A comprehensive API security strategy requires protection from fraud and abuse. To better protect our publicly-facing APIs from malicious software that engages in abusive activities, we can deploy CAPTCHAs to disrupt abuse patterns. Developers can prevent attacks, reduce their API security surface area, and minimize disruption to users by implementing Google Cloud’s reCAPTCHA Enterprise and Apigee X solutions.As Google Cloud’s API management platform, Apigee X can help protect APIs using a reverse-proxy approach to HTTP requests and responses. One important feature of Apigee X is the ability to include a reCAPTCHA Enterprise challenge in the authentication (AuthN) stage of the request.This post shows how to provision a reCAPTCHA proxy flow to protect your APIs. Complete code samples are available in this Github repo.
When and why to use Apigee X for implementing CAPTCHAs
The initial way to use reCAPTCHA Enterprise as part of a Web Application and API Protection (WAAP) solution is through Cloud Armor. For developers who want a purely API-based solution, Apigee X allows developers to define the reCAPTCHA process as a set of Apigee X proxy flows. As a dedicated solution, it moves as much API security code as possible into Apigee.
From our partners:
This method can also make code maintenance easier and can allow API business rules to be managed in code. The reCAPTCHA process can be included directly in Apigee proxies, either individually or as shared flows. This code can then be added to the same source control as all the Apigee proxy code, in line with the API business rules.
Let’s first review a few implementations of reCAPTCHA Enterprise, and then contrast those with an Apigee X implementation example to see which might be best for you.
An introduction to reCAPTCHA Enterprise
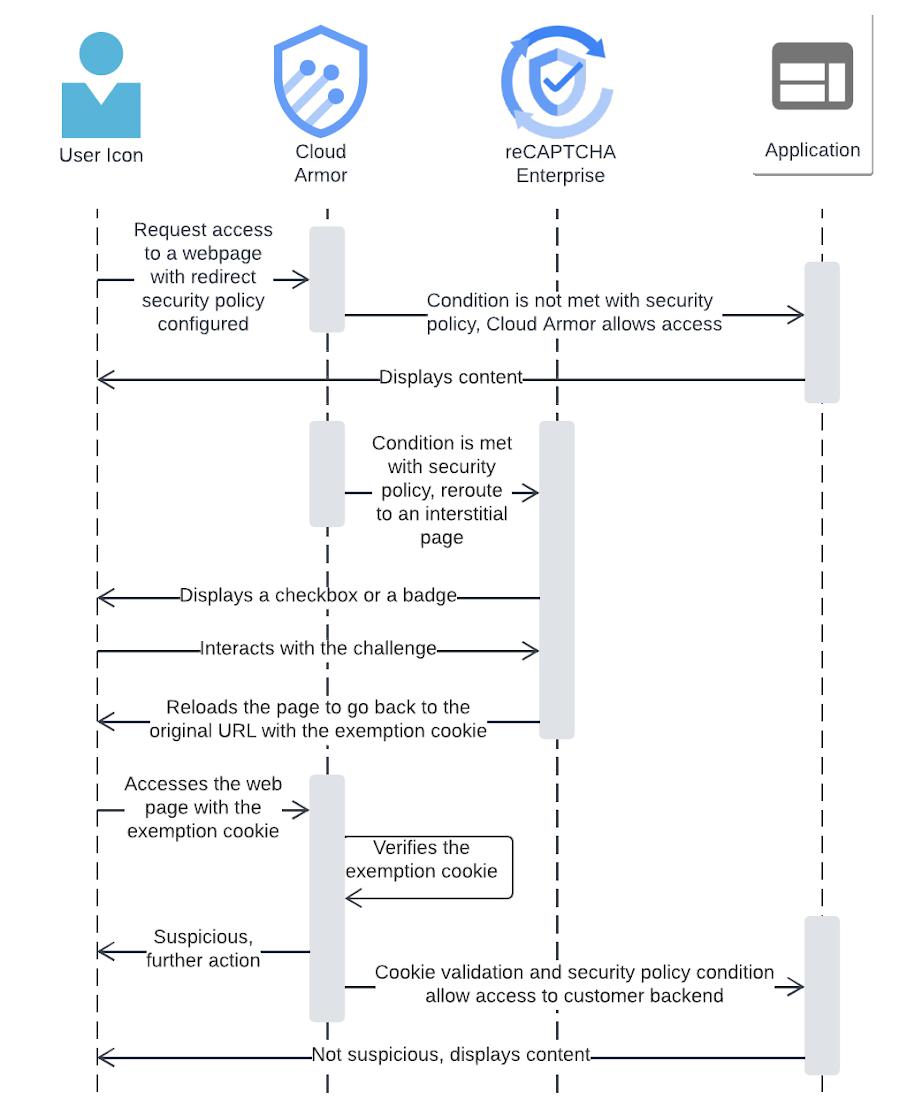
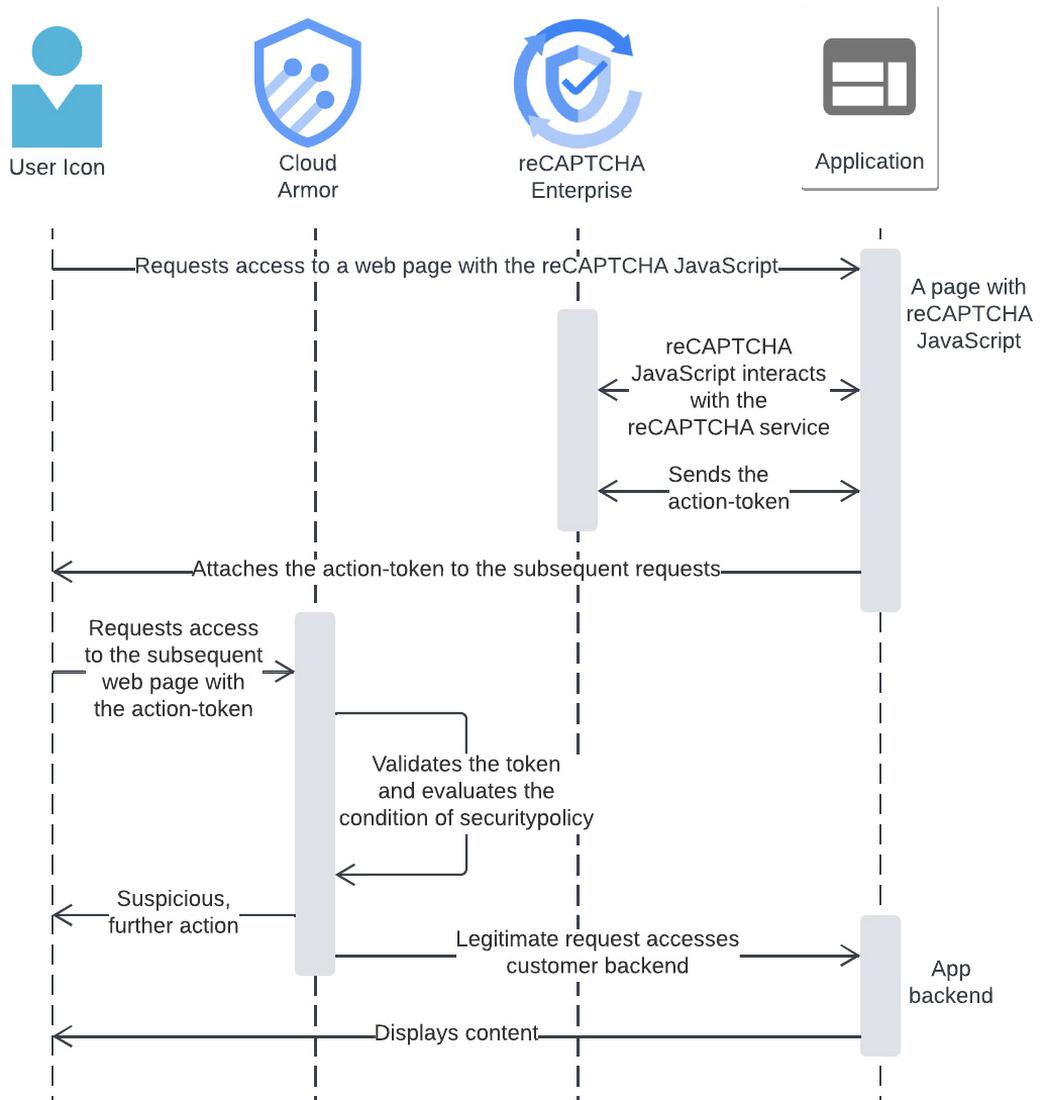
A reCAPTCHA challenge page can redirect incoming HTTP requests to reCAPTCHA Enterprise, which can help stop possible malicious attacks. When reCAPTCHA Enterprise is integrated with Cloud Armor, and the Challenge Page option is selected, a reCAPTCHA will trigger when the policy rule of Cloud Armor matches the incoming URL/traffic pattern.
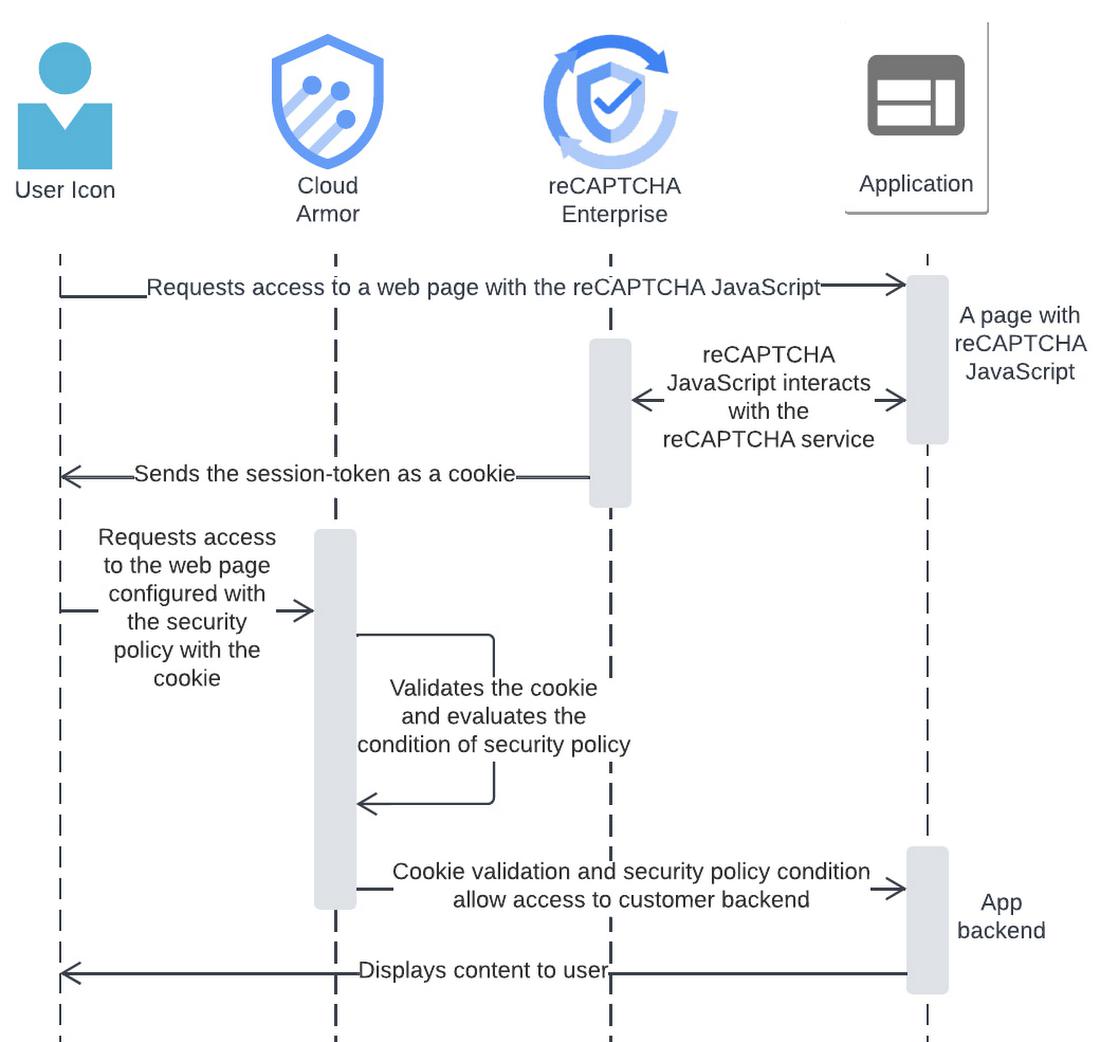
To avoid CAPTCHA fatigue (mouse-click fatigue due to too many CAPTCHA challenges), developers should consider using reCAPTCHA session-tokens, which we explain in more detail below. A challenge page is most useful for dealing with a bot making repeated programmatic HTTP requests. The challenge page redirect and possible reCAPTCHA challenge can stop malicious bots. However, the challenge page can also interrupt a legitimate user’s activity — a reCAPTCHA challenge page is less desirable for a well-intended human user.
Using Apigee X and reCAPTCHA Enterprise
All of the above can also be accomplished in Apigee X, without the need for Cloud Armor. Code for an Apigee X flow that initiates a reCAPTCHA Enterprise challenge is below, and is also available in our Github repo file SC-AccessReCaptchaEnterprise.xml.
<ServiceCallout name="SC-AccessReCaptchaEnterprise">
<Request>
<Set>
<Payload contentType="application/json">{
"event": {
"token": "{flow.recaptcha.token}",
"siteKey": "{flow.recaptcha.sitekey}"
}
}</Payload>
<Verb>POST</Verb>
</Set>
</Request>
<Response>recaptchaAssessmentResponse</Response>
<HTTPTargetConnection>
<Authentication>
<GoogleAccessToken>
<Scopes>
<Scope>https://www.googleapis.com/auth/cloud-platform</Scope>
</Scopes>
</GoogleAccessToken>
</Authentication>
<URL>https://recaptchaenterprise.googleapis.com/v1/projects/{flow.recaptcha.gcp-projectid}/assessments</URL>
</HTTPTargetConnection>
</ServiceCallout>
<Request>
<Set>
<Payload contentType="application/json">{
"event": {
"token": "{flow.recaptcha.token}",
"siteKey": "{flow.recaptcha.sitekey}"
}
}</Payload>
<Verb>POST</Verb>
</Set>
</Request>
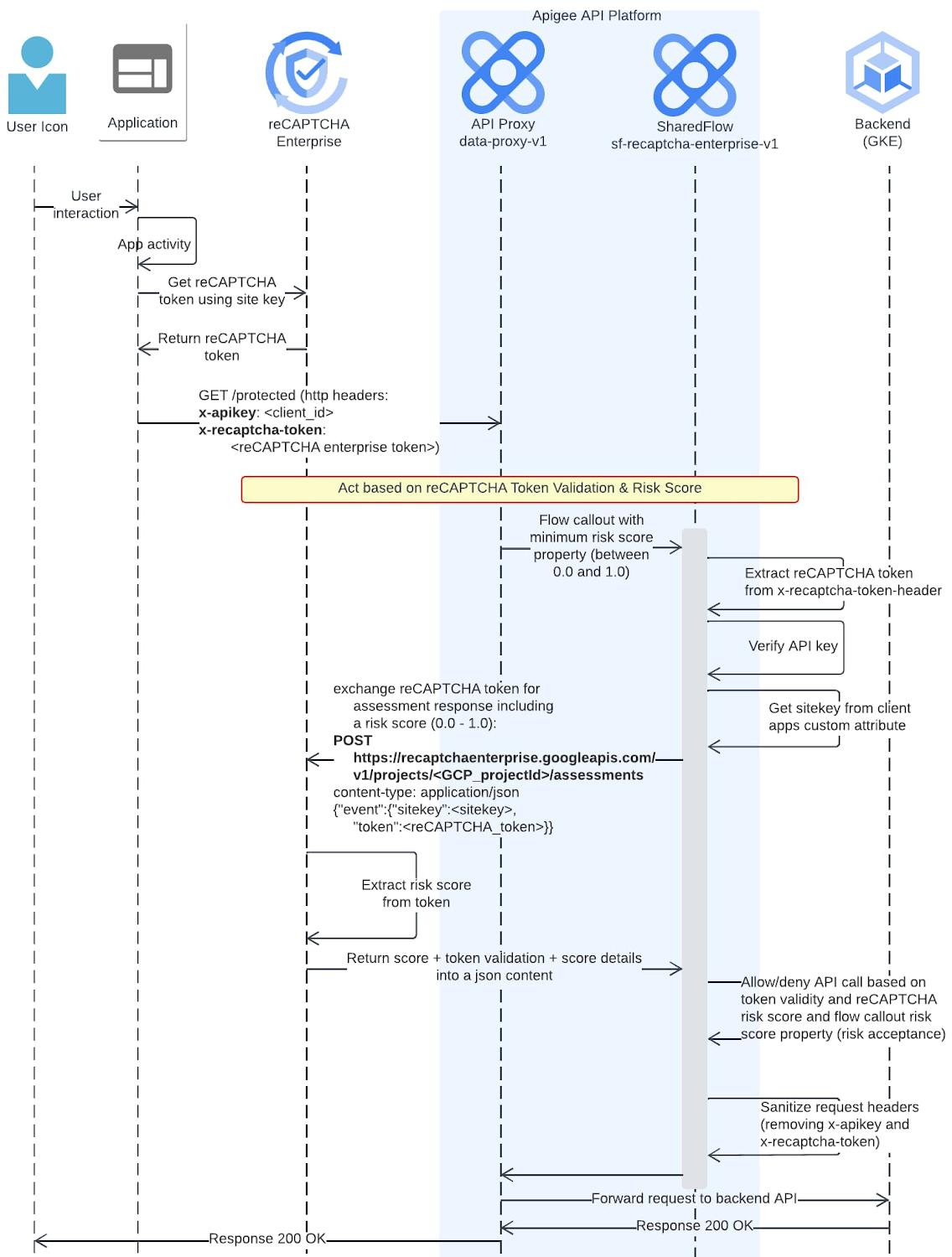
- recaptcha-data-proxy-v1: a data proxy, which calls the reCAPTCHA Enterprise shared flow. The target endpoint of this proxy is httpbin.org
- recaptcha-deliver-token-v1: an API proxy used to deliver an HTML page that includes a valid reCAPTCHA token (cf. Option 2 above). This proxy is not intended to be used in production but only during test phases.
- The reCAPTCHA Enterprise API product
- A developer (Jane Doe)
- app-recaptcha-enterprise: a single developer app when Option 1 has been selected
- 2 developer apps with real app credentials and reCAPTCHA Enterprise sitekeys when Option 2 has been selected:
- app-recaptcha-enterprise-always0
- App-recaptcha-enterprise-always1
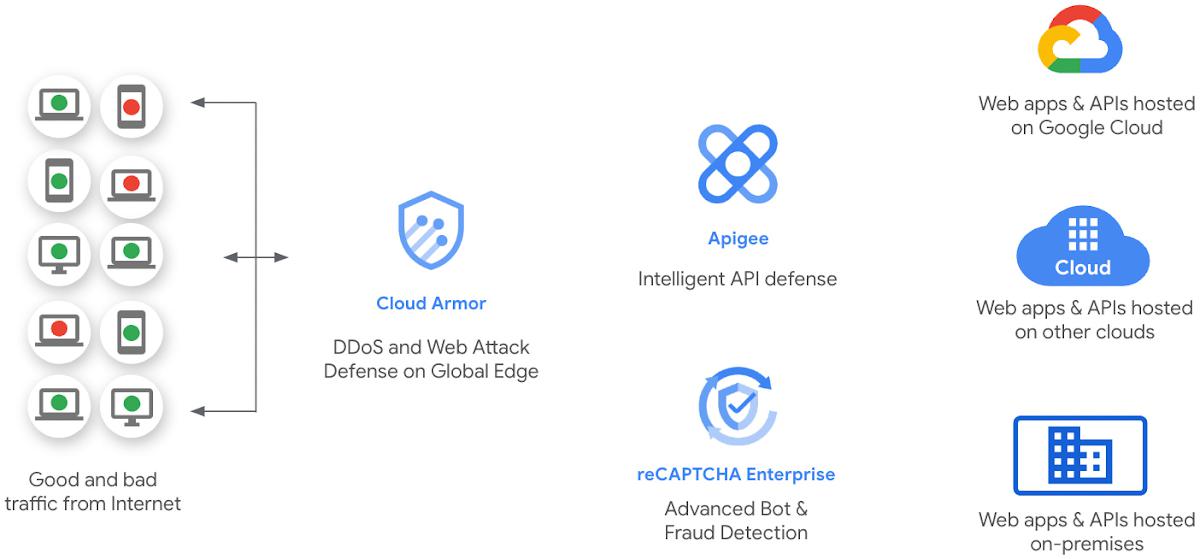
Google Cloud’s Web App and API Protection (WAAP) solution
This implementation is a part of Google Cloud’s WAAP solution. Google’s WAAP security solution stack is a comprehensive solution which is an integration of web application firewall (WAF), DDoS prevention, bot mitigation, content delivery network, Zero Trust, and API protection. The Google Cloud WAAP solution consists of Cloud Armor (for DDoS and web app defense), reCAPTACHA Enterprise (for bot defense) and Apigee (for API defense). This solution is a set of tools and controls designed to protect web applications, APIs, and associated assets. Learn more about the WAAP solution here.
- Build on tested and proven components and code
Detect risky functionality
- New code should be reviewed
- Bypassing safe patterns should also be justified
- High-risk activities should be scrutinized
Automate
- If you do it more than once, automate
What’s next
Give it a try and test out the reCAPTCHA Enterprise Apigee proxy flow code for yourself. An existing reCAPTCHA token and sitekey are required so please acquire those first. When you are ready, you can explore all of Apigee X’s security features in the following documentation: Securing a proxy and Overview of Advanced API Security.
By: Waheed Brown (Strategic Cloud Engineer) and Nandan Sridhar (Product Manager)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!








