Moving to the cloud comes with the fundamental question of how to effectively manage security and risk posture. From a Security Operations (SecOps) perspective, there are few core requirements that you may need for effective security and risk management in the cloud. Here are four big ones that are essential for SecOps:
- Need a single, security-centric view of all the cloud resources and policies in your environment
- Understand if resources and policies are configured as expected
- Detect threats reliably so your workloads are safe
- Demonstrate on an ongoing basis that you’re maintaining compliance, transparency & accountability
Security Command Center is focused on addressing these pillars.
From our partners:
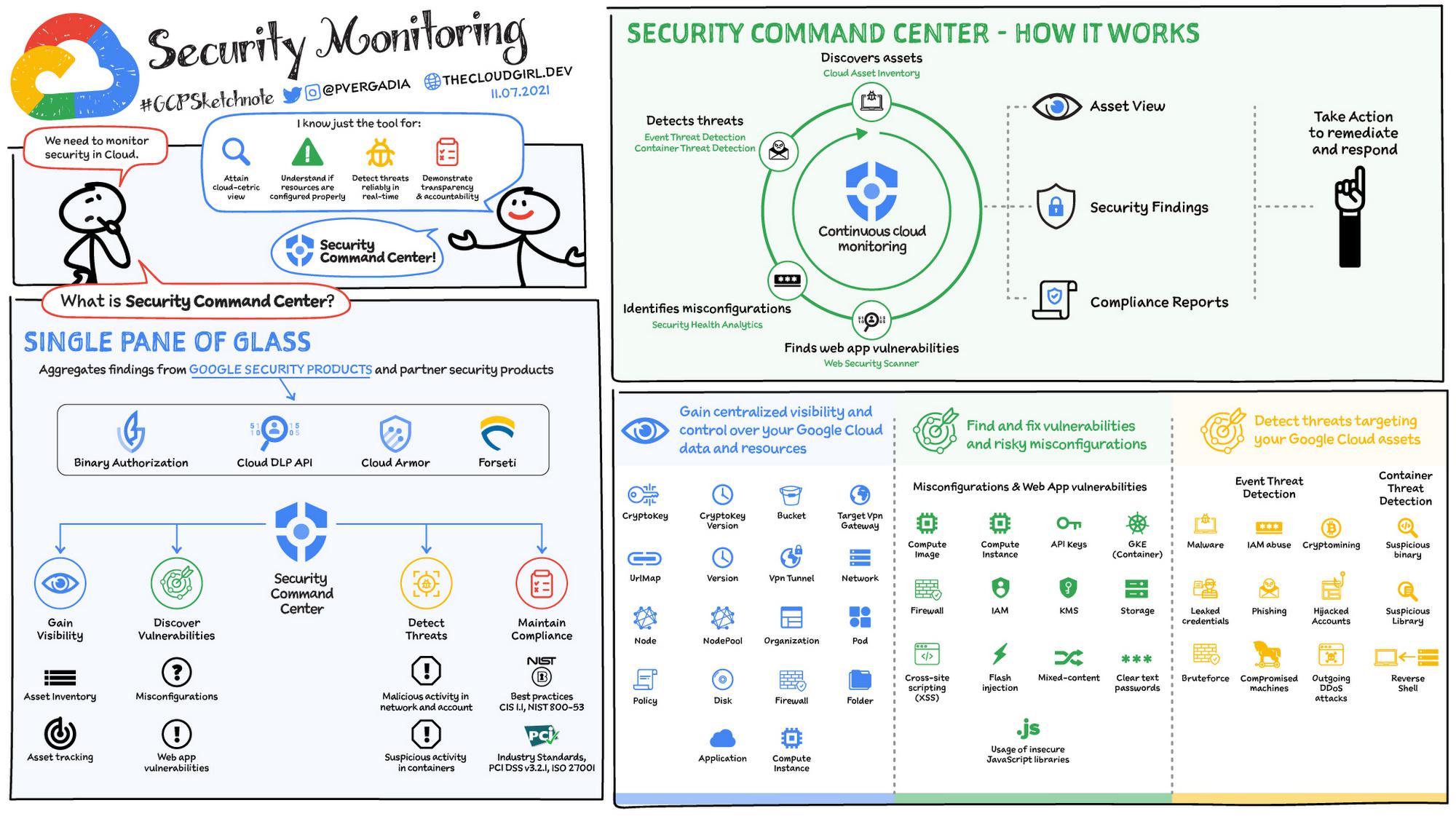
What is Security Command Center?
Security Command Center is a native security and risk management platform for Google Cloud. Security Command Center continuously monitors your Google Cloud environment, allowing you to:
- Gain visibility – Get real time monitoring for all Google Cloud resources
- Discover Vulnerabilities – Detects misconfigurations on your resources + vulnerabilities associated with your web apps (e.g.the OWASP Top 10)
- Detect Threats – It helps detect external threats that are targeted at your environment, such as malicious activity targeting your Google Cloud resources and unauthorized behavior across your organization
- Help maintain compliance – Helps address industry benchmarks & standards with ongoing reports that tie key technical controls to the vulnerabilities & misconfigurations
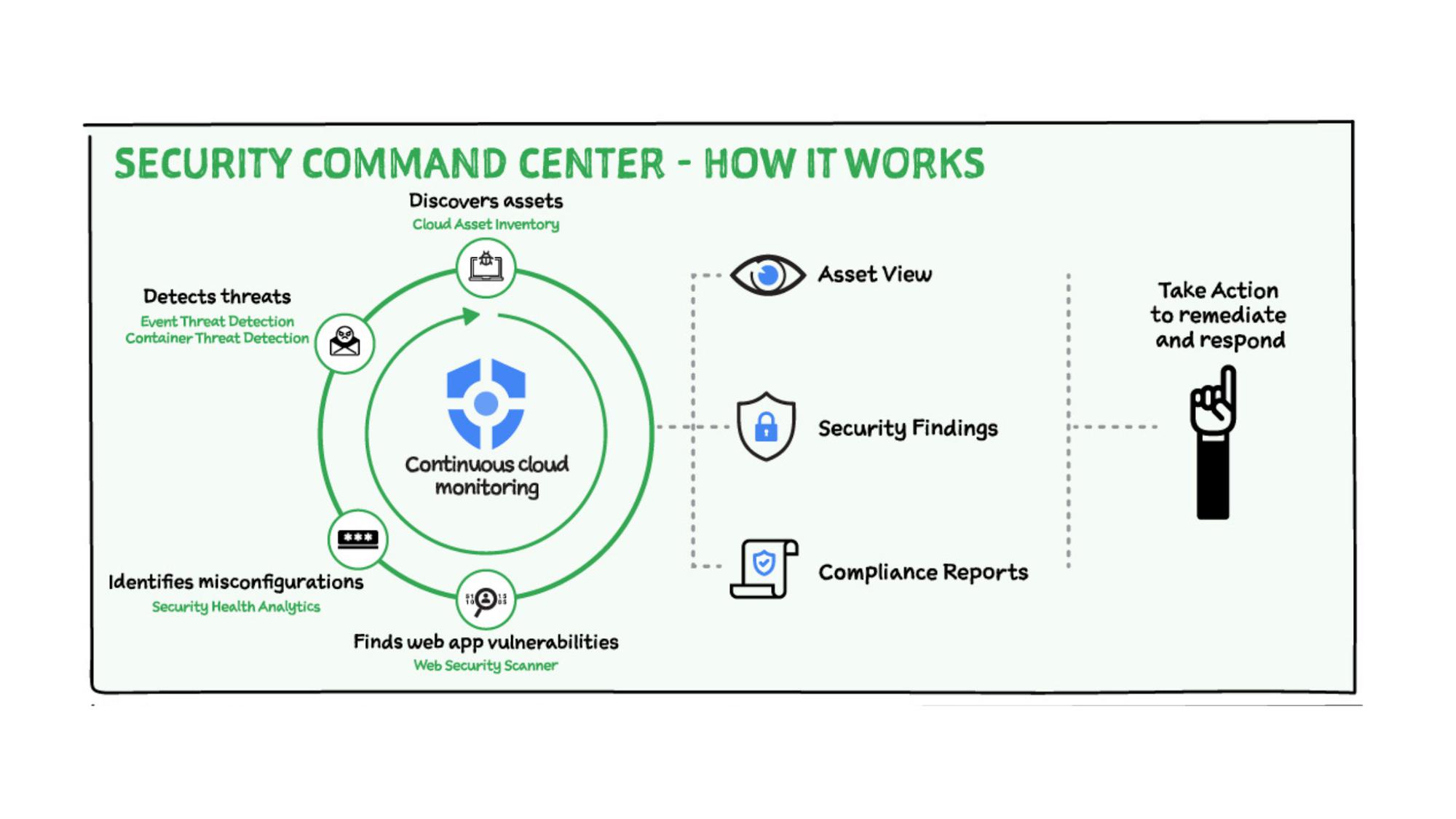
How does Security Command Center work?
There are different built-in services in Security Command Center that roll-up to a single pane of glass to get oversight of your security in Google Cloud.
- Security Command Center can help you discover assets in your Google Cloud environment using Cloud Asset Inventory. Cloud Asset Inventory is tightly integrated with Security Command Center enabling you to discover, monitor, and analyze your assets in one place.
- Security Command Center can identify misconfigurations in your Google Cloud environment using a built-in service called Security Health Analytics. Security Command Center also ties those findings to the industry standard and compliance benchmarks.
- Security Command Center finds web app vulnerabilities using Web Security Scanner, which automatically detects web applications running in Google Cloud and starts scanning them for vulnerabilities.
- Security Command Center can detect threats using Event Threat Detection that analyzes platform logs for identifying malicious activity and Container Threat Detection to help surface top suspicious activity in Container deployments.
Security Command Center’s continuous monitoring and analysis automatically can provide you with the following abilities to effectively manage security and risk:
- An asset view that provides a real-time view of your resources and policies, changes to your inventory and the security findings associated with each of those assets.
- A consolidated set of security findings that span across misconfigurations, vulnerabilities, and threats to your Google Cloud environment. Security Command Center gives you a prioritized security findings view that helps you to address potential security issues.
- A view from compliance lens as to where you stand by correlating all its tracked misconfigurations and vulnerabilities to industry standards like CIS, PCI DSS, NIST 800-53 and ISO 27001. Security Command Center provides compliance reporting segmented by these standards that you can use to track how your environment compares with the technical controls of these industry recommended benchmarks.
Security Command Center also gives you recommendations and remediation steps for you to take action. You can also send these findings to your security ecosystem such as SOAR or SIEM platform.
That was a bird’s eye view of the Security Command Center and the Premium version includes all these capabilities. For a more in-depth look check out the documentation .
For more #GCPSketchnote, follow the GitHub repo. For similar cloud content follow me on Twitter @pvergadia and keep an eye out on thecloudgirl.dev .
By: Priyanka Vergadia (Lead Developer Advocate, Google)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!