NTT Communications Corporation (NTT Com), the ICT solutions and international communications business within the NTT Group, announced today the results of its investigation regarding the possible information leak due to unauthorized access that the company announced in Japanese on May 28. NTT Com sincerely apologizes to all concerned for any inconvenience or concern caused by the possible information leak.
NTT Com announced on May 28 that some information—although no information on consumer customers—was possibly leaked externally on May 11 due to unauthorized access to NTT Com facilities by attackers on May 7. The internal investigation has determined that information may have been leaked from the construction information management server in Japan that the company uses to manage its Biz Hosting Enterprise (BHE)1 and Enterprise Cloud (ECL) Option Services2 as well as from the server group (“internal servers”) used for internal operations of NTT Com.
From our partners:
1. Unauthorized access to construction information management server of BHE/ECL
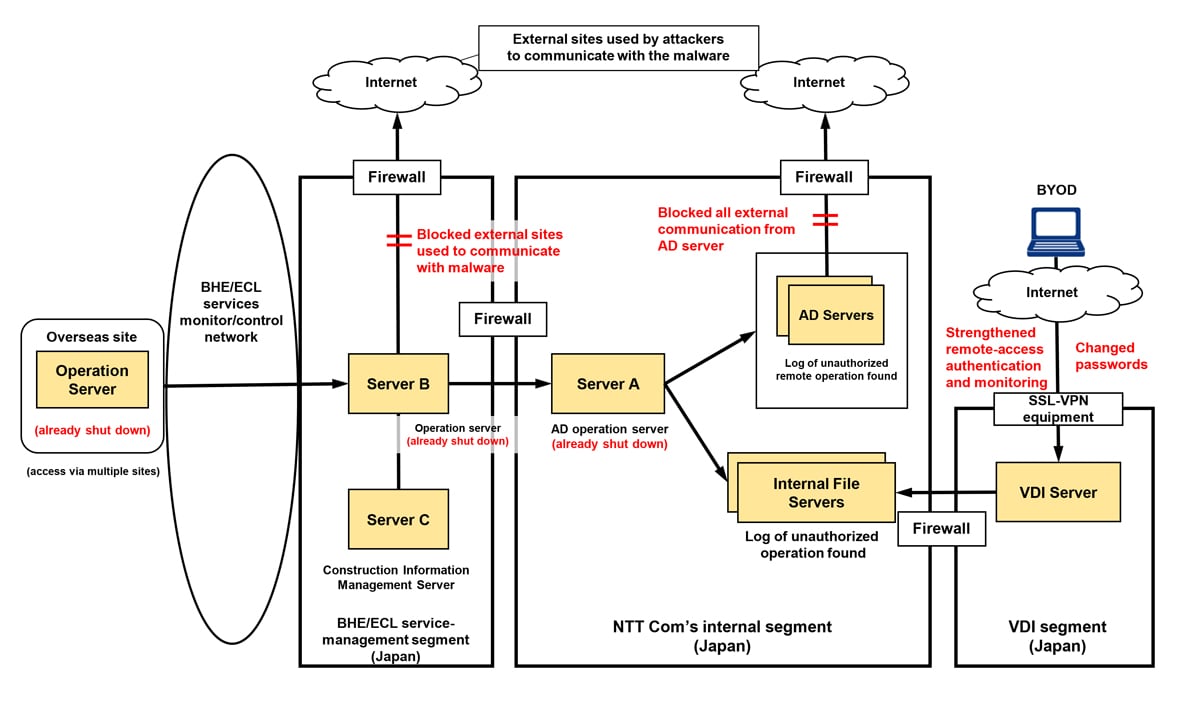
Based on a log showing unauthorized access to construction information management server (“Server C” in diagram) used for BHE and ECL Option Services, the company conducted a forensic investigation3 of its Active Directory4 operation server (“Server A” in diagram), operation server for BHE/ECL service management (“Server B” in diagram) and Server C used for BHE/ECL service management. As a result, it was determined on June 19 that service-related construction information on 83 clients—separate from the 621 clients announced on May 28—may have been leaked from the construction information management server in the service management segment in Japan, which is isolated from the BHE/ECL client network segment. NTT Com has started contacting these additional 83 clients.
All of the affected clients outside of Japan who were or are using these services in Japan have been notified individually since the last announcement on May 28.
There has been no effect on service availability or the quality of cloud services, including services provided outside of Japan. Information on consumer customers was not affected.
2. Unauthorized access to internal file servers
Regarding NTT Com’s investigation into unauthorized remote operation of the company’s internal servers, as announced on May 28, further investigation concluded on June 2 that information in some internal files was possibly leaked. NTT Com has contacted clients in Japan that were possibly affected. No clients outside of Japan were affected. Information on consumer customers was not affected.
It was newly discovered on May 26 that certain internal file servers were possibly accessed via the virtual desktop infrastructure (VDI)5 server and that internal files may have been browsed. On the same day, after identifying that a personal bring-your-own device (BYOD)6 had been used remotely to gain unauthorized access, NTT Com immediately shut down the remote access environment for all such devices as well as devices dedicated to thin clients, and changed the passwords for all employees. In addition, NTT Com strengthened remote-access authentication and monitoring. Thereafter, no unauthorized use of employee accounts has been identified.
Although extra time was required to identify which information the attackers may have browsed because a legitimate account and password were possibly stolen, the forensic investigation and analysis of the access history of internal file servers has now revealed that 188 clients may have been affected. NTT Com is in the process of contacting all of these clients. No clients outside of Japan were affected. Information on consumer customers was not affected.
Diagram of the event
3. Future measures
NTT Com is introducing measures to quickly recover any server in the event of a spoofing attack, which required extra time to assess in the recent case. These include the deployment of User and Entity Behavior Analytics (UEBA),7 which speeds up detection by visualizing the behavior of an attacker who uses a legitimate account and password after breaching the server. Also, NTT Com is working to prevent any recurrence by introducing Endpoint Detection and Response8 technology to strengthen endpoint security and by accelerating security measures based on a Zero Trust policy.9
In addition to reviewing the structure of information management in internal file servers, service quality is being further improved by strengthening the role of the Red Team10 in verifying security-measure effectiveness, and by continuously implementing Threat-Led Penetration Testing (TLPT)11 for internal IT and operational technologies.12
Hereafter, any additional relevant information will be disclosed as required, excluding information on individual clients to protect their confidentiality.
Background
Summary of press release issued in Japanese on May 28
NTT Com’s department in charge of internal systems detected unauthorized remote operation of the company’s Active Directory (AD) server in a log on May 7. On the same day, the department quickly shut down the AD operation server (“Server A”) that was used by the attacker as a springboard server to enable remote operation. NTT Com immediately launched an investigation, based on which the operation server (“Server B”) for BHE/ECL service management, from which Server A was accessed, was immediately shut down and all external communication from the AD server of the internal segment was blocked. Communication with external sites that the attacker used to communicate with malware was also blocked.
After analyzing the access logs of the internal servers, it was discovered on May 11 that some information may have been leaked. Since the route used for unauthorized access was via Server B, a forensic investigation of Server B was conducted. The results showed evidence of unauthorized access to the construction information management server (“Server C”) used for BHE/ECL service management. After analyzing Server C’s access log, it was determined on May 13 that some files stored on Server C may have been leaked.
As a result of investigating the attackers’ route, it was found that the intrusion reached Server B in Japan following unauthorized access to a site in Singapore that is connected to BHE/ECL service management.
In summary, it has been determined that service-related construction information pertaining to 621 clients may have been leaked from the construction information management server (Server C) in the service management segment in Japan, which is isolated from the BHE/ECL client network segment. Going forward, security measures designed for the latest attack methods will be deployed at facilities that are being transitioned to new services, until they are physically removed. Also, every effort will be taken to block all communication channels that become unnecessary whenever clients stop using them.
1 Biz Hosting Enterprise is a cloud service for enterprise ICT infrastructure. With the exception of certain optional services, it was terminated in March 2018.
2 ECL Option Services include managed option, collocation interconnectivity, and provisioning support
3 Forensic investigation (digital forensics) is a technology and method to investigate electronic trails, such as access logs left in personal computers, communication devices and other electronic devices, related cyberattacks and similar crimes. It is also used to preserve evidence and analyze possible damage.
4 Active Directory is a feature that Windows Server provides to manage Windows PC features and user information.
5 Virtual Desktop Infrastructure (VDI) is a mechanism that virtualizes the desktop environment, aggregates the PC desktop environment on the server, and runs it on the server.
6 Bring Your Own Device (BYOD) is a policy for using employees’ private devices for business.
7 User and Entity Behavior Analytics (UEBA) is a technology that analyzes user behavior for early-stage detection of risks.
8 Endpoint Detection and Response (EDR) is a technology that monitors and responds to suspicious behavior on a PC or server (endpoint).
9 Zero Trust is a concept of information security that assumes nothing inside or outside a company can be trusted, instead of protecting only boundaries under the assumption that within the company is safe.
10 Red Team is an independent team within a company that executes pseudo attacks to evaluate and propose security measures.
11 Threat-Led Penetration Testing (TLPT) are pseudo attacks based on fixed scenarios for evaluating the status of security measures.
12 Operational technologies include control and/or monitoring of industrial equipment that is used to optimize systems for essential infrastructure, such as electrical power grids.
About NTT Communications
NTT Communications solves the world’s technology challenges by helping enterprises overcome complexity and risk in their ICT environments with managed IT infrastructure solutions. These solutions are backed by our worldwide infrastructure, including industry leading, global tier-1 public and private networks reaching over 190 countries/regions, and more than 500,000m2 of the world’s most advanced data center facilities. Our global professional services teams provide consultation and architecture for the resiliency and security required for your business success, and our scale and global capabilities in technology world are unsurpassed. Combined with NTT Ltd., NTT Data, and NTT DOCOMO, we are NTT Group.
www.ntt.com | Twitter@NTT Com | Facebook@NTT Com | LinkedIn@NTT Com
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!