Reason # 1
A digital native startup SaaS company has just deployed a new web application in Google Cloud that tracks the sleeping habits of people who suffer from sleep disorders in order to give them a better quality sleep experience. They are a small start-up with a humble budget and don’t want to be locked into any long term commitments. They want automated protection against known critical web application security risk, but don’t have a large security team.
From our partners:
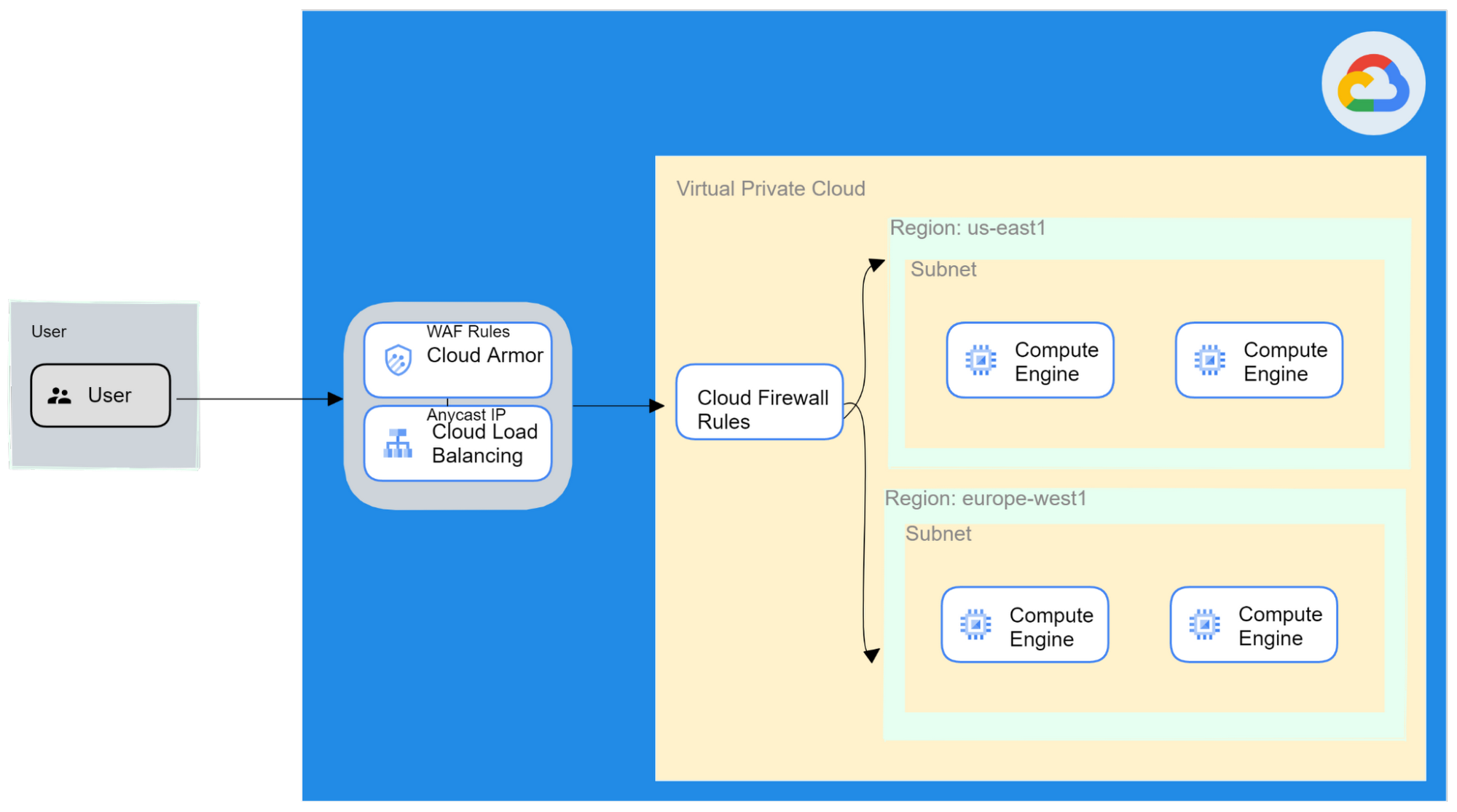
Figure 1
- Preview mode – Cloud Armor offers a preview mode so that the outcome of rules can be viewed before applying and putting into production.
- Saves time – Cloud Armor has preconfigured WAF rules that the company can leverage so they don’t have to spend much time creating custom rules and the small team can spend time working on other important projects.
- Pay as you go –In the Cloud Armor standard tier you can pay as you go.
Digital native startups can benefit from Cloud Armor because it saves time, has a pay as you go model and is flexible.
Reason # 2
A large financial institution is running their mobile and online banking app on Google Cloud. Due to certain government regulations certain parts of their app must be on-premise. They were recently a victim of a brute force attack where a bad actor was able to gain access to a high privilege account. The actor also tried to use a SQL injection attack to gain access to the applications backend to get sensitive customer information.
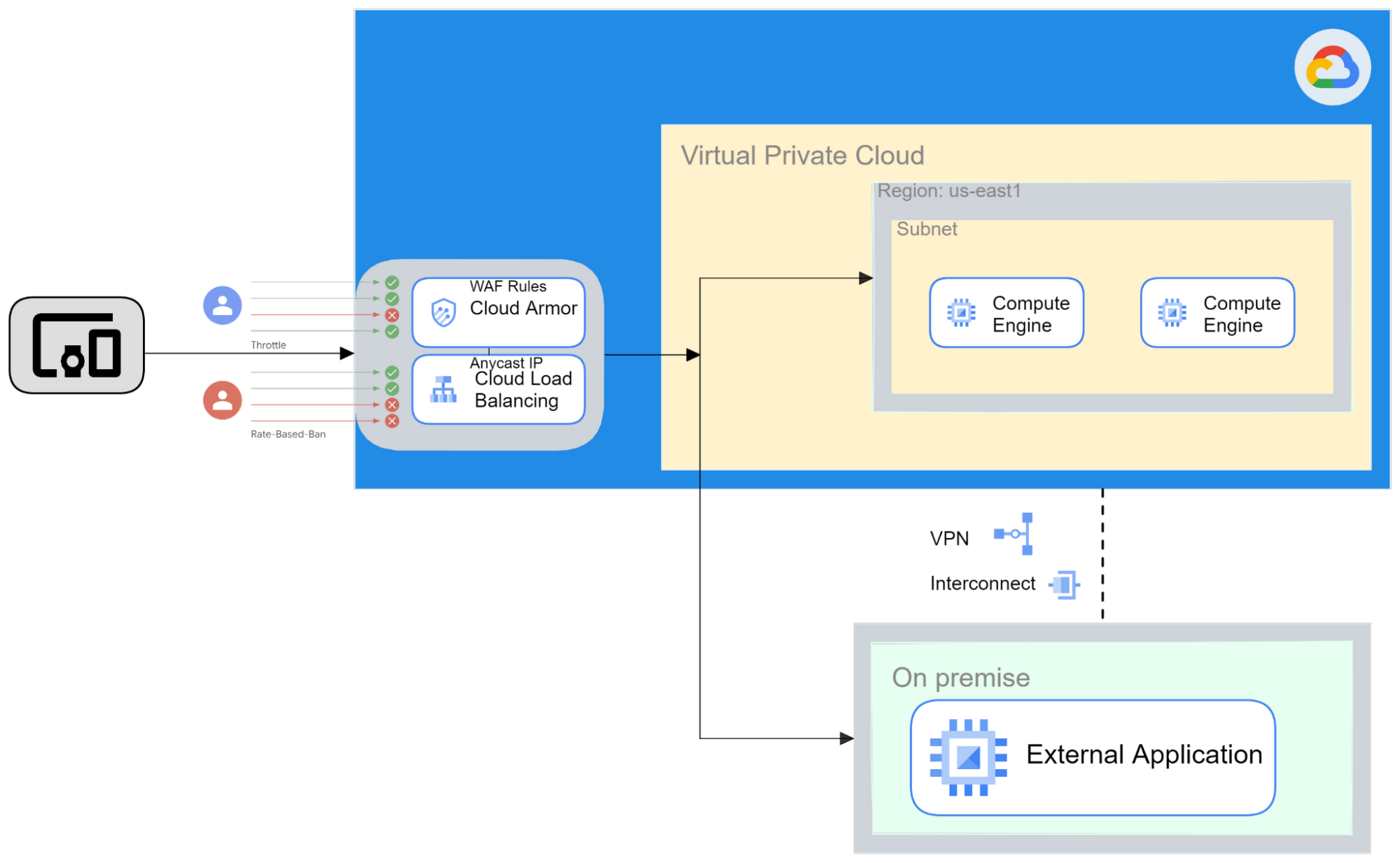
Figure 2
- Preparing for the unknown – Cloud Armor has adaptive protection in both standard and managed protection plus tier. The standard tier gives the alerting only functionality. The managed protection plus tier has more features including generating a signature describing the potential attack and generating a custom Google Cloud Armor WAF rule to block the signature.
- On-premise protection – Cloud Armor can be used in Google Cloud and on-premise to help defend from DDoS and to enforce Layer 7 security policies.
- Rate limiting – Cloud Armor uses rate-based rules to help you protect your applications from a large volume of requests which can defend against brute force attacks.
- SQL Injection Protection built in – Cloud Armor provides pre configured rules based on industry standard and OWASP Top 10 to mitigate against common web-application vulnerabilities.
- Threat Intelligence – Allows you to block traffic based on threat intelligence data in the following categories: Tor exit nodes, Known malicious IP addresses, Search engines and Public cloud IP address ranges.
Cloud Armor can keep you protected on-prem or in the cloud. You can also take advantage of Cloud Armor’s rate limiting feature to help protect against brute force attacks. Out-of-the-box rules based on industry standards give you a piece of mind and help protect your applications from common vulnerabilities.
Reason # 3
A home goods company has a substantial online presence. They have noticed an increased number of requests on the customer login page. They want to evaluate these incoming requests to help validate the requests, understand traffic patterns and to mitigate the potential for bot attacks. They also want to be able to collect and analyze the data from these requests.
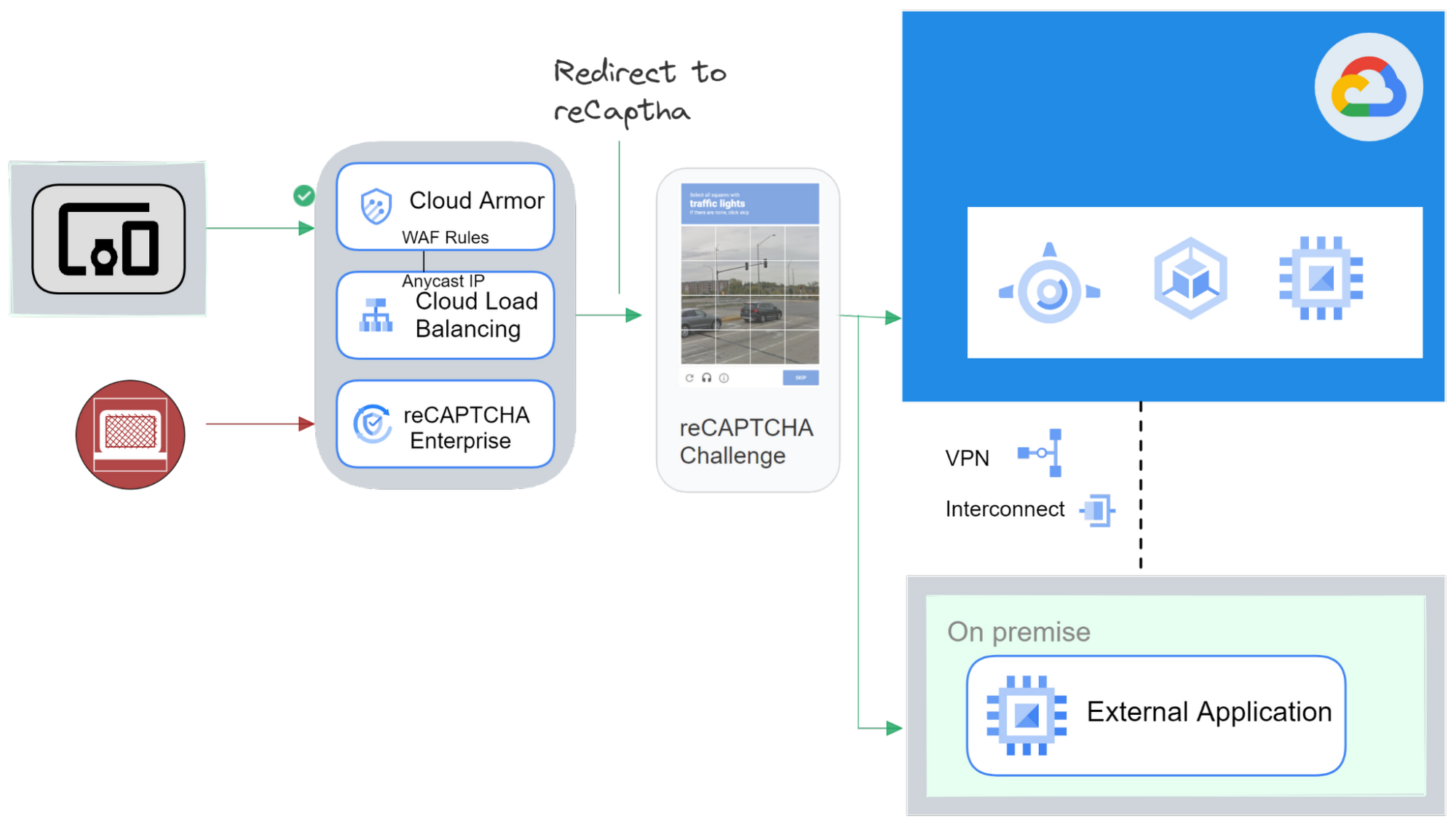
Figure 3
- ReCaptcha Enterprise Integration – Cloud Armor can integrate with reCAPTCHA Enterprise to help evaluate and act on incoming requests that might be from automated bots.
- Per-Request Logging – Via Cloud logging you can view every request evaluated by a Google Cloud Armor security policy and the outcome or action taken. If you have, Security Command Center enabled Cloud Armor is automatically integrated to provide findings.
- Request redirection – Cloud Armor can evaluate reCAPTCHA Enterprise tokens that are attached with the request and redirect requests to a different endpoint. ​​Cloud Armor can redirect requests by sending an HTTP 302 response to the client.
Utilizing Cloud Armor ReCaptcha Enterprise and Cloud Logging you can improve your application’s security posture by increasing security to protect against common bot attacks.
Reason # 4
An online training company has launched a global campaign. As a result they have seen an increase in traffic from all parts of the world. They have noticed that the performance of their website is slower than usual due to the load on the backend. Also they have noticed an increase in billing, primarily due to the increased requests to the backend. Their current website has both static and dynamic elements. They need to find a way to reduce latency, cut costs and still protect their content and web site.
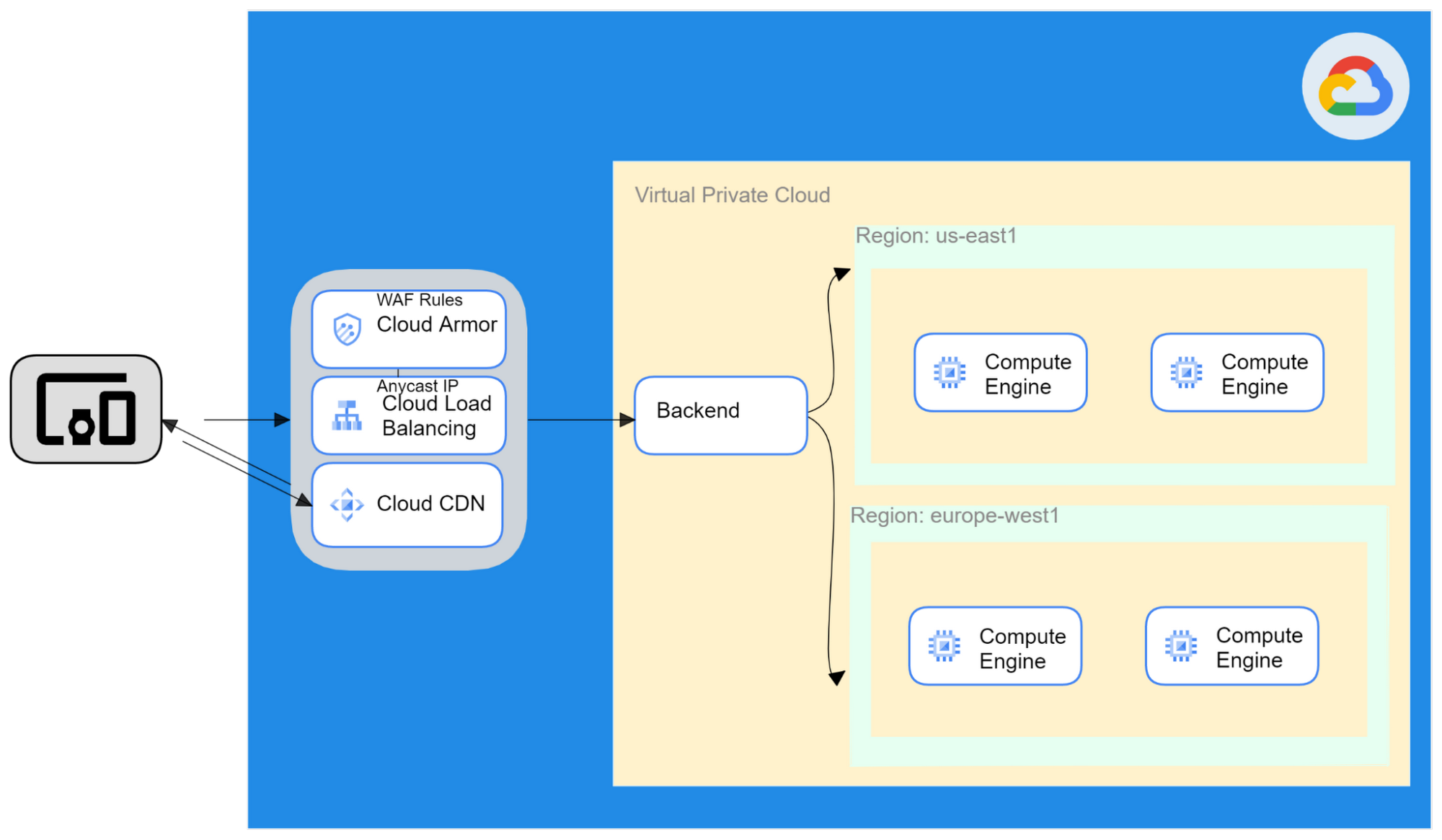
Figure 4
- CDN Integration –Cloud CDN runs on Google’s globally distributed edge points to reduce network latency by caching content closer to users depending on their location. Using Cloud CDN will increase speeds by caching static content at the edge and serve content from the CDN instead of hitting the backend. Cloud Armor allows users to customize the behavior of the edge of Google’s network.
- Block specific GEO IPs – Use edge rules
origin.ipandorigin.region_codeto restrict access to your caches stores.
Using Cloud Armor and Cloud CDN can increase the speed of your applications while protecting against malicious threats.
Making the choice
The final decision to use Cloud Armor would ultimately depend on the situation of the enterprise. In any case full considerations should be made for not only the technical aspects but also the business requirements. In addition to the benefits stated above, Cloud Armor has some documented performance results in which it performed well against a layer 7 DDoS attack at 46 million requests per second.
To learn more about Cloud Armor check out the following:
- Blog: How Google Cloud blocked the largest Layer 7 DDoS attack at 46 million rps
- Blog: Introducing new Cloud Armor features including rate limiting, adaptive protection, and bot defense
- Blog: Announcing general availability of Cloud Armor’s new edge security policies, and support for proxy load balancers
- Practice The Labs: Google Skills Boost
- YouTube: How you can protect your websites and applications with Google Cloud Armor
- YouTube: DDoS defense blow by blow
By: Emanuel Burgess (Developer Relations Engineer) and Ammett Williams (Developer Relations Engineer)
Source: Google Cloud Blog
For enquiries, product placements, sponsorships, and collaborations, connect with us at [email protected]. We'd love to hear from you!
Our humans need coffee too! Your support is highly appreciated, thank you!