforce security without writing any code or modifying any backend services.
Building security for an API takes time and significant expertise, but Apigee security policies let developers control access to APIs with OAuth, API key validation, and other threat protection capabilities. Apigee provides a positive security model understanding the structure of API requests so it can more accurately determine valid and invalid requests.
API traffic can be throttled by quotas to prevent misuse and to defend against DDoS attacks. For example it can rate limit something like account signups or checkouts differently than search queries across a product catalog.
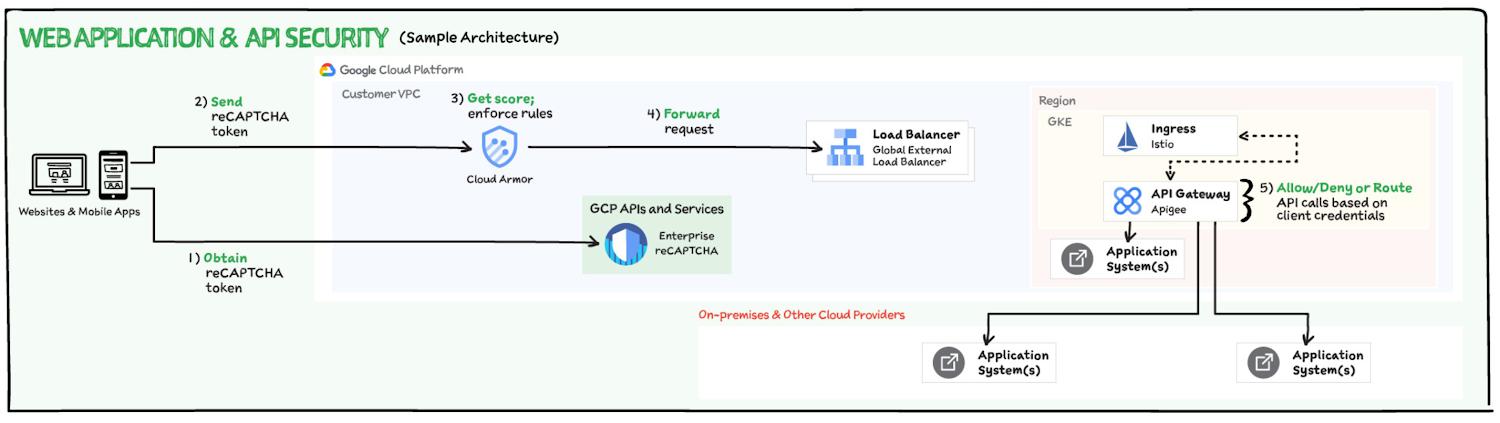
Sample Web application & API security Architecture
Here’s a sample web application & API security architecture that could include these components:
- When a user tries to log into the website or mobile app reCAPTCHA token is obtained.
- reCAPTCHA enterprise deciphers the token in the incoming request and enforce allow/deny decisions in Cloud Armor
- If Cloud Armor allows the request then it is forwarded to Load Balancer
- Load balancer then sends the request to the respective backend with Apigee API Gateway in the middle which allows/denies or route API calls based on client credentials and quotas.
That was a quick overview of the network and application security toolkit in Google Cloud. For a more in-depth look into the WAAP solution check out the solutions page.
For more #GCPSketchnote, follow the GitHub repo. For similar cloud content follow me on Twitter @pvergadia and keep an eye out on thecloudgirl.dev
By: Priyanka Vergadia (Lead Developer Advocate, Google)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!