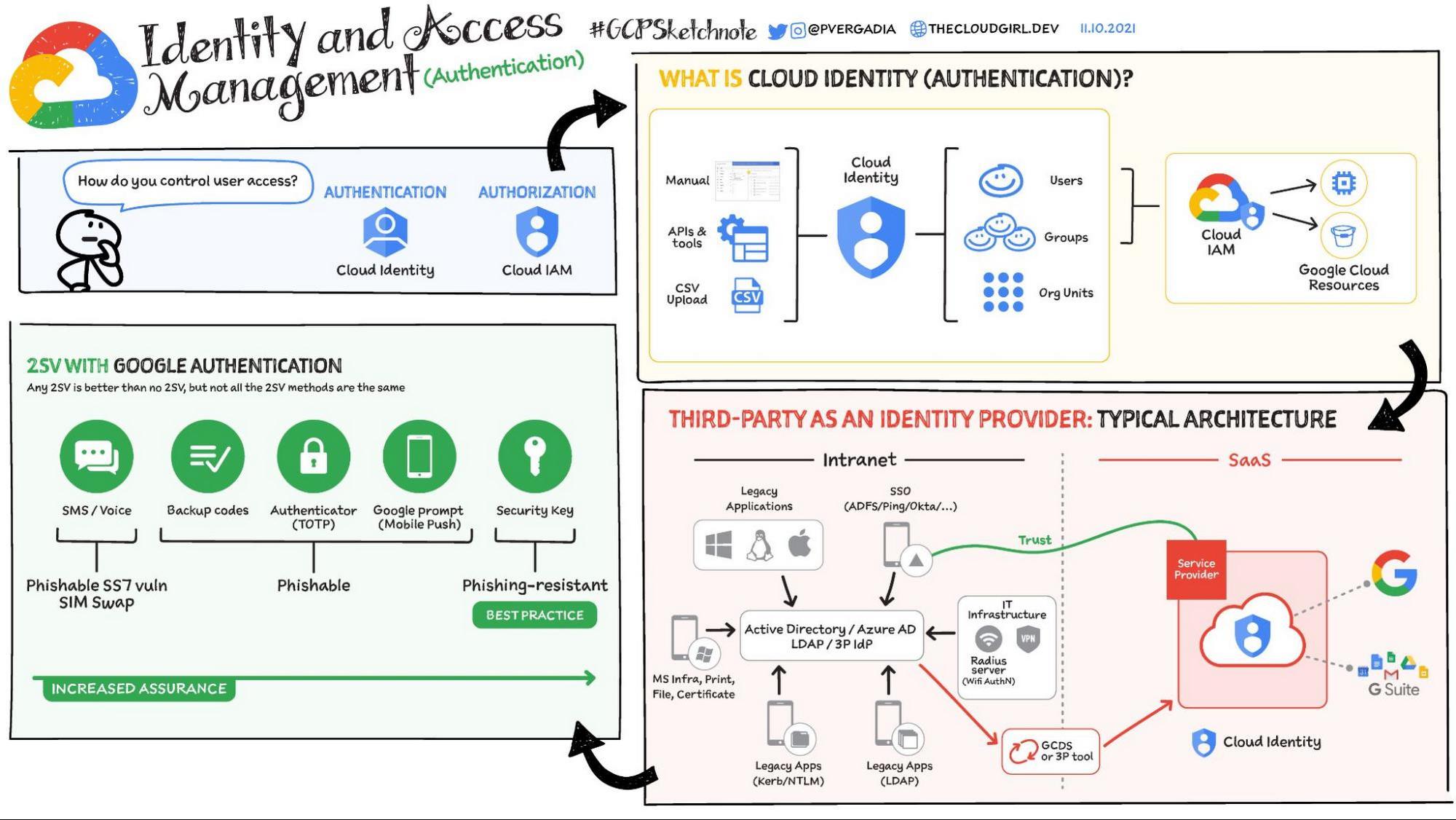
5 Ways A SOAR Solution Improves SOC Analyst Onboarding
Editor’s note: This blog was originally published by Siemplify on Feb. 19, 2021. The number of unfilled cybersecurity jobs stretches into the millions, and a critical part of the problem…
Share